|
Acer
|
c24-1655
|
2022-05-18
|
399f68dc94a6c42030efcd57fd034ff721f860b7b5d447779e7a6a6c99aba34f
|
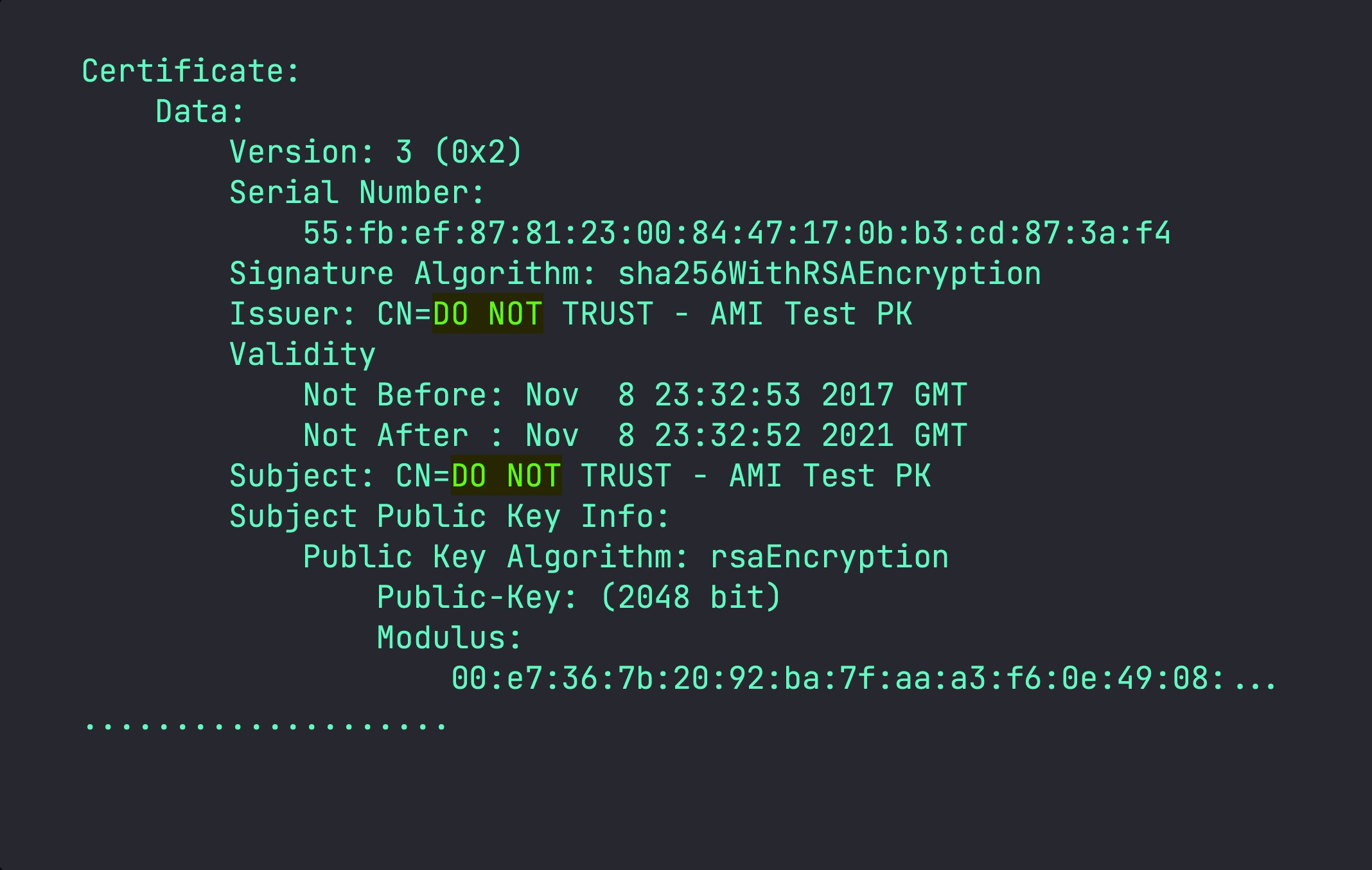
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Acer
|
aspire c22-1600
|
2022-01-17
|
d938d08543d35d4249a51057c1d9c62bb1f6440af19913c5feffcea47dd3de95
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Acer
|
c24-962
|
2020-12-08
|
3d525f96f63995c51ab1bcd2c50ebb71661ffeca9f78f97cc97e851d0e2bbbdd
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Acer
|
altos r680 f4
|
2019-07-17
|
a2679a9595a104d70bddc024dbc4f65f0dc9d906f30a0d1ae6b996b14246a6c2
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Acer
|
altos r680s f4
|
2019-07-17
|
e5fdaabf11b236c5c7b040d674936e84db746a180ab9999317e16dcb77aeeba4
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Aopen
|
iKBLMUx-DER(Volta Charging)
|
2022-04-27
|
fcd339e12730f057e41ad41228f9612d4954f2d0dbcfeef37e14dcdaf2866e05
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
xps-8950-desktop
|
2024-07-04
|
37b63cbe1951968b45b586673af076ff09ea34dffbe17955dd5fcbaf9922dd92
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-aurora-r13-desktop
|
2024-07-04
|
d776a493542f7a66d05844507e2a93f0c5f32bf6538ef58eca6f333eb614f04d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-x15-r1-laptop
|
2024-07-04
|
b6b89edc03730460183665c182a26617a9b278288acaec12df88cb77dec51d8a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-m17-r3-laptop
|
2024-07-04
|
c919c804dd8fa56303825c9f8d3cd1624cd0b7bf947de647bc18b02f20547012
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-area51m-r2-laptop
|
2024-07-04
|
e8a3b73af252dd1716397324b458f12bf589feb369660af827acac15c47abdd9
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-aurora-r15-desktop
|
2024-07-04
|
18e65d73545bdc0b0d631847e8ea1bcc095ec774a6ede90c2dcf9658803be6f3
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-aurora-r16-desktop
|
2024-07-03
|
31028653128770e6dc209ab83fbc2b50c1457962eff2796ad32eb96bcec0208b
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
xps-8960-desktop
|
2024-07-01
|
fe7e3b5d3ca095e1b9a4e2fbe8fa46f408916675b209ee535210ca835f4430e8
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-m17-r4-laptop
|
2024-06-12
|
f75b595b9ce5e1e25a5d64e54edffdf696251b4f4e860c0d3a03a183631f090e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-aurora-r11-desktop
|
2024-06-06
|
8f79d9de33f5f131226a78ccb10bb16218a5be51b2105cc32e38ceb0c8c30e9a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-m15-r2-laptop
|
2024-01-30
|
69da86e9cf24c49496529f3041604a6bb1c0c0ab86c192239d31d3a9b92467cd
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Dell
|
alienware-15-r4
|
2022-12-08
|
608e410d1c0475dac58b1e8f36b477aa8d9e9f28d30ec89d44b550e36bbbaf47
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Formelife
|
Studio Sys UPD
|
2021-02-08
|
a451ed9d6359fd109f495c75bab2678285265a72be64b3e5d0d5447a0e167cd5
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
E162-220
|
2024-06-20
|
e8659eec88d8ed7508ec7c651580a4a1b028aef3b286b6c178bf10c94ea9a0a0
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G262-IR0
|
2024-06-20
|
731df9e98a8eafad7ef38dac68ea145ca4e4798a03cddc36d0365ff923efb800
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-280
|
2024-06-20
|
36e61b1016165cd6ea10c5569727988e4dfe0284cfc7a23230c76fa6fa1a0710
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G492-ID0 (rev. 100)
|
2024-06-20
|
e568242fd9403b4e5f97c9f9f39b06aae69b7cb8d78f4ee5773ab590a5a538ab
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H252-3C0 (rev. 100)
|
2024-06-20
|
2839b666d6177cece2786bab3e529ff310d742c8cf289314ee75c777a61f1c6d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H262-PC0 (rev. 100)
|
2024-06-20
|
d38731887a5e3ee5ca99d6f6b4ab1c5d8ead20246b1872466dbfa154e6998769
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H262-PC1 (rev. 100)
|
2024-06-20
|
dd08e115ec07af4b2494807d28903c787f90adf4c0553383e2cd3bbd5f343bed
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H262-PC2
|
2024-06-20
|
94bc1be01282aff48fc0a56cfe97fe5d3b8259345989e7cc78b3100f42aeb308
