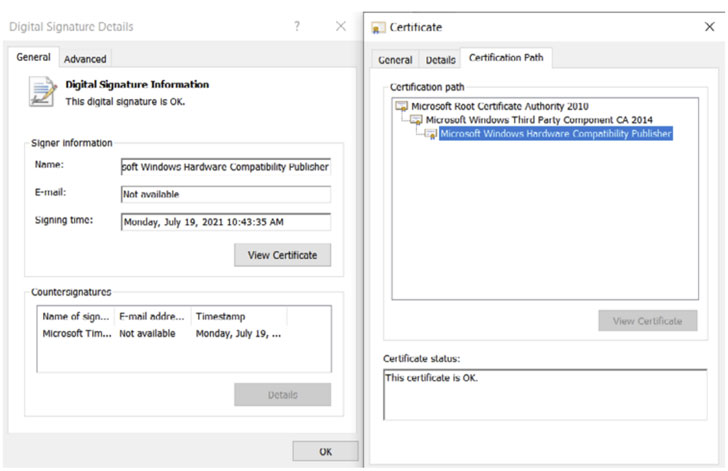
A newly identified rootkit has been found with a valid digital signature issued by Microsoft that's used to proxy traffic to internet addresses of interest to the attackers for over a year targeting online gamers in China.
Bucharest-headquartered cybersecurity technology company Bitdefender named the malware "FiveSys," calling out its possible credential theft and in-game-purchase hijacking motives. The Windows maker has since revoked the signature following responsible disclosure.
"Digital signatures are a way of establishing trust," Bitdefender researchers said in a white paper, adding "a valid digital signature helps the attacker navigate around the operating system's restrictions on loading third-party modules into the kernel. Once loaded, the rootkit allows its creators to gain virtually unlimited privileges."
Rootkits are both evasive and stealthy as they offer threat actors an entrenched foothold onto victims' systems and conceal their malicious actions from the operating system (OS) as well as from anti-malware solutions, enabling the adversaries to maintain extended persistence even after OS reinstallation or replacement of the hard drive.
In the case of FiveSys, the malware's main objective is to redirect and route internet traffic for both HTTP and HTTPS connections to malicious domains under the attacker's control via a custom proxy server. The rootkit operators also employ the practice of blocking the loading of drivers from competing groups using a signature blocklist of stolen certificates to prevent them from taking control of the machine.
"To make potential takedown attempts more difficult, the rootkit comes with a built-in list of 300 domains on the '.xyz' [top-level domain]," the researchers noted. "They seem to be generated randomly and stored in an encrypted form inside the binary."
The development marks the second time wherein malicious drivers with valid digital signatures issued by Microsoft through the Windows Hardware Quality Labs (WHQL) signing process have slipped through the cracks. In late June 2021, German cybersecurity company G Data disclosed details of another rootkit dubbed "Netfilter" (and tracked by Microsoft as "Retliften"), which, like FiveSys, also aimed at gamers in China.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.