A pro-Russian group created a crowdsourced project called 'DDOSIA' that pays volunteers launching distributed denial-of-service (DDOS) attacks against western entities.
DDoS attacks typically don’t have any security repercussions for the target but can cause a lot of damage by generating service outages. Depending on the target, the impact can extend beyond financial losses.
Because DDoS attacks are easy to organize, simple to carry out, and still carry a punch, they have been the de-facto weapon of hacktivists on both sides of the Russian-Ukrainian war.
Introducing a financial incentive is a new strategy, researchers at cybersecurity company Radware say in a report shared with BleepingComputer.
In hacktivist DDoS attacks, volunteers don't get a monetary reward. Joining the cause is normally what they're in for. With the financial incentive added, DDOSIA attracts attackers that don't necessarily support the cause.
DDOSIA operators
Project DDOSIA was launched in mid-August by a group named “NoName057(16)” that had emerged in March 2022. The group was first publicly documented in a report from cybersecurity firm Avast in early September.
Avast highlighted the presence of a DDoS module downloaded by ‘Bobik’ - a remote access trojan (RAT) discovered in 2020 that was being dropped by RedLine information stealer.
Over three months of monitoring, between June and September, Avast concluded that NoName057(16) has been involved in DDoS-ing Ukrainian organizations but was successful in just 40% of their attacks.
DDOSIA launched on Telegram, where the operators shared a link to a GitHub page containing instructions for prospective volunteers. The channel counts over 13,000 members today.
Throughout its existence, DDOSIA aligned with the targets set by the pro-Russian gang KillNet and contributed to the recent wave of DDoS attacks against large airports in the United States.
Getting paid for DDoS power
Volunteers for DDOSIA need to register through Telegram to receive a ZIP archive with the malware (“dosia.exe”), which contains a unique ID for each user.
Members can link this ID to a cryptocurrency wallet and receive money for participating in DDoS attacks, payment being proportional to the firepower they provide.
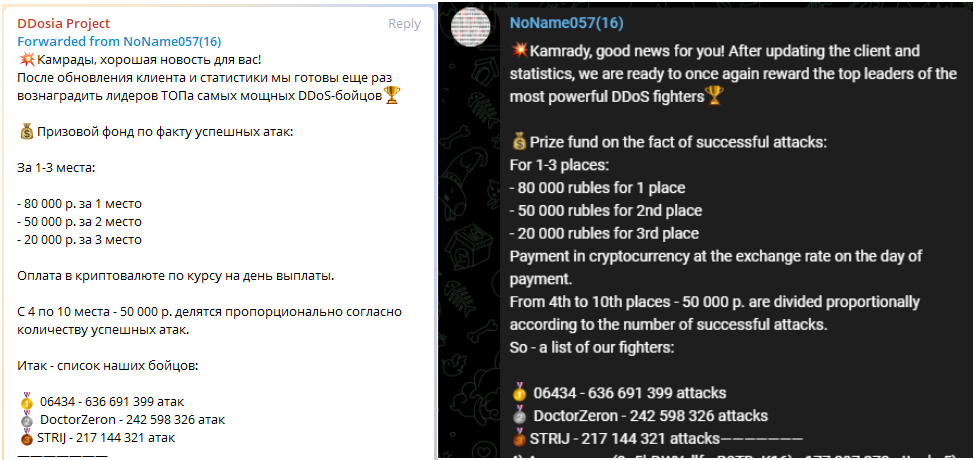
Top contributors in each attack wave receive 80,000 rubles ($1,250), second-place attackers receive 50,000 rubles ($800), and third-place contributors are compensated with 20,000 rubles ($300).
In the attacks against the U.S. airports, DDOSIA announced that they would distribute payouts to the top ten contributors, increasing the rewards for the contributors.
Currently, DDOSIA has about 400 members and remains a semi-closed invite-only group, regularly targeting a list of 60 military and education organizations in Ukraine.
The financial reward is an appealing incentive and could allow NoName057(16) not only draw in a mass of volunteers but also set a trend for other DDoS groups.
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.