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MD72-HB0 (rev. 1.x/2.0)
|
2024-06-20
|
0c21e595f6cb6825a2cc2523a44c63f1d9612141740e0830326c61dd405d55d7
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MD72-HB1 (rev. 1.x)
|
2024-06-20
|
de652b50e4152e06100e177dd4e44dac92bb51d2f0e783176dad338d241107a5
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MD72-HB2 (rev. 1.x)
|
2024-06-20
|
ce57caef115789b978a0c79001232c06e316b2377378ee9a6526240671b96df1
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MD72-HB3 (rev. 1.x)
|
2024-06-20
|
aeceb9d2b5967597e69823b6aca157d2bb8f16d28a5f22433869898edac0f945
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MU72-SU0 (rev. 1.x/2.x)
|
2024-06-20
|
7ee64186fd36a89f143ab73db0f48a5defa8e2cdf430d488e0a50bb773ef203a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MU92-TU0 (rev. 1.x)
|
2024-06-20
|
d394c43f2063758d9906c724e4f5e3227f6225e9d0ab000e862bcdb2e21deb84
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MU92-TU1 (rev. 1.x/2.x)
|
2024-06-20
|
abbb400ffb198b19e734685e4e10d1ac4c4bbe0ef226c989130922f4efbfd93e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R182-34A
|
2024-06-20
|
bd1364247d72f0353ffcbd424dec6456127268a2e52c67e4f95ea825ee0e64ab
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R182-NA0
|
2024-06-20
|
d7afc67e73d101358adaf6dc010d0bfbf2a964444ffab3c6a57c6a53dae8d34a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R182-NC0
|
2024-06-20
|
e3f0c98ac8f79168f5de66cb09991b91bc46804b2997a39f6087ef6d3a9be514
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R282-G30
|
2024-06-20
|
36c99e0a608a670d3ac37705372dc4cd1f2597ebbc16974350c07a3acf74d522
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
E152-ZE1 (rev. A00)
|
2024-06-18
|
a9638651a2475403924f124552dc199689a45d2e2e59e3dea2b223667dfb63de
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G152-Z12
|
2024-06-18
|
ad457250d51a0638880d9cf1df9dd029ab34b36265eda73c5459d8d0460ba3de
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G242-Z11
|
2024-06-18
|
2ab6af312a78886a13144814ce766a771604755f8dd303381658026304415280
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G242-Z12
|
2024-06-18
|
eef3fd99672410b85e6342c5757723d0d3ccecef9805237955baa20780de8b4f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G262-ZR0
|
2024-06-18
|
f21b8f836105cdb4051d8bb29302dcf86836b640bf048b24f3c76e930b513b32
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-Z20 (rev. A00)
|
2024-06-18
|
62bb737d55f4caa082b7ea2aa6f8a59c8efdaf9d5ac5b158cbfb32a6cead8164
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-Z43
|
2024-06-18
|
1b6ff7d60400c7c21a5b28f947475e61abee187627c1ff12cddb25b1ce59ecb3
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-Z45
|
2024-06-18
|
18def9ce5aa6551c1d7e77e9f53e34701f77b89d6b32d41ea050cc94d52941e1
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G482-Z50
|
2024-06-18
|
b14d2e3fadc16c97684a4ae947798bb3a67372441dd7252568f71fc86e98ae9f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G492-Z52
|
2024-06-18
|
062e3100bfbe635c66feed863141f7a6f2bfcf0b887a5b3d7ae31fb610d17cac
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H252-Z12 (rev. A02)
|
2024-06-18
|
ac416150a9752dc20107bef240e73c6054af4992348003429bfd97a7373f4f27
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H262-Z61
|
2024-06-18
|
340cc5c8f4468eb2d36b684dffbf139b4ac4504b5db3993c3c1b5145858c5131
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H262-Z6B
|
2024-06-18
|
0e761b6f3c7d3a1407addf499ff848c493a9d0b0197368cbe858bbc4fa5a4702
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H282-ZC0 (rev. A00)
|
2024-06-18
|
0b739af751913ea6ff42999069963dcf6a1bdd58a3de800ab721d9bdbd59bf0d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MZ32-AR0 (rev. 3.x)
|
2024-06-18
|
a4102b19258804214beb838f61699a7623cc654341e6f60ad986dae805935c14
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MZ72-HB0 (rev. 3.x/4.x)
|
2024-06-18
|
e0a3837abd91821c4ad98687d2dc6456b7fcb05c8b672c48f242ffeabfa3e9b4
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MZ72-HB2 (rev. 3.x)
|
2024-06-18
|
