The Russian state-sponsored hacking group 'APT29' (aka Nobelium, Cloaked Ursa) has been using unconventional lures like car listings to entice diplomats in Ukraine to click on malicious links that deliver malware.
APT29 is linked to the Russian government's Foreign Intelligence Service (SVR) and has been responsible for numerous cyberespionage campaigns targeting high-interest individuals across the globe.
In the past two years, Russian hackers focused on NATO, EU, and Ukrainian targets, using phishing emails and documents with foreign policy topics, along with phony websites to infect their targets with stealthy backdoors.
A report published today by Palo Alto Network's Unit 42 team explains that APT29 has evolved its phishing tactics, using lures that are more personal to the phishing email recipient.
Luxury cars in Kyiv
In one of the most recent APT29 operations spotted by Unit 42, which started in May 2023, the threat actors use a BMW car advertisement to target diplomats in Ukraine's capital, Kyiv.
The sale flier was sent to diplomat's email addresses, mimicking a legitimate car sale circulated two weeks prior by a Polish diplomat preparing to leave Ukraine.
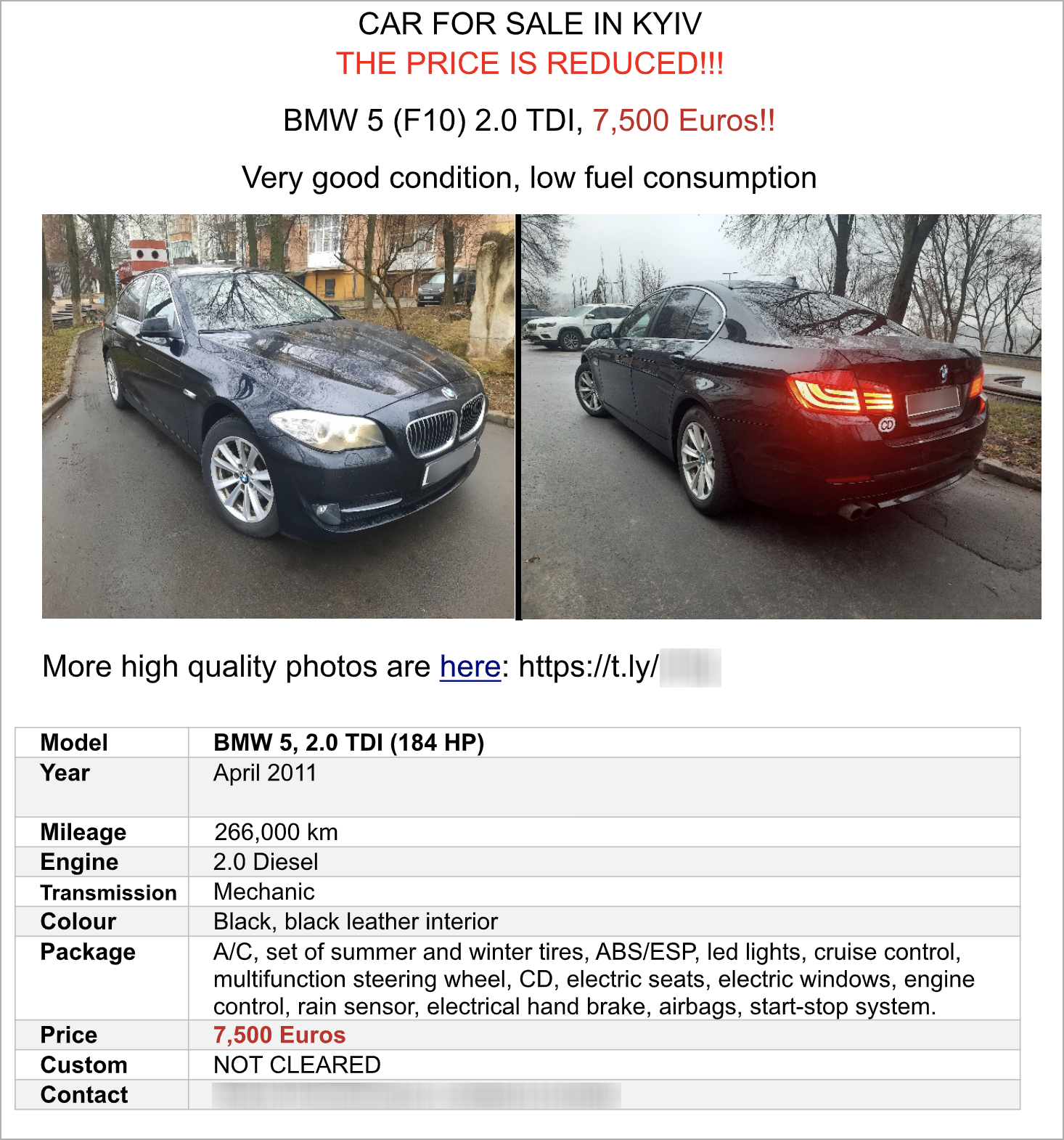
Malicious flyer sent by APT29 (Unit 42)
When the recipients click on the "more high-quality photos" link embedded in the malicious document, they are redirected to an HTML page that delivers malicious ISO file payloads via HTML smuggling.
HTML smuggling is a technique used in phishing campaigns that use HTML5 and JavaScript to hide malicious payloads in encoded strings in an HTML attachment or webpage. These strings are then decoded by a browser when a user opens the attachment or clicks a link.
Using this technique helps to evade security software as the malicious code is obfuscated and only decoded on rendering in the browser.
