An amalgam of multiple state-sponsored threat groups from China may have been behind a string of targeted attacks against Russian federal executive authorities in 2020.
The latest research, published by Singapore-headquartered company Group-IB, delves into a piece of computer virus called "Webdav-O" that was detected in the intrusions, with the cybersecurity firm observing similarities between the tool and that of popular Trojan called "BlueTraveller," that's known to be connected to a Chinese threat group called TaskMasters and deployed in malicious activities with the aim of espionage and plundering confidential documents.
"Chinese APTs are one of the most numerous and aggressive hacker communities," researchers Anastasia Tikhonova and Dmitry Kupin said. "Hackers mostly target state agencies, industrial facilities, military contractors, and research institutes. The main objective is espionage: attackers gain access to confidential data and attempt to hide their presence for as long as possible."
The report builds on a number of public disclosures in May from Solar JSOC and SentinelOne, both of which disclosed a malware called "Mail-O" that was also observed in attacks against Russian federal executive authorities to access the cloud service Mail.ru, with SentinelOne tying it to a variant of another well-known malicious software called "PhantomNet" or "SManager" used by a threat actor dubbed TA428.
"The main goal of the hackers was to completely compromise the IT infrastructure and steal confidential information, including documents from closed segments and email correspondence of key federal executive authorities," Solar JSOC noted, adding the "cybercriminals ensured themselves a high level of secrecy through the use of legitimate utilities, undetectable malware, and a deep understanding of the specifics of the work of information protection tools installed in government bodies."
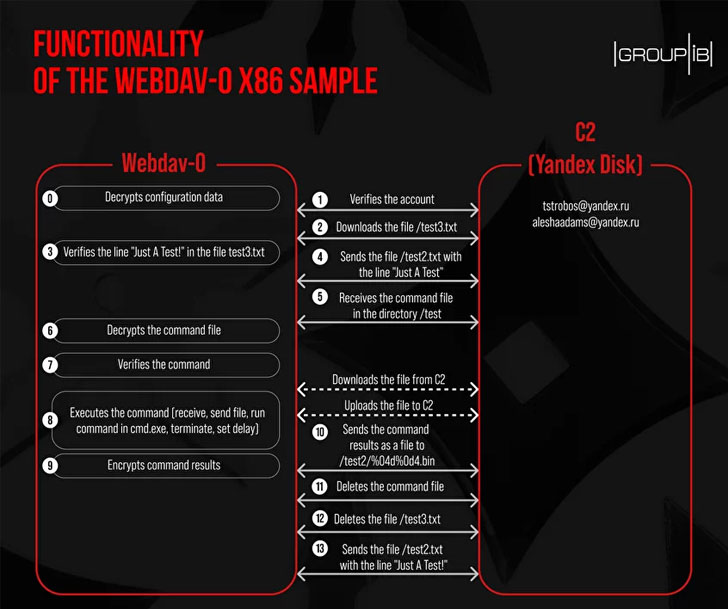
Group-IB's analysis centers on a Webdav-O sample that was uploaded to VirusTotal in November 2019 and the overlaps it shares with the malware sample detailed by Solar JSOC, with the researchers finding the latter to be a newer, partially improvised version featuring added capabilities. The detected Webdav-O sample has also been linked to the BlueTraveller trojan, citing source code similarities and the manner in which commands are processed.
What's more, further investigation into TA428's toolset has revealed numerous commonalities between BlueTraveller and a nascent malware strain named "Albaniiutas" that was attributed to the threat actor in December 2020, implying that not only is Albaniiutas an updated variant of BlueTraveller, but also that Webdav-O malware is a version of BlueTraveller.
"It is noteworthy that Chinese hacker groups actively exchange tools and infrastructure, but perhaps it is just the case here," the researchers said. "This means that one Trojan can be configured and modified by hackers from different departments with different levels of training and with various objectives."
"Either both Chinese hacker groups (TA428 and TaskMasters) attacked Russian federal executive authorities in 2020 or that there is one united Chinese hacker group made up of different units."
- Karlston
-

 1
1


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.