7678e64f7728c059b228ddec74f0918f0544d5193f7b8efe0bf03e8f36c2f5c5
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R162-Z10
|
2024-06-18
|
122baff0bf1243b945a7eaa9ca55303469d624d6150d4da136d697878177f1a8
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R162-ZA2
|
2024-06-18
|
9d318d27111a3c5a2e3a6451103750d70dec9d6e9d048f7e98fcd60066b98aee
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R182-Z90 (rev. A00/B00/AT0)
|
2024-06-18
|
dbd77ee47e4bccbb2b8af2883765641e9d7c404937da2942637fa1b4b6d4d635
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R262-ZA2
|
2024-06-18
|
c7f73261e85bdc43932e49254cb8654ed2ce0945379592cecb081d51e5834289
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R282-Z97 (rev. A00)
|
2024-06-18
|
076310804e591d1c2d4ab1d53cff0866c04a4189e03e6964b528b8a94faa7991
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
S252-ZC0
|
2024-06-18
|
8927ee41096d71b75bbef2672e22f640a22ae3588f4f44786fff92c70b861885
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G191-H44
|
2024-05-27
|
28068e88e5041161f4485f958f49060d6a865e4beb0b53bafc8f3c5e5e3923b9
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G241-G40 (rev. 100)
|
2024-05-27
|
912834981a1de06dcdd4f8cfd11e7db46ac691e5ef20616d76d859e889c303be
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G291-2G0 (rev. 100)
|
2024-05-27
|
0dbbb711ff0879479dc30b9a7116fb94f093e0225b74916f6b79edae90d8fb2a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G591-HS0
|
2024-05-27
|
bce2bb4589e9ba8bc8029514a887f3f3bb4ded3556bb5d77dc1a38bad564b435
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H231-G20 (rev. 100/A00)
|
2024-05-27
|
819cf98fc21e036b3ae7e6390ae09edcf6fc6c260b22bf6ede0852029ef2495b
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H261-H61 (rev. 100)
|
2024-05-27
|
190d03dff0cfed20b38ae3270c8bb197b024765963dff6b7730d96bfebcbb24c
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H261-NO0
|
2024-05-27
|
7eab23785afd939c2abdf53e001e896c67216a6cc75b646d990fdf92ae226748
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H281-PE0
|
2024-05-27
|
9f715f7b4128701de97332885c28547fe89ca4214de5af85623ab90670fdbbff
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MD61-SC2 (rev. 1.x)
|
2024-05-27
|
98c90d7d56e82fcf28b362fbf659c3dfd3f987de96d997defe2ef2e78f33cecf
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MD71-HB0 (rev. 1.x)
|
2024-05-27
|
82bbbdeed52e95c3f19ad09cc8fff5ea17f9f5341fbef5f88fba478c24e9fd66
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MD71-HB1 (rev. 1.x)
|
2024-05-27
|
c6957244c7417f2ea28889e02d23b63091b6049b82263872ec3a952765becf9c
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MU71-SU0 (rev. 1.x)
|
2024-05-27
|
67c4f4ad83e151ebe6e61092bec3153ec269e7be1945dbba0c61091a345a885e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R161-340 (rev. 100/200)
|
2024-05-27
|
1bea20b7f9327d743487da2db53e5fb89ace6d22f56600b58918737418e716ee
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R281-3C1
|
2024-05-27
|
aef16fc11c0f6ddca64581dc5b42b9d6e4ab66807ae7c5a30ccfd8f6774a2b18
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R281-3C2
|
2024-05-27
|
5077c5d90bce52e6e22371dd64910f30aad69c42aaf9a144165682fffe23c3e0
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
T181-G20 (rev. 1.0)
|
2024-05-27
|
c2b46f65550950fb75d45f5bff54bbed8d4877d803a9688739abd47909fc5f6e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
E251-U70 (rev. 100)
|
2024-03-20
|
6c404dfcb9550bf9080bb679ccfba607c96b149772c345ddeab0f881fdd16f8b
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R162-ZA1
|
2024-03-06
|
8567d8f2fd8a32c33c81aae33ef21e34f818159199f0beed6c10dd6e2283351f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G242-Z10
|
2024-02-27
|
c7e9eff716b9e7000c89692637c58014ee0be37d7ddd39a0c2ae4ecba82e38fe
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MC62-G41 (rev. 1.0)
|
2024-02-26
|
dc4153ee0a3333ab789383cef8b0d9760b9f416138a093cd3357370261babf4e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MX33-BS0 (rev. 1.x)
|
2024-02-21
|
a0e138096681313a3923eefa3bd3480e6416c73d627d3888b36ce7bb6b2b989f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MD72-HB2 (rev. 1.x/2.x)
