QNAP has fixed a critical zero-day vulnerability exploited by security researchers on Thursday to hack a TS-464 NAS device during the Pwn2Own Ireland 2024 competition.
Tracked as CVE-2024-50388, the security flaw is caused by an OS command injection weakness in HBS 3 Hybrid Backup Sync version 25.1.x, the company's disaster recovery and data backup solution.
"An OS command injection vulnerability has been reported to affect HBS 3 Hybrid Backup Sync. If exploited, the vulnerability could allow remote attackers to execute arbitrary commands," QNAP said in a Tuesday security advisory.
The company has addressed the security bug in HBS 3 Hybrid Backup Sync 25.1.1.673 and later.
To update HBS 3 on your NAS device, log in to QTS or QuTS hero as an administrator, open the App Center, and search for "HBS 3 Hybrid Backup Sync".
If an update is available, click "Update". However, the "Update" button will not be available if your HBS 3 Hybrid Backup Sync is already up-to-date.
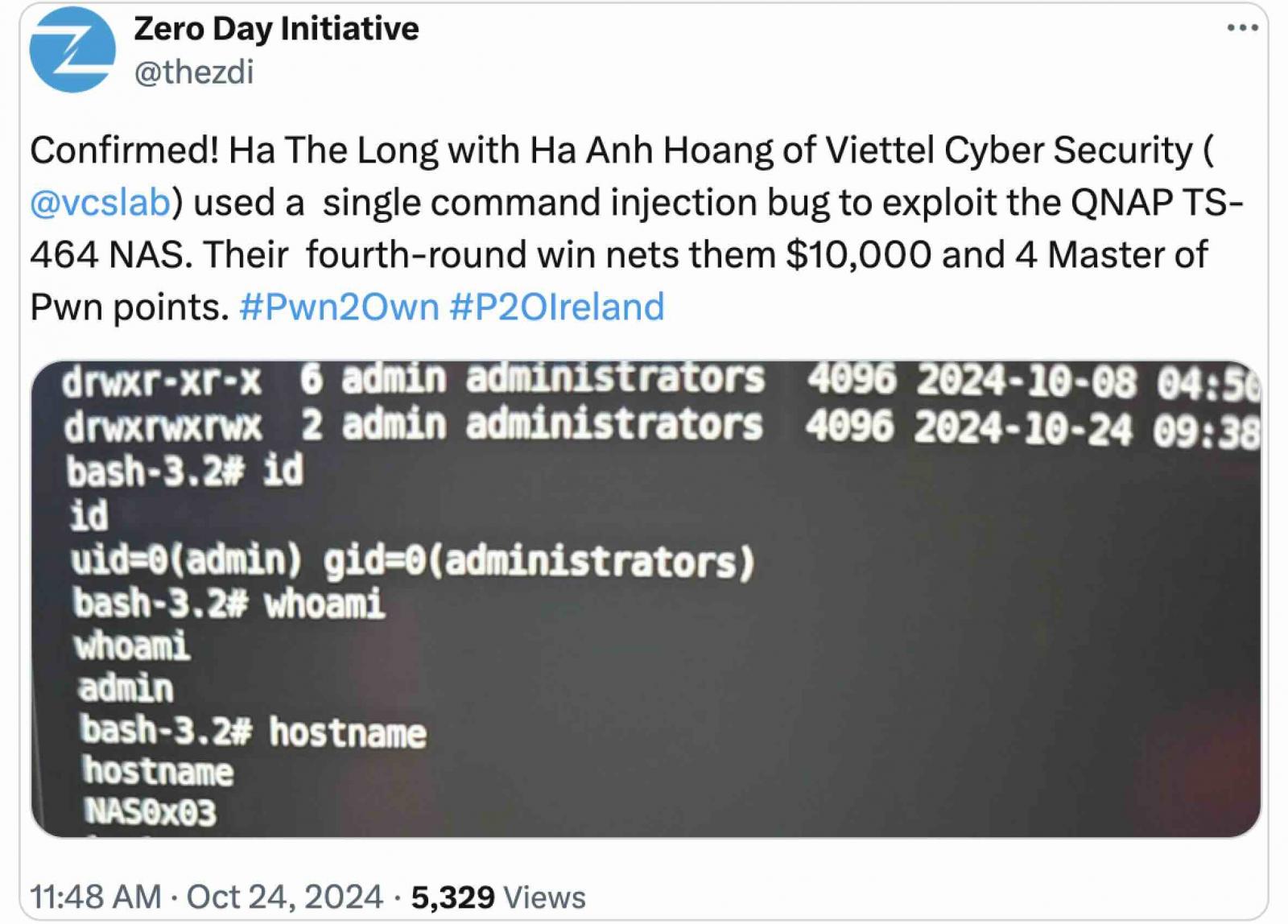
The zero-day was patched five days after enabling Ha The Long and Ha Anh Hoang of Viettel Cyber Security to execute arbitrary code and gain admin privileges on the third day of Pwn2Own Ireland 2024.
However, after the Pwn2Own contest, vendors usually take their time to release security patches, seeing that they're given 90 days until Trend Micro's Zero Day Initiative publishes details on security bugs demoed and disclosed during the contest.
Team Viettel won Pwn2Own Ireland 2024, which ended after four days of competition, on Friday, October 25. More than $1 million in prizes were awarded to hackers who disclosed over 70 unique zero-day vulnerabilities.
Three years ago, QNAP also removed a backdoor account in its Hybrid Backup Sync solution (CVE-2021-28799), which was exploited together with an SQL Injection vulnerability in Multimedia Console and the Media Streaming Add-On(CVE-2020-36195) to deploy Qlocker ransomware onto Internet-exposed NAS devices to encrypt files.
QNAP devices are a popular target among ransomware gangs because they store sensitive personal files, making them perfect leverage for forcing victims to pay a ransom to decrypt data.
In June 2020, QNAP warned of eCh0raix ransomware attacks exploiting Photo Station app security flaws. One year later, eCh0raix (aka QNAPCrypt) returned in attacks exploiting known vulnerabilities and brute-forcing accounts with weak passwords.
QNAP also alerted customers in September 2020 of AgeLocker ransomware attacks targeting publicly exposed NAS devices running older and vulnerable Photo Station versions.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
2023: Over 5,800 news posts | 2024 (till end of September): 4,292 news posts
RIP Matrix | Farewell my friend ![]()
- phen0men4
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.