Phishing emails distributing the QBot malware are using a DLL hijacking flaw in the Windows 10 Control Panel to infect computers, likely as an attempt to evade detection by security software.
DLL hijacking is a common attack method that takes advantage of how Dynamic Link Libraries (DLLs) are loaded in Windows.
When a Windows executable is launched, it will search for any DLL dependencies in the Windows search path. However, if a threat actor creates a malicious DLL using the same name as one of the program's required DLLs and stores it in the same folder as the executable, the program would load that malicious DLL instead and infect the computer.
QBot, also known as Qakbot, is a Windows malware that started as a banking trojan but evolved into a full-featured malware dropper. Ransomware gangs, including Black Basta, Egregor, and Prolock, also use the malware to gain initial access to corporate networks.
In July, security researcher ProxyLife discovered that threat actors were exploiting a DLL hijacking vulnerability in the Windows 7 Calculator to install the QBot malware.
This week, ProxyLife told BleepingComputer that attackers have switched to using a DLL hijacking flaw in the Windows 10 Control Panel executable, control.exe.
In a phishing campaign seen by ProxyLife, the threat actors use stolen reply-chain emails to distribute an HTML file attachment that downloads a password-protected ZIP archive with an ISO file inside.
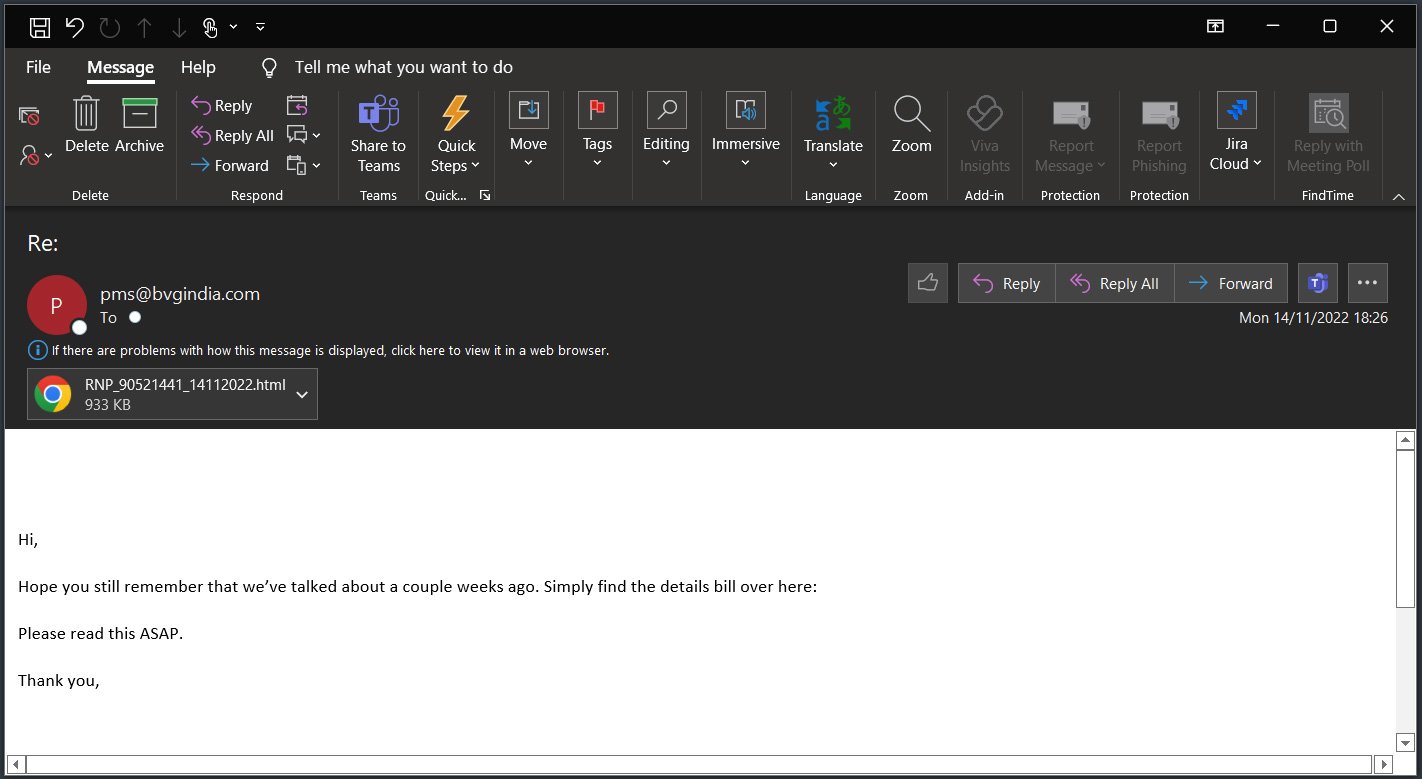
QBot phishing email in new campaign - Source: BleepingComputer
The HTML file, named similar to 'RNP_[number]_[number].html, displays an image pretending to be Google Drive and a password for a ZIP archive that is downloaded automatically, as shown below.