|
2024-01-12
|
e01af875c3100fa3d72d014aaf93417317a1a4a4e69c4a28c216c73dfa5e041f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G482-Z54
|
2023-12-21
|
f446b6d7d932602558e4abdbea9a9b826a12d27c535ca6c2d0bafa5e34ec3864
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R271-Z00 (rev. B00)
|
2023-09-22
|
dcff49fc24b1b8cf02fce97a15b0bc8bb19c6979df21136007c677ac3b9023c7
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
E152-ZE0
|
2023-08-18
|
83d24271a7b1b9bba7070c128edcc8b4d6a5e7c96caa920baf5c014efbf6775d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R282-Z93 (rev. A00)
|
2023-08-18
|
255ffd2b1161bb8a53626ad3920c40eb5f0f63cb1d5710969abf31797f8771de
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R162-ZA0 (rev. A00)
|
2023-08-17
|
85f9cdc44ed670c411f0892b769e91567f9a81bcdeb92861fcf6e2ffc7773f9c
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G262-ZO0
|
2023-08-16
|
efc056c3caa782e178b7ade2333316ef39a0a6e17157c68a61927b3a045061e9
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H262-Z6A
|
2023-08-16
|
2ac696517ae7da9f3efe81af66b89b5f7b24beb6e09aca06e61e454915070a3b
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MZ72-HB0 (rev. 3.0/4.0)
|
2023-08-16
|
2ad038a3b127e95df1fc8fa61bafb96a113fe0093d9ecee66db9ece973c5a257
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MZ72-HB2 (rev. 3.0)
|
2023-08-16
|
225cea866d8c5843d32d6edc97764b69b05707e47c9537e6e6e7f4ac06775816
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G152-Z12 (rev. 200)
|
2023-08-14
|
e7969888310f2eceb73544fd8108eda95c1a3ea62ff57da93c643bc55b898f50
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-Z40
|
2023-08-14
|
d31512a9a475071b6e14a03aed7c5286aa0c622925d7a840bdee7158a7d9583c
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H242-Z10 (rev. A00)
|
2023-08-14
|
1096dfa8e4e5f5d2410eacac73c51bd1b946bc4d2f110a44e8c33f53d0182eb5
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R152-Z30
|
2023-08-14
|
5297e4a26fd8ed927abcb2438a5ac2a4e35e770d06d272ed77b3d847bebb11fb
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G262-IR0 (rev. 100)
|
2023-06-16
|
43dd7e97fc6fd1fc0ac1ef601c00eed9ec9b5d5325243fb8c6f0ae3517fce89b
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-280 (rev. 100)
|
2023-06-16
|
5b7eee5f852ce1424dfd476d8713650e528fa359f19e551b7adb9b6a12ad467e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G492-H80
|
2023-06-16
|
e79fefca976e762f76a8ce36494928dc2ba039de02b69659a87b5245cb27ac2f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H262-NO0
|
2023-06-16
|
d04141fdfff53843c10ef247e885ad9fb62ffc58c89580718ecd2b102a590f30
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H262-NO1
|
2023-06-16
|
ca65772cdd5fef0d287957d5a6e308fa1126b9b40a2cd701e1190e852ce0bfd2
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R182-340 (rev. 100)
|
2023-06-16
|
ade7666d9e200c0929260025880128674b63349911f1d03857a42cf753f10b80
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G291-280
|
2023-06-15
|
6917b15d532856e0c0f7cbfc3501f4d5c273616046d94695e01ce07303f6011f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G481-H80 (rev. 100)
|
2023-06-15
|
53a8edb12be4b79c231d3f950e20343f20f3727a6544504259639fa6506f2457
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H231-H60 (rev. 100/A00)
|
2023-06-15
|
56289ef76755acc7f4e843b3ee0f29ec8f063f113f640b157d095d18a866d874
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R181-2A0 (rev. 100)
|
2023-06-15
|
01c95a23c9bfeff78ab2b6d77ca33e6a967cf624d1afb5fad393776c79a25920
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
S251-3O0 (rev. 100)
|
2023-06-15
|
303797b38020f7b91381f887954f819112509c4b855ebd75c7a31dd227acf1cc
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
S451-3R0
|
2023-06-15
|
c9a2e7d55dcf6e3f7537515d2c6cb0e36770a5fbea7a01dafe4a90359ade90eb
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
WRX80-SU8-IPMI (rev. 1.0)
|
2023-06-08
|
249510667c5c37bd25d731655d7dbf18c5fc2d8d377c0c2326810cda6d9c0f46
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R292-4S0
|
2023-06-06
