LastPass suffered two data breaches in a span of 3 months. The first hack occurred in August, while the 2nd one happened sometime later.
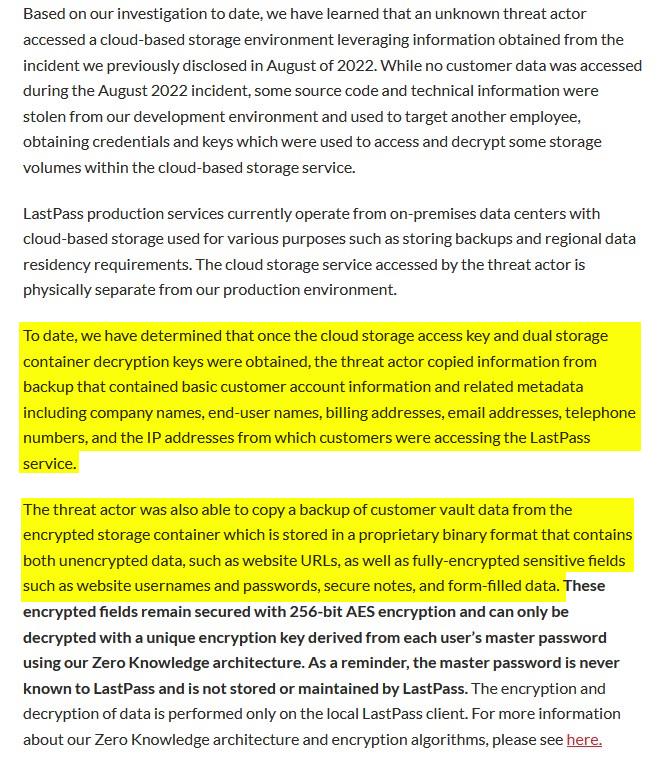
Martin's write-up explains what LastPass' statement had to say about the recent security incident. The situation could actually be a lot worse. Many security researchers have blasted the company for misleading its users about the stolen password vaults.
Wladimir Palant, the creator of AdBlock Plus was among those who slammed the statement. He says in an article on his blog, that by releasing the update right before the holiday season, LastPass wanted to make sure the news flew under the radar.
That's a sneaky move.
Palant called the statement as "full of omissions, half-truths and outright lies", and that the company had tried to draw focus to the 2 hacks as two separate incidents, to cover up the fact that they are related to each other. As a matter of fact, LastPass has not revealed when the 2nd attack took place, and Palant says that this could have happened in September itself. He also points out that the hackers could have collected all IPs associated with a user, website URLs which were unencrypted, to profile their activity.
Here's the primary issue, LastPass claims that its Zero Knowledge architecture and 256-bit encryption will protect user data from being accessed by hackers, because "it would take millions of years to guess your master password using generally-available password-cracking technology."
This claim has been criticized by Palant, and Jeffrey Goldberg at 1Password. They say that it may take a long time for hackers to guess the master password, only if LastPass had forced its 12-character minimum password requirement. While the rule came into effect in 2018, it was only mandatory for new users (default setting), existing users were never asked to change their password. So, thousands of users could actually been using a weaker password.
This is really important, because most people would not be using a master password generated by a password generator, and this greatly increases the risk of their vault being breached. The fact that LastPass only hashes passwords with 100,000 iterations (PBKDF2) was also criticized by the researchers. The company had been using 5,000 iterations as the default value, which is incredibly low. Goldberg says it may cost just $100 for a hacker to run ten billion guesses to crack the passwords hashed with PBKDF2 (100,000 iterations).
Jeremi Gosney, a Senior Engineer at Yahoo, called "LastPass's claim of "zero knowledge" is a bald-faced lie." He also says that users assume that their vault is stored in an encrypted database which is protected, but this is not the case, and that LastPass stores your vault as a plaintext file, and that only some of the fields are encrypted.
When I wrote about the hack, I speculated that the only customer information that were stolen would be the things that you'd find on an invoice, because that's how LastPass had described the incident. I was quite shocked by the disclosure from the company when they admitted the threat actors gained access to users' password vaults and other data. I know people who were using it on a daily basis, and I've spoken to them about migrating away from the service. The Verge observes that this is in fact the seventh time that LastPass has been breached.
Let's face the truth, such hacks could happen to any cloud based password manager. Even though every company employs its own security protocols, no service is 100% foolproof or hacker proof. In the end, the quality of the security system, and how prepared they are to handle such threats make all the difference.
