A new variant of StopCrypt ransomware (aka STOP) was spotted in the wild, employing a multi-stage execution process that involves shellcodes to evade security tools.
StopCrypt, also known as STOP Djvu, is the most widely distributed ransomware in existence that you rarely hear about.
While you constantly hear how big some ransomware operations are, such as LockBit, BlackCat, and Clop, you rarely hear security researchers discussing STOP.
That is because this ransomware operation does not typically target businesses but rather consumers, hoping to generate tens of thousands small $400 to $1,000 ransom payments instead of one large multi-million-dollar demand.
The ransomware is commonly distributed via malvertising and shady sites distributing adware bundles disguised as free software, game cheats and software cracks.
However, when these programs are installed, the users become infected with a variety of malware, including password stealing trojans and STOP ransomware.
This leads infected users to desperately reach out to security researchers, ransomware experts, and our 807-page STOP ransomware forum topic to try and receive help.
Since its original release in 2018, the ransomware encryptor has not changed much, with new versions mostly released to fix critical problems.
For this reason, when a new STOP version is released, it bears watching due to the large number of people who will be affected by it.
New multi-staged execution
SonicWall's threat research team has uncovered a new variant of the STOP ransomware (they call it StopCrypt) in the wild that now utilizes a multi-stage execution mechanism.
Initially, the malware loads a seemingly unrelated DLL file (msim32.dll), possibly as a diversion. It also implements a series of long time-delaying loops that may help bypass time-related security measures.
Next, it uses dynamically constructed API calls on the stack to allocate the necessary memory space for read/write and execution permissions, making detection harder.
StopCrypt uses API calls for various operations, including taking snapshots of running processes to understand the environment in which it's operating.
The next stage involves process hollowing, where StopCrypt hijacks legitimate processes and injects its payload for discreet execution in memory. This is done through a series of carefully orchestrated API calls that manipulate process memory and control flow.
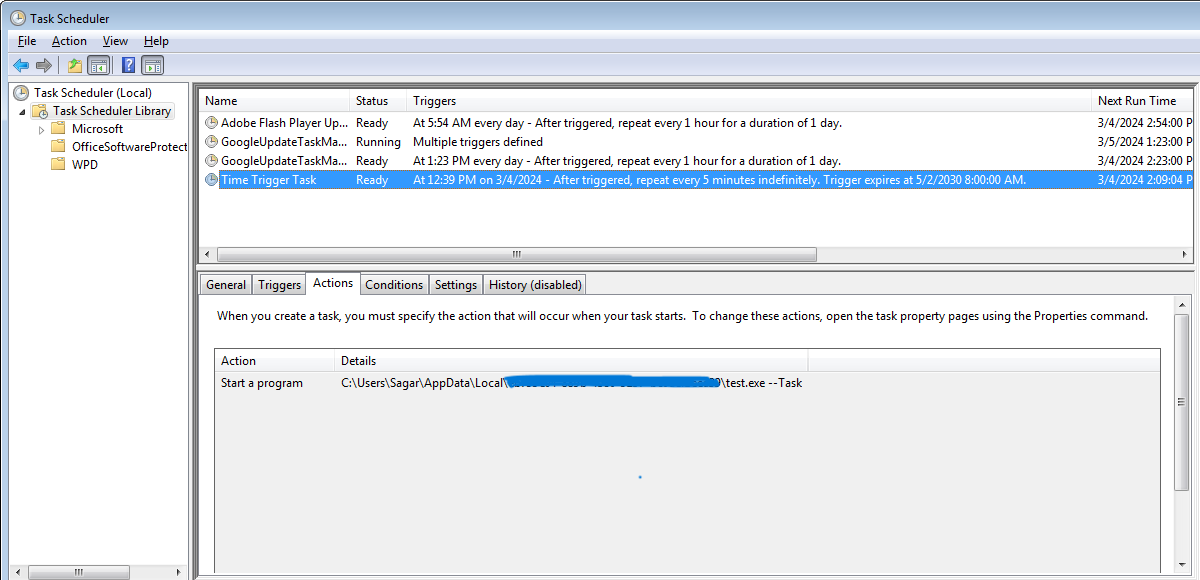
Once the final payload is executed, a series of actions takes place to secure persistence for the ransomware, modify access control lists (ACLs) to deny users permission to delete important malware files and directories, and a scheduled task is created to execute the payload every five minutes.
Files are encrypted and a ".msjd" extension is appended to their new names. However, it should be noted that there are hundreds of extensions related to the STOP ransomware as they change them often.
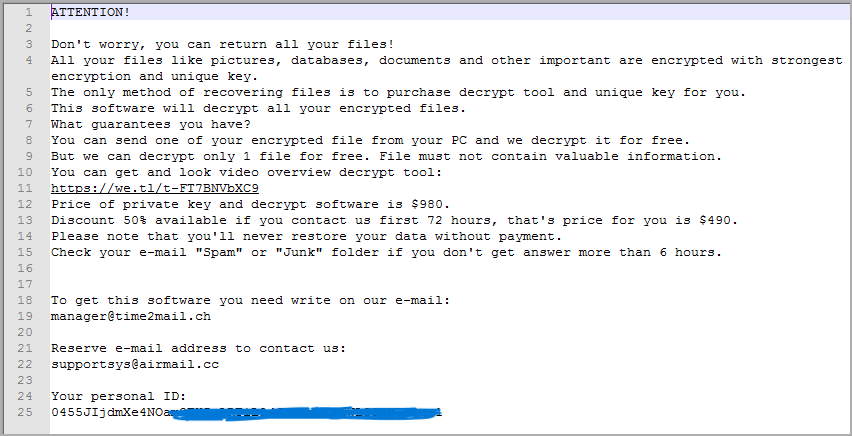
Finally, a ransom note named "_readme.txt" is created in every impacted folder, giving victims instructions on paying the ransom for data retrieval.
The evolution of StopCrypt into a more stealthy and powerful threat underscores a troubling trend in cybercrime.
Though StopCrypt's monetary demands aren't high and its operators do not perform data theft, the damage it can cause to many people could be significant.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.