|
1dcce1bfce8c75c3fdf8a307ba7f6d0231504095e1c4e6bf2166a4cf75df29cc
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R161-R12
|
2023-02-24
|
523e9d1bf5710144e36f9535141955dcf9a3d075fff092f6b4d1e12ee2eda562
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
TO23-H60
|
2022-10-24
|
955038954a0d1463be658fe518b6006f9fde166b67e9007f3befb9cfa62e5da9
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BRR7-4700
|
2022-09-16
|
a462c1a73072f541b6719e4cdee351d44a7cb3593dabbc6809b5b387d909eee5
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BRR7-4800
|
2022-09-16
|
424e8b46bd3feec4aae4ec33eae1ca8658526eeb66e121adb244d3c322dd005d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BRR3-4300 (rev. 1.0)
|
2022-09-13
|
5cc12fd686928c97fa7fbfda17250579adc4e7bd11e46e88650de5ebca6ed03c
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BRR5-4500 (rev. 1.0)
|
2022-09-13
|
6ea44803e9b188161126374021e9d845136edd676d33fc80e5f9348b8d577a87
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
W771-Z00 (rev. 100)
|
2022-09-13
|
d07d7094aa0dbdb896f8d3dceb093ea8c1d72ee0009472ece73190d2071aee6e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MB51-PS0 (rev. 1.0)
|
2022-08-05
|
372c9a6f86f60d7cef6ae2d2ee7ca0d55df998ba0a47468668c6758b3d3db725
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G492-ZD2 (rev. A00)
|
2022-06-21
|
c8ab653dc8a40406c0a8a4d71b56059a2f9b7c7ab9e883290acd071941c7bc25
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MW22-SE0 (rev. 1.0)
|
2022-06-21
|
d369b68d0c38afedcbb0eeb82f2d06d486e9c0ce212ebe3b0d9f8dfcdbbbf5b0
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MX32-4L0 (rev. 1.0)
|
2022-06-21
|
78ce8406e3b09a3450d41ba11c1dae91456f25c796441dabb52c7b7e261b3a69
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MW32-SP0 (rev. 1.0)
|
2022-06-20
|
0cd64d233ea4db6db2a90962d2888f4e5b967fbb24fa944ccbbfc2c02d5a358a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MX32-BS0 (rev. 1.0)
|
2022-06-20
|
40234a98894a9855db1a921ffe9d272caa1e5702dcdd14afc82f6a91753fd460
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BER3-5300
|
2022-06-16
|
a3ab1a934f5806b5472f13257771924e3fcbaed289b2d6a860ec2fbbfd2d0c11
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BER3-5400
|
2022-06-16
|
06879fa2383284b0222247992f7d359bf5d0ddcebfdcd5b42a20ee5f46a8473f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BER5-5500 (rev. 1.0)
|
2022-06-16
|
68f88269c87ecb16f9b7d9269005ce505a3498b9e3440054742481a2254d5aea
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BER5-5600
|
2022-06-16
|
d98134626baccb58d0d97613efeae6d504b112a4f8d8849e2599ceecf55f7fad
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BER7-5700
|
2022-06-16
|
ec439231fb2d3491a63b173bda078a128bf02b19262b3549f3a799992442d9e7
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BER7-5800
|
2022-06-16
|
7704838038c24fa47fadd54f19c5911fa39823ecfb5f451db59271112a07e777
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BMCE-4500C
|
2022-06-16
|
43cce322b194b9be7bedb247098e8b691878f238b14199cfba11af4422b3464d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BMCE-5105
|
2022-06-16
|
c412ba0cc85278e93f349b9fae6011982f23f8f3a7b6539a36d90b551ae1006f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BMPD-6005
|
2022-06-16
|
6f14b4087af44921d294462fb0d65259f18af0cc23b7ab1c5b87773b9c3c13e4
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BRi3-10110 (rev. 1.0)
|
2022-06-16
|
d6626703c5940d244a87f2967f0c54f4a5a7b53597dd92a0b561f28a2f9a9161
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BRi7-10510 (rev. 1.0)
|
2022-06-16
|
af98c4cea319d387751cb356a28390fa630a1b2f66920a3202b37e0acb861ade
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MF51-ES1 (rev. 1.0)
|
2022-06-14
|
dbe505cc1f3a4135628b7e22c7fddb99bf3ee1d46f82a84219e8cb0905c20ff2
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MF51-ES0 (rev. 1.0)
|
2022-06-13
|
d27437e85db58b607bc173e844b31dbfb8b949ea3c225e13377ae942572c4611
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MF51-ES2 (rev. 1.0)
|
2022-05-24
|
