REvil ransomware hits 200 companies in MSP supply-chain attack
A massive REvil ransomware attack affects multiple managed service providers and their clients through a reported Kaseya supply-chain attack.
Starting this afternoon, the REvil ransomware gang targeted approximately six large MSPs, with thousands of customers, through what appears to be a Kaseya VSA supply-chain attack.
Kaseya VSA is a cloud base MSP platform that allows providers to perform patch management and client monitoring.
Huntress Labs' John Hammond has told BleepingComputer that all of the affected MSPs are using Kaseya VSA and that they have proof that their customers are being encrypted as well.
"We have 3 Huntress partners that are impacted with roughly 200 businesses encrypted," Hammond told BleepingComputer.
Kaseya is warning all VSA customers to immediately shut down their VSA server to prevent the attack's spread while they investigate.
"We are experiencing a potential attack against the VSA that has been limited to a small number of on-premise customers only as of 2:00 PM EDT today," reads a warning on Kaseya's site.
"We are in the process of investigating the root cause of the incident with an abundance of caution but we recommend that you IMMEDIATELY shutdown your VSA server until you receive further notice from us."
"Its critical that you do this immediately, because one of the first things the attacker does is shutoff administrative access to the VSA."
REvil attack spread through autoupdate
BleepingComputer has been told by both Huntress' John Hammond and Sophos' Mark Loman that the attacks on MSPs appear to be a supply chain attack through Kaseya VSA.
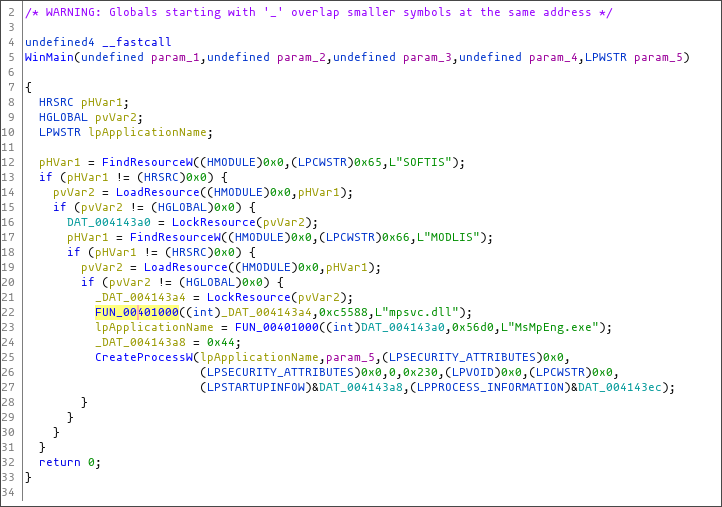
According to Hammond, an agent.crt file is dropped by Kaseya VSA, which is then decoded with the legitimate certutil.exe to extract an agent.exe file.
This agent.exe includes an embedded 'MsMpEng.exe' and 'mpsvc.dll,' with the DLL being the REvil encryptor. The MsMPEng.exe is used as a LOLBin to launch the DLL and encrypt the device through a trusted executable.
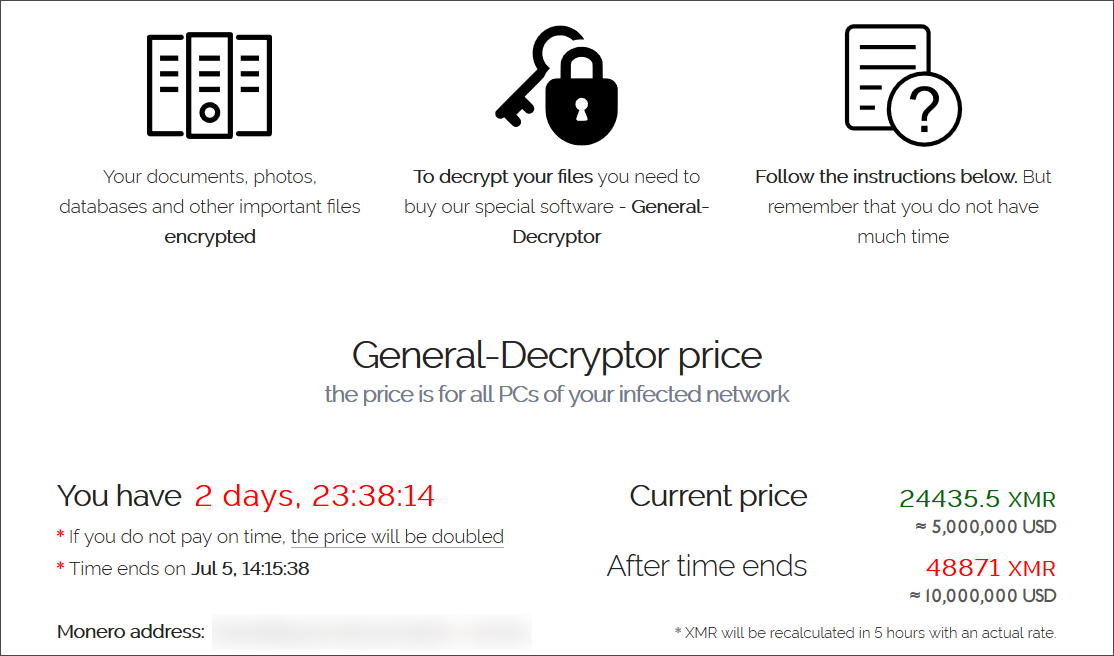
Ransomware gang demands a $5 million ransom
A sample of the REvil ransomware used in one of these attacks has been shared with BleepingComputer. However, it is unknown if this is the sample used for every victim or if each MSP received its own ransom demand.
The ransomware gang is demanding a $5,000,000 ransom to receive a decryptor from one of the samples.
While REvil is known to steal data before deploying the ransomware and encrypting devices, it is unknown if the attackers exfiltrated any files.
This is a developing story and will continue to be updated.
REvil ransomware hits 200 companies in MSP supply-chain attack
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.