In this case, there is no doubt that LastPass made an absolute disaster of managing the post-hack process. Why did they hide the nature of the original attack? Why not acknowledge that the hackers managed to access crucial employee data, and that it could lead to further repercussions? Did they end their security audit prematurely or not conduct a thorough scrutiny? Why didn't they disclose the fact that user's vaults could have been stolen earlier?
The decent thing to do, the professional thing to do, would have been to admit their mistake the moment they realized their servers had been breached. They should have warned users as soon as possible to change their passwords, to protect their online identities, bank accounts, etc. Users may not have been pleased to hear the news, but they would have applauded the responsibility and effort to notify them.
Instead, all the users got was a vague statement that possibly arrived months later, and casually admitted that LastPass had been hacked, and that users could potentially lose access to their priceless accounts, and that the company wasn't to be blamed for this. I'm guessing they took their time while working on the legal side of things, to find some loopholes or safety net to protect themselves from potential lawsuits.
I got the "Update on Recent Security Incident" mail from LastPass on December 28th, a whole week after they originally announced it on their blog. I deleted my primary account a couple of years ago, but I never had important passwords saved there, I just had some test accounts there, but they contained fake information. But if I were a regular user, I'd have been upset by the delay in notifying me about the risks, and the awful way the issue has been handled.
If anything, these shenanigans have only made it worse, and it will lose the trust of your users. I don't think that LastPass can recover from this mishap, and it's time to ditch it for your sanity, and the security of your accounts.
If you want a free alternative, there are two good options to consider, and both support importing your passwords. Speaking of which, I strongly recommend changing all of your passwords (or at least weak ones, those without 2FA) that were saved in LastPass.
Bitwarden is a cloud-based password manager that is available across all major platforms (Windows, macOS, Linux, Android and iOS). It even has browser extensions for Firefox and Chrome. Bitwarden has an optional premium subscription that costs $12 a year, that's not a typo it actually costs just $1/month, and it gives you some extra features like YubiKey and FIDO2 (for 2FA), 1GB storage space for file attachments, emergency access, etc. Don't want to pay for it? That's fine, the free version is just as good, and you can even self-host it on your own server if you're tech-savvy.
KeePass is the other alternative that I recommend, it's an open-source, offline password manager available for Windows, Linux and macOS. There are many unofficial ports too, the most notable one for desktops is KeePassXC, it has a nice UI, some additional features, and a browser extension for Firefox and Chrome, which is useful for autofill.
There are quite a few KeePass forks available for Android and iOS that you can use on your phone, some of these mobile apps support cloud storage services like Google Drive, OneDrive, Dropbox, etc., so you can use it like a regular cloud-based password manager by placing your encrypted vault in your cloud drive. I prefer Keepass2Android on Android and KeePassium on iOS.
Is it safe to store your KeePass vault on a cloud storage server? Yes, you should use a strong unique password for your cloud account, and enable 2FA for it. That's already 2 layers of security, the encrypted vault with its own unique password acts as a third layer, it's safe to use it this way.
Note: I know that 1Password is a popular paid alternative, but I haven't used it, so I can't comment on its quality.
You should use a strong and unique master password instead of a pronounceable one, though passphrases are considered secure too. For best results, use your password manager's password generator to get a secure one. Make sure it has a some numbers and special characters, and a mix of lower and upper case letters. All you need to do is memorize the password, keep typing it a few times, and within no time it should be just as easy to remember as regular passwords. You can even write it down and store it securely, maybe put it in a plastic wrap and stick it somewhere where it can't be found by others easily, or place it in a safe, or hide it discreetly inside a book.
Deleting your LastPass account:
Please take a backup of your LastPass Vault before deleting your account, otherwise you will lose access to your passwords, notes, etc. You may export the contents to a CSV or XML file. KeePass, Bitwarden and other password managers allow you to import the file's contents, and save them in their own vault.
Refer to this support page for further details.
Note: TOTP codes cannot be exported directly, you will have to set up a different authenticator app manually. Aegis for Android, and Raivo OTP for iOS are my preferred apps, they are free and open-source. You may also consider using the Microsoft Authenticator (Android, iOS) or Google Authenticator (Android, iOS) apps, though they are not open-source, they are safe to use. Authy suffered a data breach a few months ago, which is why I'm not recommending it.
You can delete your LastPass account from this page.
- infinia
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.