9bd110e7a5a1e1cdd77af3702309d98f748cdec6d25a5e76c04f63417e2e6a8d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G492-Z50 (rev. A00)
|
2022-04-26
|
0b2bd8851706081fb9e310e5f4a7a97c3a0bb32eb7167a609e602ba6cec1ea89
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BSRE-1505 (rev. 1.0)
|
2022-02-14
|
2f18902d7afbe8d900b6552c2d7a86760f05c4698c1018053b2fad97f6ab51f7
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BSi3-1115G4 (rev. 1.0)
|
2022-02-14
|
6f6c034629c0d8df05227f4e7d85d02d8fa52d7fda0940fd4f80f62a23be06c8
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BSi5-1135G7
|
2022-02-14
|
baddfacc85e4aa97915493c4f66cde6002104bfc10ecfa3839c4fc6e32597953
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BSi7-1165G7
|
2022-02-14
|
b191f4293202c488ba673c288bb5edbaf506a9835a508ec38fa705797738c918
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-Z20 (rev. 100)
|
2021-12-21
|
e0ae28d4aca350a31f66402f4b0f46e05e4aaf77adfc813179a7df20c8f4b148
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H261-Z60
|
2021-12-03
|
826f711b5accbc542c3e33d607f1dd10edfb3486772975f204aa2de43bdb52fb
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MZ71-CE0 (rev. 3.x/4.x)
|
2021-12-03
|
c0c4215e8207d397914a56edf50428f01ad3676c23630ef7b8c06cf36e45a7e1
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-Z40 (rev. 100)
|
2021-10-19
|
fcbed542b232be01a0ed2d52dcd3dddc101fafed3da9f3e3aa6b17b652e640f4
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G182-C20
|
2021-10-12
|
e133210fdecf2d57cde25b0bc706437210318e37655eb22a97000bf27a02c177
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R162-ZA0 (rev. 100)
|
2021-08-02
|
03e23d40902c4e68730e74ddadcc716f46032774001e1b6bc606c5294d4bacf8
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MZ72-HB0 (rev. 1.x)
|
2021-07-30
|
390cd14f2be9ff14cdcc90a9e705cc017bb2535e66b93859eddc233425998937
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G221-Z30
|
2021-07-12
|
8e8b934cc0bd3127262a9e52fac754d64abe27c09902a78acec81c0daf883f77
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G291-Z20 (rev. A00)
|
2021-07-12
|
8d49dfb69b420390cf13ff8f3a3b3ab88e5dcd46a182c4ac5be9868bc6278c35
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MZ71-CE0 (rev. 1.x)
|
2021-07-12
|
d3b797002d243cbed1182569ffc6b5e5f6243e59ee27bbabae7362fa80be6e91
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R181-Z90
|
2021-07-12
|
24be564cb337350bd9cbf409cd95f29b760e1ff872f99b27379c40b533e9f2e6
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R271-Z00 (rev. A00)
|
2021-07-12
|
99f913a3f88561d7163bb1ed79380dd346897e577315eef71695aeb861e82579
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
T181-Z70 (rev. A00)
|
2021-07-12
|
e42a49d2674808c57b781e8b3d78613a143ba9797d1a856ccd2a62302a49520e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BRi7-10710 (rev. 1.0)
|
2021-07-02
|
14c74b9b80e71d3302c13aea0dfea3560e1452a55c698c20e457c5b495154443
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BRi5-10210(E)
|
2021-06-29
|
56430f2f4f9aef4e50f503dc8397fdb20b005bf38a8b9029c43e3eed56c39229
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G492-ZD0
|
2021-06-26
|
bacd1c945c9ff1ecea3e29039ad8b742c6d040e5792bb45008c1b7f664fb36bb
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-Z46
|
2021-06-17
|
31aa7ba19f6edb9472a3da22793803c265a0cb0b7cd7979db56251c37edcfe5f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R282-Z90 (rev. A00)
|
2021-06-11
|
8cc6129ba23848fbd65b91a9b70999aad19d3b7a6d168066cbe4a0b759fc5a5c
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R282-Z96 (rev. 100)
|
2021-04-28
|
605db3a5cf91d915929488803446e5a51dda16d661e76840b707474d2df79069
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G482-Z50 (rev. 100)
|
2021-04-26
|
9b0c2aaaef88b38db18e4efd44b2582c8401f9a17f2c54d0e1f07d2c94a9a5f4
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G492-ZD0 (rev. 100)
|
2021-03-05
|
25555956322c0eaecf58fd759ed9b0b7857f9dd149b02de55e2f5eedb291117b
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
W281-G40
|
2021-02-18
|
f7c504d3d3907aa4c7f70ca1fbe1fed7e73426eb987b9c5e2f6b31d42e801af1
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MW51-HP0 (rev. 1.x)
