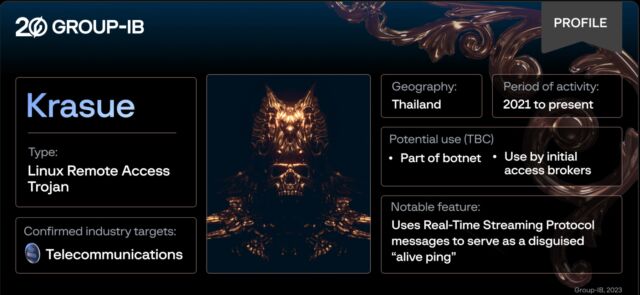
Krasue infects telecom firms in Thailand using techniques for staying under the radar.
Stealthy and multifunctional Linux malware that has been infecting telecommunications companies went largely unnoticed for two years until being documented for the first time by researchers on Thursday.
Researchers from security firm Group-IB have named the remote access trojan “Krasue,” after a nocturnal spirit depicted in Southeast Asian folklore “floating in mid-air, with no torso, just her intestines hanging from below her chin.” The researchers chose the name because evidence to date shows it almost exclusively targets victims in Thailand and “poses a severe risk to critical systems and sensitive data given that it is able to grant attackers remote access to the targeted network.
According to the researchers:
- Krasue is a Linux Remote Access Trojan that has been active since 20 and predominantly targets organizations in Thailand.
- Group-IB can confirm that telecommunications companies were targeted by Krasue.
- The malware contains several embedded rootkits to support different Linux kernel versions.
- Krasue’s rootkit is drawn from public sources (3 open-source Linux Kernel Module rootkits), as is the case with many Linux rootkits.
- The rootkit can hook the `kill()` syscall, network-related functions, and file listing operations in order to hide its activities and evade detection.
- Notably, Krasue uses RTSP (Real-Time Streaming Protocol) messages to serve as a disguised “alive ping,” a tactic rarely seen in the wild.
- This Linux malware, Group-IB researchers presume, is deployed during the later stages of an attack chain in order to maintain access to a victim host.
- Krasue is likely to either be deployed as part of a botnet or sold by initial access brokers to other cybercriminals.
- Group-IB researchers believe that Krasue was created by the same author as the XorDdos Linux Trojan, documented by Microsoft in a March 2022 blog post, or someone who had access to the latter’s source code.
During the initialization phase, the rootkit conceals its own presence. It then proceeds to hook the `kill()` syscall, network-related functions, and file listing operations, thereby obscuring its activities and evading detection.
The researchers have so far been unable to determine precisely how Krasue gets installed. Possible infection vectors include through vulnerability exploitation, credential-stealing or -guessing attacks, or by unwittingly being installed as trojan stashed in an installation file or update masquerading as legitimate software.
The three open source rootkit packages incorporated into Krasue are:
- Diamorphine
- Suterusu
- Rooty
An image showing salient research points of Krasue.
Rootkits are a type of malware that hides directories, files, processes, and other evidence of its presence to the operating system it’s installed on.
By hooking legitimate Linux processes, the malware is able to suspend them at select points and interject functions that conceal its presence.
Specifically, it hides files and directories beginning with the names “auwd” and “vmware_helper” from directory listings and hides ports 52695 and 52699, where communications to attacker-controlled servers occur. Intercepting the kill() syscall also allows the trojan to survive Linux commands attempting to abort the program and shut it down.
In a post, Group-IB Malware Analyst Sharmine Low wrote:
Krasue creates a child process and establishes a UDP socket server on port 52699. The purpose of this server is to wait for commands from a command and control (C2) server. For C2 communication, the traffic undergoes AES-CBC encryption using a static key: `22 32 A4 98 A1 4F 2E 44 CF 55 93 B7 91 59 BE A6`. The author used the tiny-AES library. The Trojan handles C2 commands as shown below:
| C2 command | Description |
| ping | Reply with `pong` |
| master | Set the master upstream C2 |
| info |
Get information about the malware: main pid, child pid, and its status such as
root: gained root permissions god: process is unable to be killed hidden: process is hidden module: rootkit is loaded |
| restart | Restart child process |
| respawn | Restart main process |
| god die | Kill itself |
| shell | Run shell commands with `/bin/sh` |
Krasue is able to designate a communicating IP as its master C2. It constantly sends `DESCRIBE rtsp://server/media[.]mp4 RTSP/1.0\r\nCSeq: 2\r\n\r\n` in the form of an alive ping to its master C2, in which it returns a blank space character `\x20`. `DESCRIBE` is a method used in Real Time Streaming Protocol (RTSP), a network protocol designed for controlling the delivery of real-time media streams over IP networks. It is often used in applications such as video streaming and video surveillance systems.
We found a total of 9 hardcoded IP addresses for its master C2. Krasue will always attempt to connect to the internal addresses initially. Only after multiple non-replies and trying to connect to server after server, it will attempt to connect 128[.]199[.]226[.]11 at port 554, which is a port commonly used for RTSP. We suspect that the program is attempting to masquerade and camouflage its network communication, and this is notable because while malware developers typically make a concerted effort to disguise network traffic, using RTSP for this purpose is highly uncommon.
The IP addresses are:
- 172[.]19[.]37[.]145: 52699
- 172[.]19[.]37[.]159: 52699
- 172[.]19[.]37[.]169: 52699
- 172[.]19[.]37[.]170: 52699
- 172[.]19[.]37[.]171: 52699
- 172[.]19[.]37[.]172: 52699
- 172[.]19[.]37[.]173: 52699
- 172[.]19[.]37[.]175: 52699
- 128[.]199[.]226[.]11: 554
As “internal” addresses, the first 8 IPs are reserved for devices inside the local network hosting the infected Linux device. Low said it’s not clear why there are so many such addresses. One possibility is that they’re meant to be decoys that stymie detection by connecting to external addresses only after running for a set period of time.
“The second possibility is that the cybercriminals had access to the Remote Access Trojan from within the victim’s infrastructure since the malware does not have reverse proxy capabilities,” Low wrote. “The hackers may have gained access to the victim’s infrastructure and created tunnels within the network. This would also suggest that Krasue is typically deployed during the later stages of an attack chain in order to maintain remote access to an infected network.”
Besides the rootkit functions, Krasue features an installation file that’s shielded inside a UPX, a so-called packer that provides a cryptographic wrapper around the main executable that can stymie detection by anti-virus software. The Group-IB post provides indicators of compromise and digital characteristics for detecting infected systems.
- phen0men4
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.