Nearly 71 million unique credentials stolen for logging into websites such as Facebook, Roblox, eBay, and Yahoo have been circulating on the Internet for at least four months, a researcher said Wednesday.
Troy Hunt, operator of the Have I Been Pwned? breach notification service, said the massive amount of data was posted to a well-known underground market that brokers sales of compromised credentials. Hunt said he often pays little attention to dumps like these because they simply compile and repackage previously published passwords taken in earlier campaigns.
Not your typical password dump
Some glaring things prevented Hunt from dismissing this one, specifically the contents indicating that nearly 25 million of the passwords had never been leaked before:
- 319 files totaling 104GB
- 70,840,771 unique email addresses
- 427,308 individual HIBP subscribers impacted
- 65.03 percent of addresses already in HIBP (based on a 1,000 random sample set)
“That last number was the real kicker,” Hunt wrote. “When a third of the email addresses have never been seen before, that's statistically significant. This isn't just the usual collection of repurposed lists wrapped up with a brand-new bow on it and passed off as the next big thing; it's a significant volume of new data. When you look at the above forum post the data accompanied, the reason why becomes clear: it's from ‘stealer logs’ or in other words, malware that has grabbed credentials from compromised machines.”
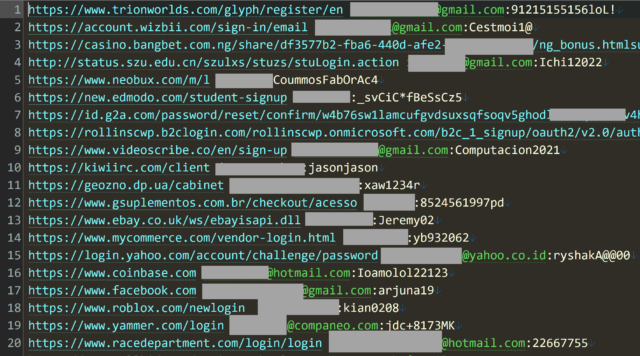
A redacted image that Hunt posted showing a small sample of the exposed credentials indicated that account credentials for a variety of sites were swept up. Sites included Facebook, Roblox, Coinbase, Yammer, and Yahoo. In keeping with the claim that the credentials were collected by a “stealer”—malware that runs on a victim’s device and uploads all user names and passwords entered into a login page—the passwords appear in plaintext. Account credentials taken in website breaches are almost always cryptographically hashed. (A sad aside: Most of the exposed credentials are weak and would easily fall to a simple password dictionary attack.)
Data collected by Have I Been Pwned indicates this password weakness runs rampant. Of the 100 million unique passwords amassed, they have appeared 1.3 billion times.
“To be fair, there are instances of duplicated rows, but there's also a massive prevalence of people using the same password across multiple different services and completely different people using the same password (there are a finite set of dog names and years of birth out there...),” Hunt wrote. “And now more than ever, the impact of this service is absolutely huge!”
Hunt confirmed the authenticity of the dataset by contacting people at some of the listed emails. They confirmed that the credentials listed there were—or at least once were—accurate. For added assurance, Hunt also checked a sample of the credentials to see if the email addresses were associated with accounts on the affected websites. All of them did. Some of Hunt’s users reported that the passwords appeared to be valid as of 2020 or 2021. Whatever the date of the passwords, it stands to reason that unless they’ve been updated, they remain valid. The underground market post advertising the dataset said it came from a breach dubbed naz.api that had been donated to a different site earlier.
Hunt said that a large percentage of the credentials came not from stealer malware as claimed, but from credential stuffing, a form of account-hijacking attack that collects large numbers of stolen account credentials from previous breaches. Hunt said credential stuffing sources explained how a password he used "pre-2011" landed in the dump.
"Some of this data does not come from malware and has been around for a significant period of time," he wrote. "My own email address, for example, accompanied a password not used for well over a decade and did not accompany a website indicating it was sourced from malware."
Making passwords safe
There are dozens of useful primers online explaining how to properly secure accounts. The two main ingredients to account security are: (1) choosing strong passwords and (2) keeping them out of the sight of prying eyes. This means:
- Creating a long, randomly generated password or passphrase. These passcodes should be at least 11 characters for passwords and for passphrases at least four words randomly chosen from a dictionary of no fewer than 50,000 entries. Bitwarden, a free, open-source password manager is a good choice and a great way for less experienced people to get started. Once a password is created, it should be stored in the password-manager vault.
- Preventing strong passwords from being compromised. This entails not entering passwords into phishing sites and keeping devices free of malware.
- Use two-factor authentication, preferably with a security key or authenticater app, whenever possible. This doubly applies to protecting the password manager with 2FA.
- Better yet, use passkeys, a new, industry-wide authentication standard that's immune to theft through stealer apps and credential phishing.
It’s also a good idea to either create an account with Have I Been Pwned? or periodically enter email addresses into the site search box to check if they appear in any breaches. To prevent abuse of the search, the site doesn’t log entered email addresses and no corresponding passwords are loaded with password data stored on the site. Have I Been Pwned also accepts a single email address at a time, except in certain cases. You can find more on the service and the security of using it here.
Have I Been Pwned also allows users to search its database for specific passwords. More about k-anonymity and other measures Hunt uses to prevent password exposure and abuse of his service is here.
This post has been updated to correct inferences about how Hunt's password ended up in the dataset.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)

Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.