|
2021-01-08
|
1190d15905ff8656d2d0601c388df633b1646fd585de4fe871fdf93fc23d35a0
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G482-Z53
|
2020-12-24
|
f5f61e3f93c7f6615cfdc26efce6a83b3188d697e2243643d08d10dfa9de8afb
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G482-Z54 (rev. 100)
|
2020-12-23
|
0fe0c762e396660fb30aeddcf5a5928af864eb44399271ed975913f36e46190e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
C621 AORUS XTREME (rev. 1.0)
|
2020-10-27
|
7edc3eecb5d5ed515e06f8130d875fcae07cb0c7bfaa2e4cd8d86862e5ecc256
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
MJ11-EC0 (rev. 1.2)
|
2020-10-14
|
3631995d059e336863527f1511894bdfc61361bc0691a430b3896fb94746aded
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G291-Z20 (rev. 100)
|
2020-08-24
|
6d6107f0d094fab41eaf6073089de8a0b24bb7a66c5851f534a8f1d26812c3d2
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H261-Z60 (rev. 100)
|
2020-08-24
|
edd3eccfbbc2ef2ac40e723697f67a346fca062ddd6679c5ff8cfbb91d3b6afb
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R181-Z90 (rev. 100)
|
2020-08-24
|
575fc48c70ea9ee40f8016ea2328ebe790e7e556333a95b9b511be466047f668
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
H261-T60 (rev. 100)
|
2020-08-20
|
6b636c9fc0ec84737f2238365e71c23e9227695cd5ad52bf40dbe8290920fb60
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
C621-SD8
|
2020-07-30
|
d6ad23c1fab3f0a2babb23e7907385e25a06801c2edd50d108e5b08f923855a8
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
C621-SU8 (rev. 1.0)
|
2020-07-30
|
b9017e90f6c47a9d9560cfd92206c4b2e624cd91cd7f0680fb75dd972ef9582d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
GB-BSRE-1605 (rev. 1.0)
|
2020-07-29
|
d72f64d5a25b9088f7fff456d3783c2fb0e7926cd4de6469c6c3f57690830907
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
C621-WD12-IPMI (rev. 1.0)
|
2020-07-21
|
0215ce75b3629651d0c64b0b241095b58f0af921cec3022c524d531c22f1385e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
C621-WD12
|
2020-05-06
|
f528dbe55aba35bd4e5d55fe853afed41c54d78719765944a5ea74dbc062f4b5
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G292-Z42 (rev. 100)
|
2019-12-17
|
09d1d8dff99b19615f14413d6ba20891819d481b12667452786510209344095e
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
G482-Z51 (rev. 100)
|
2019-11-29
|
4dcab1a378bb4cc541f210917c563b95dd678e185b4d0dc8483b175cbf9097ad
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
W42G-P08R
|
2019-09-03
|
f0d6176199b56171ec12bd663025c664b2bf3f8b844bc90edc8dbc3cc062871d
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
S12-P04R (rev. 1.0)
|
2019-06-27
|
25b628eb776a57d9fa45cffb00f8f3347cb9d7c2f3c33712348b85c3ecad2d4f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R272-Z30 (rev. 100)
|
2019-06-25
|
fbf652a641fc3d847c148abb65130f7eece7a51a9c6607f1c403a8bbdde6ce48
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Gigabyte
|
R181-T90 (rev. 100)
|
2019-06-12
|
c02c66a7d393e7bd8cf757197bbc6bc22fd9f9b38a8a1068166eba97bc5b4a29
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Intel
|
BIOS Update [PNWHL357]
|
2023-12-18
|
a3fb2070233c4544bac73cd0f6578e65dfe5333cdec5a1e624806b4182127740
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Intel
|
BIOS Update [PNWHL57v]
|
2023-12-18
|
0f9dd355e6ab0369a9df46af391350acff375e9c1c7a488aa06e875f3ab06fd2
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Intel
|
Intel Server Board M10JNP2SB - Firmware Update Package - EFI BIOS 7220, BMC 8100.01.12
|
2023-04-03
|
ea519a5fd11f6a1955545f3c01fea145589b272c474f61c72437efda90f024bb
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Intel
|
Intel Server Board M10JNP2SB - Firmware Update Package - EFI BIOS 7219, BMC 8100.01.11
|
2022-12-13
|
388cd43e6007e7550c22eff47ca1b4527de8883e30a572ba43e4a9a00c8203ea
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Intel
|
Intel Server Board M10JNP2SB - Firmware Update Package - EFI BIOS 7218, BMC 8100.01.10
|
2022-06-29
|
460fda3a419e94caa56d17552e6acd4a67c678afb5b7e80b4651dda5956c54ac
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Intel