The ISO file contains what appears to be nine PNG images but are, in reality, LNK files that trigger the infection chain shown in the diagram below.
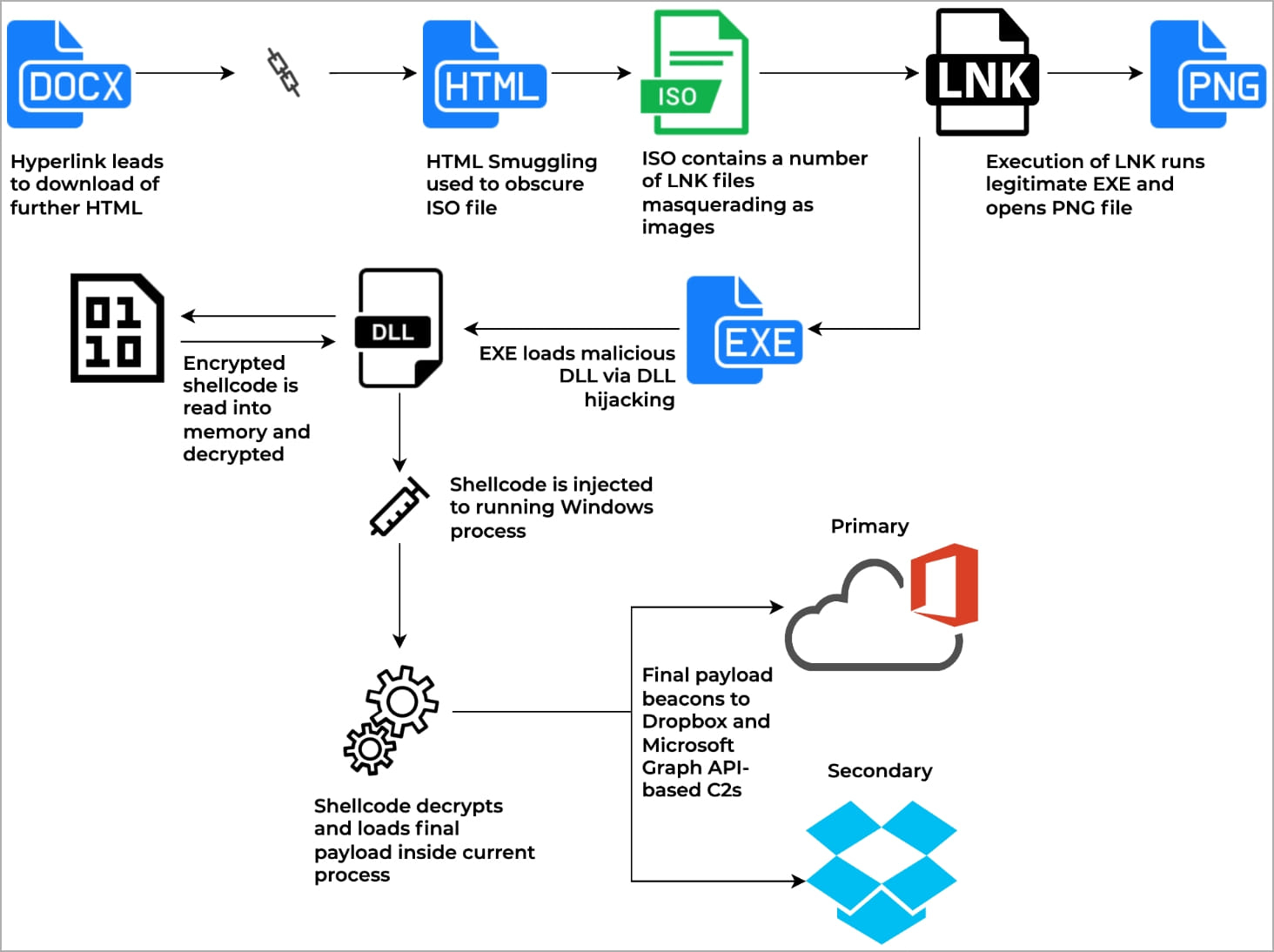
Observed infection chain (Unit 42)
When the victim opens any of the LNK files posing as PNG images, they launch a legitimate executable that uses DLL side-loading to inject shellcode into the current process in memory.
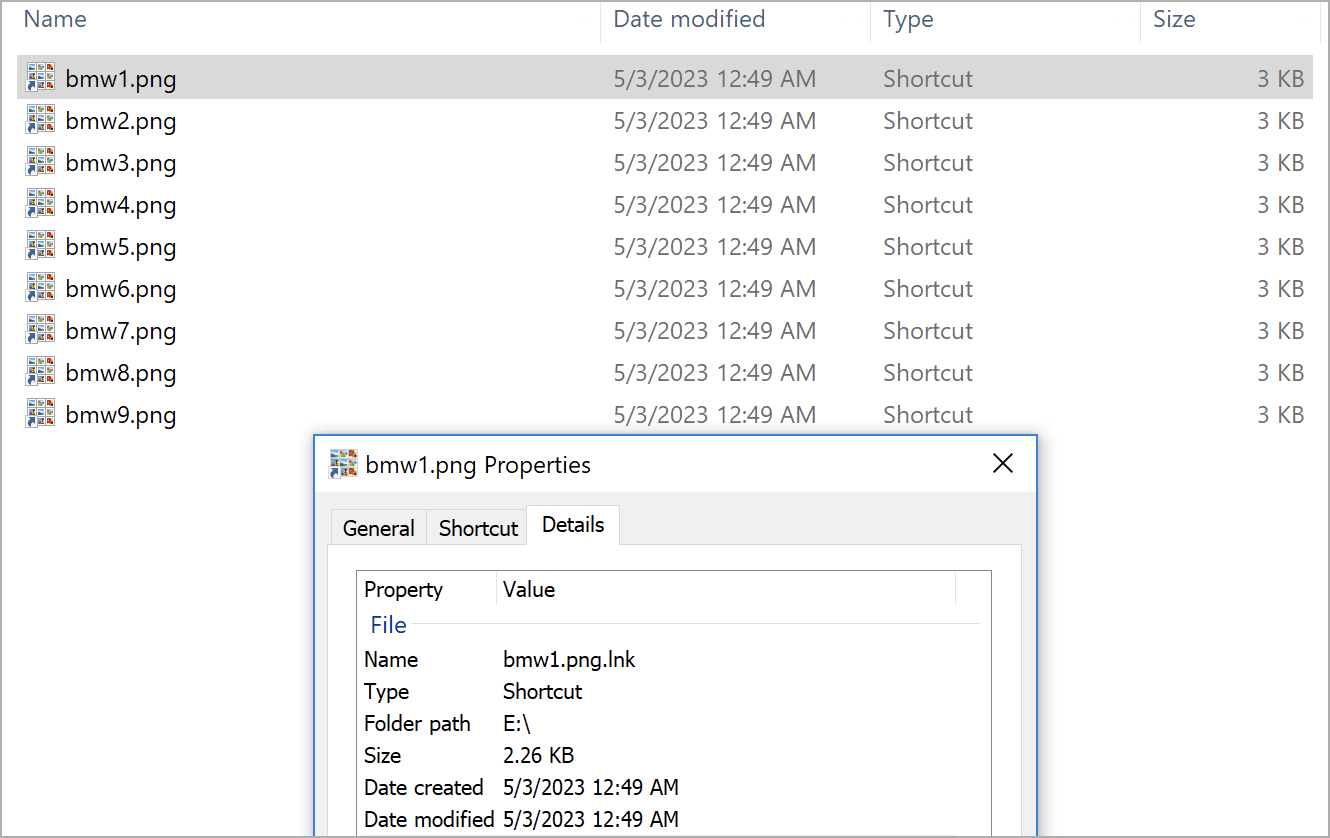
Fake PNG files contained in the ISO archive (Unit 42)
Unit 42 reports that this campaign has targeted at least 22 of the 80 foreign missions in Kyiv, including those of the United States, Canada, Turkey, Spain, Netherlands, Greece, Estonia, and Denmark. However, the infection rate remains unknown.
Roughly 80% of the email addresses that received the malicious flyer were publicly available online, while APT29 must have sourced the other 20% through account compromise and intelligence collection.
