Researchers Discover First Known Malware Targeting Windows Containers
Security researchers have discovered the first known malware, dubbed "Siloscope," targeting Windows Server containers to infect Kubernetes clusters in cloud environments.
"Siloscape is heavily obfuscated malware targeting Kubernetes clusters through Windows containers," said Unit 42 researcher Daniel Prizmant. "Its main purpose is to open a backdoor into poorly configured Kubernetes clusters in order to run malicious containers such as, but not limited to, cryptojackers."
Siloscape, first detected in March 2021, is characterized by several techniques, including targeting common cloud applications such as web servers to gain an initial foothold via known vulnerabilities, following which it leverages Windows container escape techniques to break out of the confines of the container and gain remote code execution on the underlying node.
A container is an isolated, lightweight silo for running an application on the host operating system. The malware's name — short for silo escape — is derived from its primary goal to escape the container, in this case, the silo. To achieve this, Siloscape uses a method called Thread Impersonation.
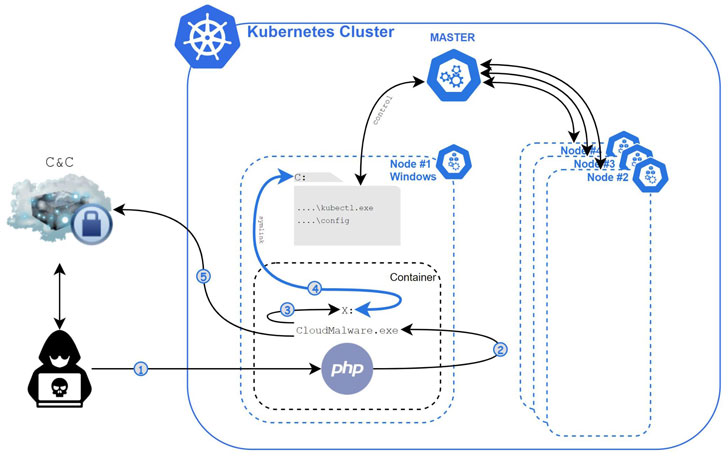
"Siloscape mimics CExecSvc.exe privileges by impersonating its main thread and then calls NtSetInformationSymbolicLink on a newly created symbolic link to break out of the container," said Prizmant. "More specifically, it links its local containerized X drive to the host's C drive."
Armed with this privilege, the malware then attempts to abuse the node's credentials to spread across the cluster, before anonymously establishing a connection to its command-and-control (C2) server using a Tor proxy for further instructions, including taking advantage of the computing resources in a Kubernetes cluster for cryptojacking and even exfiltrating sensitive data from applications running in the compromised clusters.
After gaining access to the C2 server, Unit 42 said it found 23 active victims, with the server hosting a total of 313 users. The campaign is said to have begun at least around Jan. 12, 2020, based on the creation date of the C2 server, suggesting that the malware could just be a small part of a larger campaign that started over a year ago.
"Unlike most cloud malware, which mostly focuses on resource hijacking and denial of service (DoS), Siloscape doesn't limit itself to any specific goal," Prizmant noted. "Instead, it opens a backdoor to all kinds of malicious activities." In addition to securely configuring Kubernetes clusters, it's also recommended to deploy Hyper-V containers if containerization is utilized as a form of the security boundary.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.