|
Intel Server Board M10JNP2SB - Firmware Update Package - EFI BIOS 7217, BMC 8100.01.10
|
2022-03-24
|
a132cd6038454085a5d1fe961a70d08c7afb17c6a1b846a71ddb4c08edcae652
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Intel
|
Intel Server Board M10JNP2SB - Firmware Update Package - EFI BIOS 7216, BMC 8100.01.10
|
2021-06-29
|
e871223077aedfb6983ab46ee71b1a1308797f2f0235b77b9cb4792d04d9f06f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
AS -4124GQ-TNMI
|
2023-08-10
|
d5b2fb249bfea79224982d0663843ccf814511ba2054f37c18102ba06b312b31
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
MBD-H12DSG-Q-CPU6
|
2023-04-21
|
730417639fc5e894029fb0f33f8c5ea8c82829f1b4ea26d8f203f226a868b25a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
MBD-H12DGO-6
|
2023-04-18
|
81c9d66ad0e9687e13eb4f7cc66838b64a3f4a2541ccb1844062780f6a85df9f
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
MBD-H12SSW-AN6
|
2023-04-18
|
c217692eb826ad399f33fcd12a2f1092764c3a584d4a135f646e7acb3cc18a73
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
MBD-H12DSU-iN
|
2023-04-13
|
0b4ccd02bd1e5e218672f1f959b76b621da86568b022b8f53f6e6c4de67c6745
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
MBD-H12DSi-N6
|
2023-04-13
|
7c4bc9a577443b1d8abffc2344cbc82691e72c2f53c0acde4b9ff7f56e11a0df
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
MBD-H12DGQ-NT6
|
2023-03-07
|
e3776bf7f73b11117981241dd64a0019bf291a426da3848373ca628712acbf7a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
MBD-X11QPL
|
2020-02-24
|
d45f4621d8c40a27d4f4bcb5592a0baef7febe5bdf9f675963feab6230ec1c84
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
B11DPT
|
2019-09-06
|
b870f5071c2aaba57a714d409e27ba15c5bc2476ec5e16471a79f4272f23ea5a
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11QPH+
|
2019-08-22
|
a39c7ae750563f43f67a832de470a146f11e27b68f9701c7f7b923c67c7c4eb7
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11DPS-RE
|
2019-06-11
|
fd8a767a767843abdd7165a1e1819463bc5195f169f0c570ae18ddc68d2f2029
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
B11QPI
|
2019-06-07
|
d128e52fb7278f14b6fe042982750ac0de39e4c32d10b771e039270603719aec
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
B11DPE
|
2019-05-29
|
beb4e0a939a94256dd65d981ba8d7c36fd4297a56dfa43a05520348817e67e60
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11SCH-F/LN4F
|
2019-05-24
|
a42a7f0f1c689c716915d4e3b9f611f4a586006d90de40f8661bf161427c207b
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
AOM-X11OPI-LBG-P/MBD-X11OPI-CPU-P
|
2019-05-10
|
058995906709407a71b19f551a86d38265bc75938334a0bdbfae7e14d6b00ac7
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11DPG-SN
|
2019-05-10
|
5d11d805debd6de0251df46a6d284fb76e1a4ef6b5981aa8e2782dcc29605e63
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11DGQ
|
2019-05-09
|
3005d1aec88adf5b46c7cbea0465d50f2e6845b76b05419068f10d1aa7325652
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11SSE8_308
|
2019-05-09
|
94a0261c16595d3eaee502cc7762d65ab6fcdabf49f16671d157536ac520d710
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11DPG-HGX2
|
2019-05-03
|
275bbd2e442fe8133c90beb65416ac3e2ba5d2933899348818287b6dfaa25e07
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11DPI-N(T)
|
2019-04-26
|
389f7518b4dd4e7eea1f595f9199693620b3cb5d542a609e709904f0b77675cd
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11DPi-N(T)
|
2019-04-01
|
849db7bb59486d02674bf6ca0c5d5577cba502b5c2f0d13ed6945fd466df00ec
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
X11OPi
|
2019-03-08
|
635060eff5f4c73209cb6fd8b6b4767f46c17267a24aa6c471dbbe656bcc65d4
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
C7Z270L8_222
|
2019-02-26
|
0d46bee3f5e5dabcaf681d3504a98b200ee88cc281e1a637ecf9fe19f89609b6
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|
|
Supermicro
|
B11QPI-T
|
2019-02-22
|
185a6593df982988acc7d45f20c9dd32c001eb6e7b007e3ecf629c5fa9e241e9
|
55:fb:ef:87:81:23:00:84:47:17:0b:b3:cd:87:3a:f4
|



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)

Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.