Someone is flooding Cobalt Strike servers operated by former members of the Conti ransomware gang with anti-Russian messages to disrupt their activity.
The operators of Conti ransomware completed turning off their internal infrastructure in May this year but its members have dispersed to other ransomware gangs, such as Quantum, Hive, and BlackCat.
However, former Conti members continue to use the same Cobalt Strike infrastructure to conduct new attacks under other ransomware operations.
Server flood
Someone is now tracking the TeamServers (C2) used by ransomware actors to control the Cobalt Strike (CS) Beacon payloads on compromised hosts (clients), which allow lateral movement on the network.
When flooding the CS servers, these people are using the username “Stop Putin!” on multiple computers and changing their computer name to various messages, such as “Stop the war!,” “15000+ dead Russian soldiers!,” and “Be a Russian patriot!”
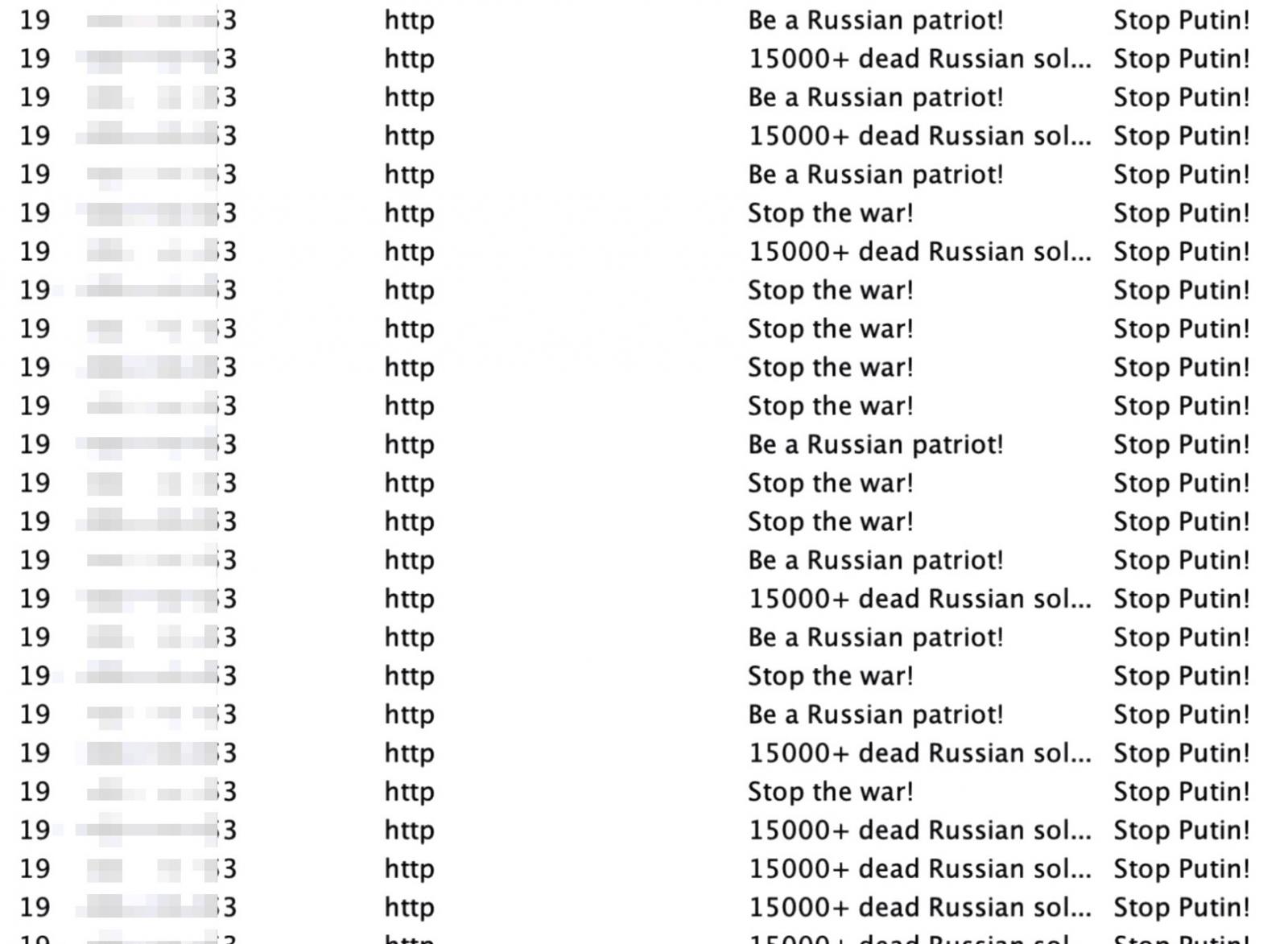
Vitali Kremez, the CEO of cyber intelligence company Advanced Intelligence (AdvIntel), told BleepingComputer that whoever is running these attacks initially targeted at least four Cobalt Strike servers allegedly controlled by ex-Conti members.
The researcher says that the messages are flooding the servers at a high rate of about two every second.
As an effect of this large number of pings, TeamServer’s Java application is overloaded and activity is disrupted in a similar way a denial-of-service (DoS) condition would.
Running Cobalt Strike TeamServer from a Java application was possible in versions of the toolkit up to 4.6, released this year in April. In more recent releases, the component runs from an executable image (TeamServerImage).
Kremez says whoever is behind this activity is constantly targeting Cobalt Strike servers believed to be operated by previous Conti ransomware members, resuming the flood whenever a new server is discovered.
Turning the tables on cybercriminals
It is unclear who is behind these messages (it could be anyone from a security researcher, to law enforcement agencies, to a cybercriminal with a grudge for siding with Russia) but it looks like they’re keeping the threat actor busy.
Disrupting ransomware gangs’ activity with denial-of-service has happened before, the LockBit operation being a recent target, allegedly for encrypting systems belonging to digital security company Entrust.
The attack was serious enough for LockBit to shut down its leak sites and start reorganizing its infrastructure. In the meantime, none of the data the gang published was available.
The hackers blamed the DDoS on Entrust since the HTTPS requests came with the message to delete the company’s data.
However, the disruption was temporary and the ransomware actor came online with stronger infrastructure allowing them to keep the stolen data available even when facing distributed denial-of-service (DDoS) attacks.
- aum and Karlston
-

 2
2




Recommended Comments
There are no comments to display.