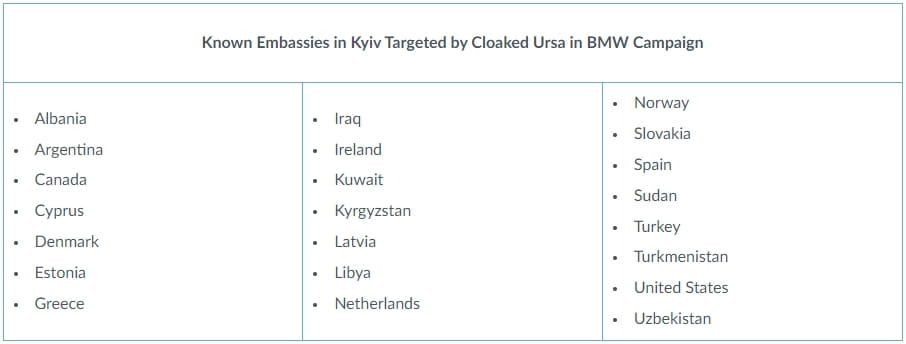
Targeted embassies in Ukraine (Unit 42)
Another recent example of APT29's readiness to exploit real-world incidents for phishing is a PDF sent to the Turkish Ministry of Foreign Affairs (MFA) earlier in 2023, guiding humanitarian assistance for the earthquake that struck southern Turkey in February.
Unit 42 comments that the malicious PDF was likely shared among MFA's employees and forwarded to other Turkish organizations, as the attack took advantage of the excellent timing.
As the conflict in Ukraine persists and evolving developments within NATO threaten to alter the geopolitical landscape, Russian cyber espionage groups are expected to continue and even intensify their efforts to target diplomatic missions.



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.