A financially motivated threat actor is hacking telecommunication service providers and business process outsourcing firms, actively reversing defensive mitigations applied when the breach is detected.
The campaign was spotted by Crowdstrike, who says the attacks started in June 2022 and are still ongoing, with the security researchers able to identify five distinct intrusions.
The attacks have been attributed with low confidence to hackers tracked as 'Scattered Spider,' who demonstrate persistence in maintaining access, reversing mitigations, evading detection, and pivoting to other valid targets if thwarted.
The campaign's ultimate goal is to breach telecom network systems, access subscriber information, and conduct operations such as SIM swapping.
.png)
Five intrusion events attributed to Scattered Spider (Crowdstrike)
Campaign details
The threat actors gain initial access to corporate networks using a variety of social engineering tactics.
These tactics include calling employees and impersonating IT staff to harvest credentials or using Telegram and SMS messages to redirect targets to custom-crafted phishing sites that feature the company's logo.
If MFA protected the target accounts, the attackers either employed push-notification MFA fatigue tactics or engaged in social engineering to get the codes from the victims.
In one case, the adversaries exploited CVE-2021-35464, a flaw in the ForgeRock AM server, to run code and elevate their privileges on an AWS instance.
"Leveraging AWS Instance Roles to assume or elevate privileges from the Apache Tomcat user, the adversary would request and assume permissions of an instance role using a compromised AWS token," explains Crowdstrike.
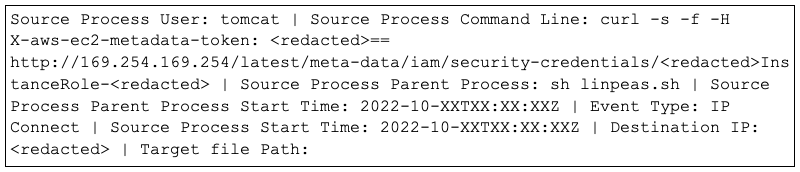
Curl command for privilege escalation in AWS using the LinPEAS tool (Crowdstrike)
Once the hackers gain access to a system, they attempt to add their own devices to the list of trusted MFA (multi-factor authentication) devices using the compromised user account.
Crowdstrike noticed the hackers using the following utilities and remote monitoring and management (RMM) tools in their campaigns:
- AnyDesk
- BeAnywhere
- Domotz
- DWservice
- Fixme.it
- Fleetdeck.io
- Itarian Endpoint Manager
- Level.io
- Logmein
- ManageEngine
- N-Able
- Pulseway
- Rport
- Rsocx
- ScreenConnect
- SSH RevShell and RDP Tunnelling via SSH
- Teamviewer
- TrendMicro Basecamp
- Sorillus
- ZeroTier
Many of the above are legitimate software commonly found in corporate networks and hence unlikely to generate alerts on security tools.
In intrusions observed by Crowdstrike, the adversaries were relentless in their attempts to maintain access to a breached network, even after being detected.
"In multiple investigations, CrowdStrike observed the adversary become even more active, setting up additional persistence mechanisms, i.e. VPN access and/or multiple RMM tools, if mitigation measures are slowly implemented," warned CrowdStrike.
"And in multiple instances, the adversary reverted some of the mitigation measures by re-enabling accounts previously disabled by the victim organization."
In all intrusions observed by Crowdstrike, the adversaries used various VPNs and ISPs to access the victimized organization's Google Workspace environment.
To move laterally, the threat actors extracted various types of reconnaissance information, downloaded user lists from breached tenants, abused WMI, and performed SSH tunneling and domain replication.
Crowdstrike has shared an extensive list of indicators of compromise (IoCs) for this activity at the bottom of the report, which is vital for defenders to note as the threat actor uses the same tools and IP addresses across different intrusions.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.