The Microsoft consumer signing key stolen by Storm-0558 Chinese hackers provided them with access far beyond the Exchange Online and Outlook.com accounts that Redmond said were compromised, according to Wiz security researchers.
Redmond revealed on July 12th that the attackers had breached the Exchange Online and Azure Active Directory (AD) accounts of around two dozen organizations. This was achieved by exploiting a now-patched zero-day validation issue in the GetAccessTokenForResourceAPI, allowing them to forge signed access tokens and impersonate accounts within the targeted organizations.
The affected entities included government agencies in the U.S. and Western European regions, with the U.S. State and Commerce Departments among them.
On Friday, Wiz security researcher Shir Tamari said that the impact extended to all Azure AD applications operating with Microsoft's OpenID v2.0. This was due to the stolen key's ability to sign any OpenID v2.0 access token for personal accounts (e.g., Xbox, Skype) and multi-tenant AAD apps.
Microsoft clarified after the publishing of this article that it only impacted those that accepted personal accounts and had the validation error.
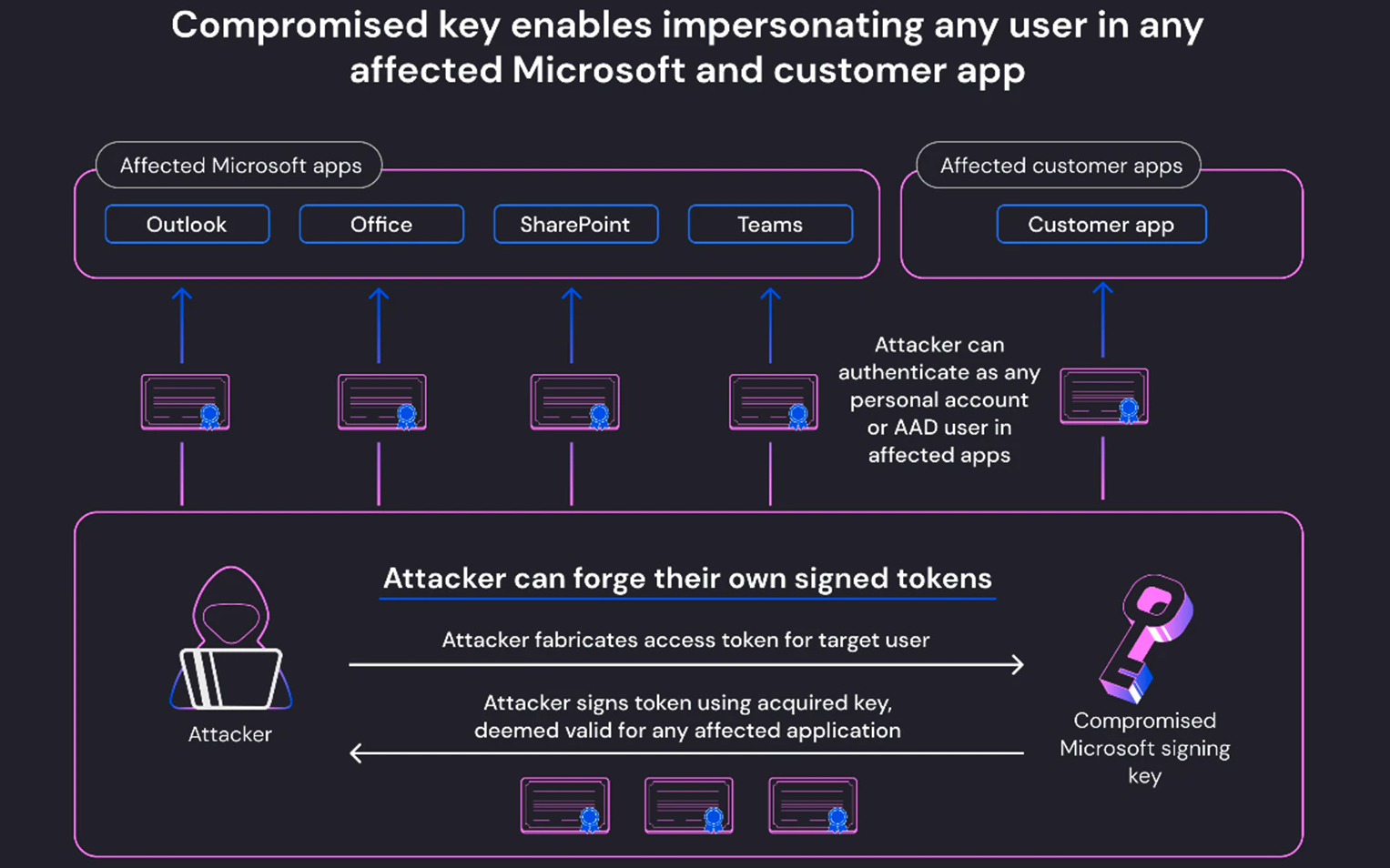
While Microsoft said that only Exchange Online and Outlook were impacted, Wiz says the threat actors could use the compromised Microsoft consumer signing key to impersonate any account within any impacted customer or cloud-based Microsoft application.
"This includes managed Microsoft applications, such as Outlook, SharePoint, OneDrive, and Teams, as well as customers' applications that support Microsoft Account authentication, including those who allow the 'Login with Microsoft' functionality," Tamari said.
"Everything in the world of Microsoft leverages Azure Active Directory auth tokens for access," Wiz CTO and Cofounder Ami Luttwak also told BleepingComputer.
"An attacker with an AAD signing key is the most powerful attacker you can imagine, because they can access almost any app – as any user. This is the ultimate cyber intelligence' shape shifter' superpower."
In response to the security breach, Microsoft revoked all valid MSA signing keys to ensure that the threat actors didn't have access to other compromised keys.
This measure also thwarted any attempts to generate new access tokens. Further, Redmond relocated the newly generated access tokens to the key store for the company's enterprise systems.
After invalidating the stolen signing key, Microsoft found no further evidence suggesting additional unauthorized access to its customers' accounts using the same auth token forging technique.
Additionally, Microsoft reported observing a shift in Storm-0558 tactics, showing that the threat actors no longer had access to any signing keys.
Last but not least, the company revealed last Friday that it still doesn't know how the Chinese hackers stole the Microsoft consumer signing key. However, after pressure from CISA, they agreed to expand access to cloud logging data for free to help defenders detect similar breach attempts in the future.
Before this, these logging capabilities were only available to Microsoft customers who paid for Purview Audit (Premium) logging license. As a result, Microsoft faced considerable criticism for impeding organizations from promptly detecting Storm-0558 attacks.
"At this stage, it is hard to determine the full extent of the incident as there were millions of applications that were potentially vulnerable, both Microsoft apps and customer apps, and the majority of them lack the sufficient logs to determine if they were compromised or not," Tamari concluded today.
Update 7/22/23: Updated article with clarifications from Microsoft.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.