Hundreds of databases on Amazon Relational Database Service (Amazon RDS) are exposing personal identifiable information (PII), new findings from Mitiga, a cloud incident response company, show.
"Leaking PII in this manner provides a potential treasure trove for threat actors – either during the reconnaissance phase of the cyber kill chain or extortionware/ransomware campaigns," researchers Ariel Szarf, Doron Karmi, and Lionel Saposnik said in a report shared with The Hacker News.
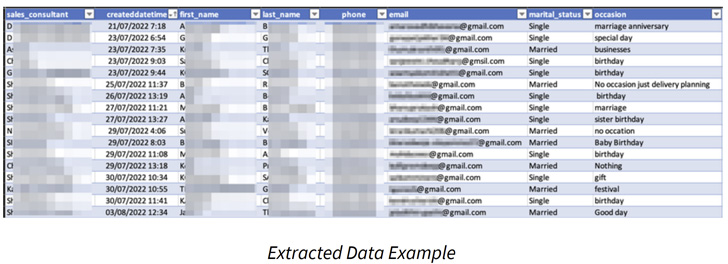
This includes names, email addresses, phone numbers, dates of birth, marital status, car rental information, and even company logins.
Amazon RDS is a web service that makes it possible to set up relational databases in the Amazon Web Services (AWS) cloud. It offers support for different database engines such as MariaDB, MySQL, Oracle, PostgreSQL, and SQL Server.
The root cause of the leaks stems from a feature called public RDS snapshots, which allows for creating a backup of the entire database environment running in the cloud and can be accessed by all AWS accounts.
"Make sure when sharing a snapshot as public that none of your private information is included in the public snapshot," Amazon cautions in its documentation. "When a snapshot is shared publicly, it gives all AWS accounts permission both to copy the snapshot and to create DB instances from it."
The Israeli company, which carried out the research from September 21, 2022, to October 20, 2022, said it found 810 snapshots that were publicly shared for varying duration, starting from a few hours to weeks, making them ripe for abuse by malicious actors.
Of the 810 snapshots, over 250 of the backups were exposed for 30 days, suggesting that they were likely forgotten.
Based on the nature of the information exposed, adversaries could either steal the data for financial gain or leverage it to get a better grasp of a company's IT environment, which could then act as a stepping stone for covert intelligence gathering efforts.
It's highly recommended that RDS snapshots are not publicly accessible in order to prevent potential leak or misuse of sensitive data or any other kind of security threat. It's also advised to encrypt snapshots where applicable.
- Karlston and aum
-

 2
2





Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.