A growing number of ransomware groups are adopting a new tactic that helps them encrypt their victims' systems faster while reducing the chances of being detected and stopped.
This tactic is called intermittent encryption, and it consists of encrypting only parts of the targeted files' content, which would still render the data unrecoverable without using a valid decryptor+key.
For example, by skipping every other 16 bytes of a file, the encryption process takes almost half of the time required for full encryption but still locks the contents for good.
Additionally, because the encryption is milder, automated detection tools that rely on detecting signs of trouble in the form of intense file IO operations are more likely to fail.
"What the cool kids use."
SentinelLabs has posted a report examining a trend started by LockFile in mid-2021 and now adopted by the likes of Black Basta, ALPHV (BlackCat), PLAY, Agenda, and Qyick.
These groups actively promote the presence of intermittent encryption features in their ransomware family to entice affiliates to join the RaaS operation.
"Notably, Qyick features intermittent encryption, which is what the cool kids are using as you read this. Combined with the fact that is written in Go, the speed is unmatched," describes a Qyick advertisement on hacking forums.
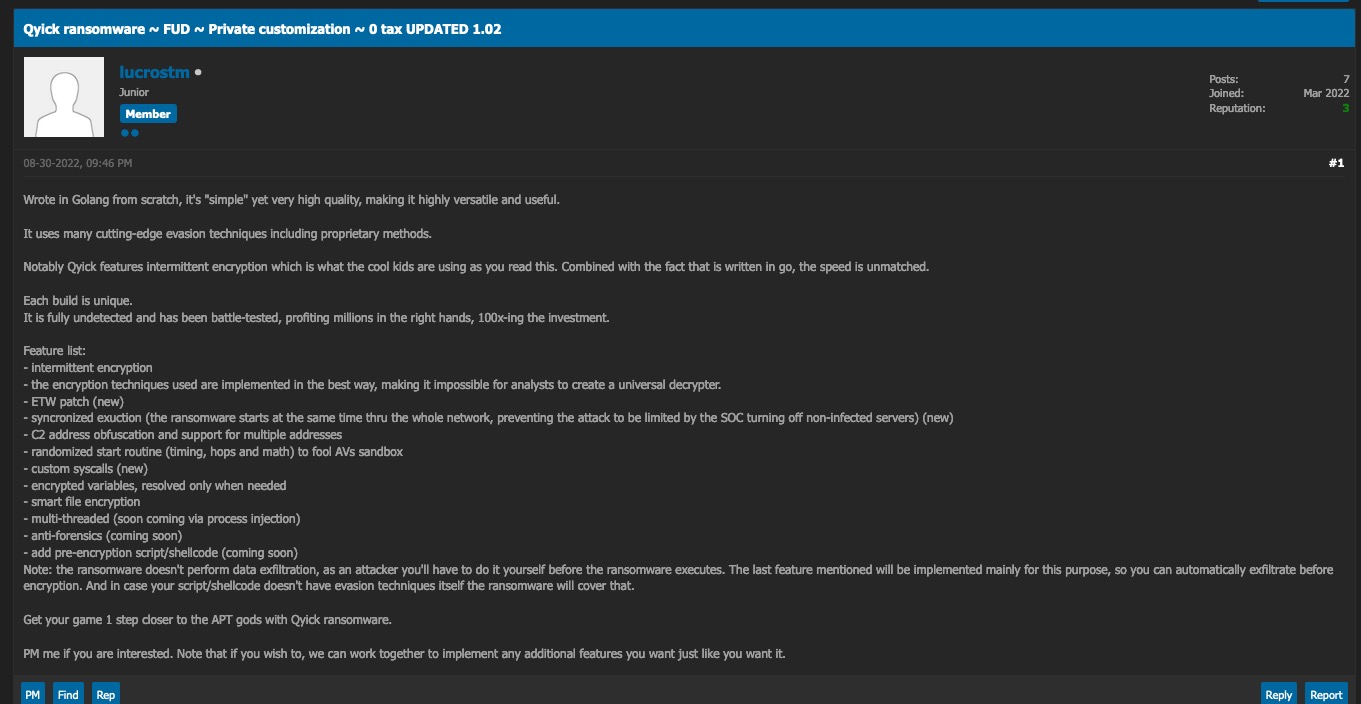
Agenda ransomware offers intermittent encryption as an optional and configurable setting. The three possible partial encryption modes are:
- skip-step [skip: N, step: Y] - Encrypt every Y MB of the file, skipping N MB.
- fast [f: N] - Encrypt the first N MB of the file.
- percent [n: N; p:P] - Encrypt every N MB of the file, skipping P MB, where P equals P% of the total file size.
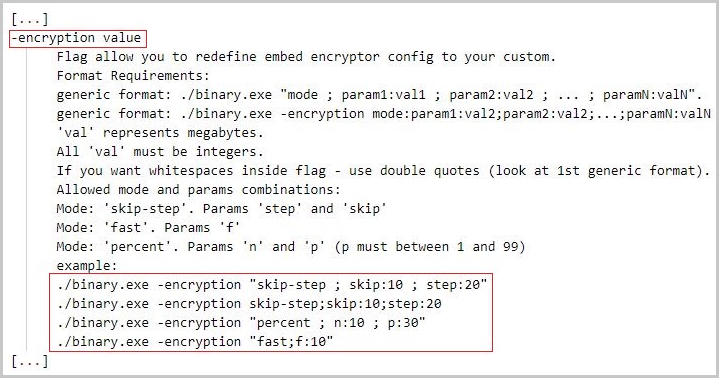
BlackCat's implementation of intermittent encryption also gives operators configuration choices in the form of various byte-skipping patterns.
For example, the malware can encrypt only the first bytes of a file, follow a dot pattern, a percentage of file blocks, and also has an "auto" mode that combines multiple modes for a more tangled result.
The recent emergence of the PLAY ransomware via a high-profile attack against Argentina's Judiciary of Córdoba was also backed by the rapidness of intermittent encryption.
PLAY doesn't give configuration options, but instead, it just breaks the file into 2, 3, or 5 chunks, depending on the file size, and then encrypts every other chunk.
Finally, Black Basta, one of the biggest names in the space at the moment, also doesn't give operators the option to pick among modes, as its strain decides what to do based on the file size.
For small files below 704 bytes in size, it encrypts all content. For files between 704 bytes and 4 KB, it encrypts 64 bytes and skips 192 bytes in between.
If the file size exceeds 4 KB, Black Basta's ransomware reduces the space size of untouched intervals to 128 bytes, while the size of the encrypted portion remains 64 bytes.
Intermittent encryption outlook
Intermittent encryption seems to have significant advantages and virtually no downsides, so security analysts expect more ransomware gangs to adopt this approach shortly.
LockBit's strain is already the quickest out there in terms of encryption speeds, so if the gang adopted the partial encryption technique, the duration of its strikes would be reduced to a couple of minutes.
Of course, encryption is a complex matter, and the implementation of intermittent encryption must be done correctly to ensure that it won't result in easy data recoveries by the victims.
Right now, BlackCat's implementation is the most sophisticated, while that of Qyick remains unknown since malware analysts have not yet analyzed samples of the new RaaS.
Source: Bleeping Computer
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.