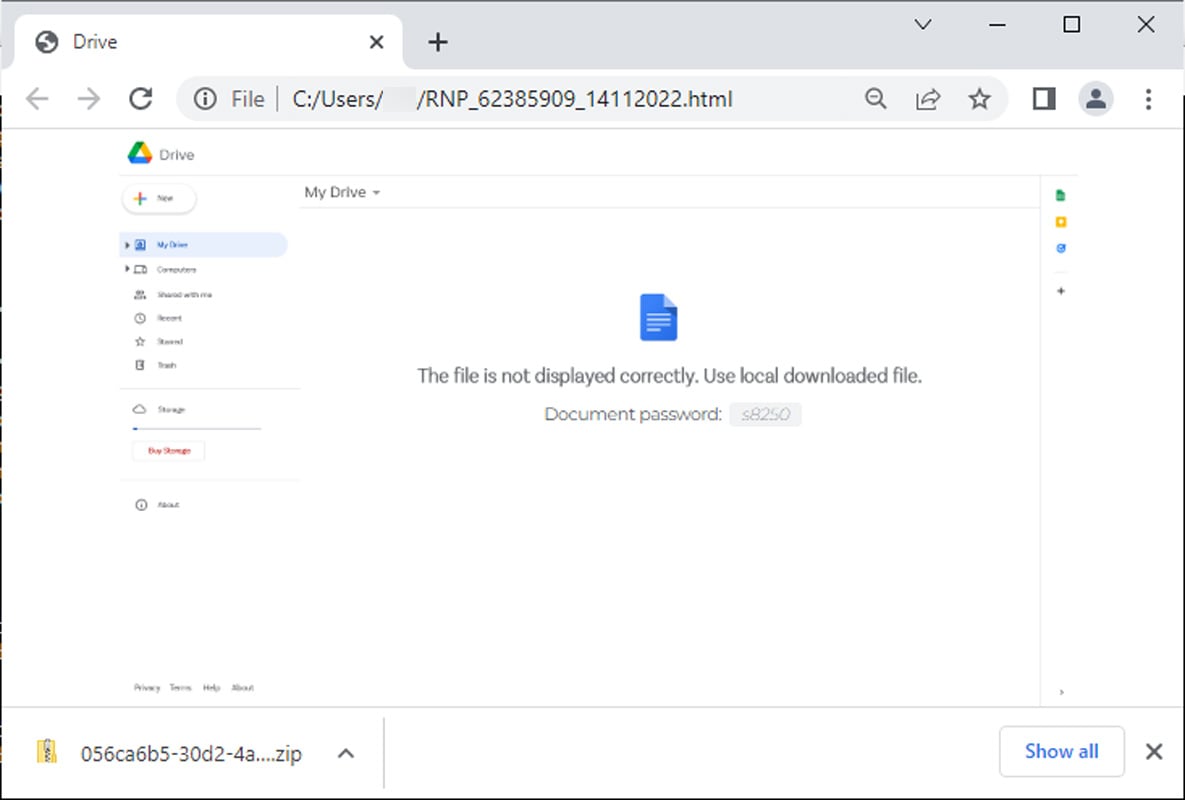
HTML attachment on QBot spam emails - Source: BleepingComputer
This ZIP archive contains an ISO disk image that, when double-clicked, will automatically open in a new drive letter in Windows 10 and later.
This ISO file contains a Windows Shortcut (.LNK) file, a ‘control.exe’ (Windows 10 Control Panel) executable, and two DLL files named edputil.dll (used for DLL hijack) and msoffice32.dll (QBot malware).
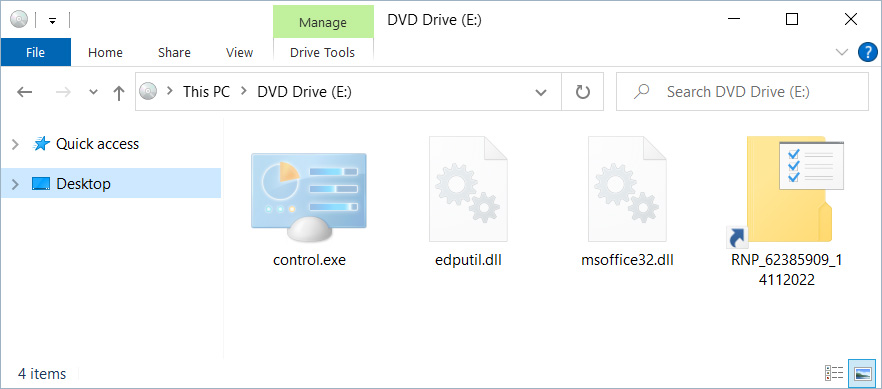
Contents of the ISO image - Source: BleepingComputer
The Windows shortcut (.LNK) included in the ISO uses an icon that tries to make it look like a folder.
However, when a user attempts to open this fake folder, the shortcut launches the Windows 10 Control Panel executable, control.exe, which is stored in the ISO file, as shown below.
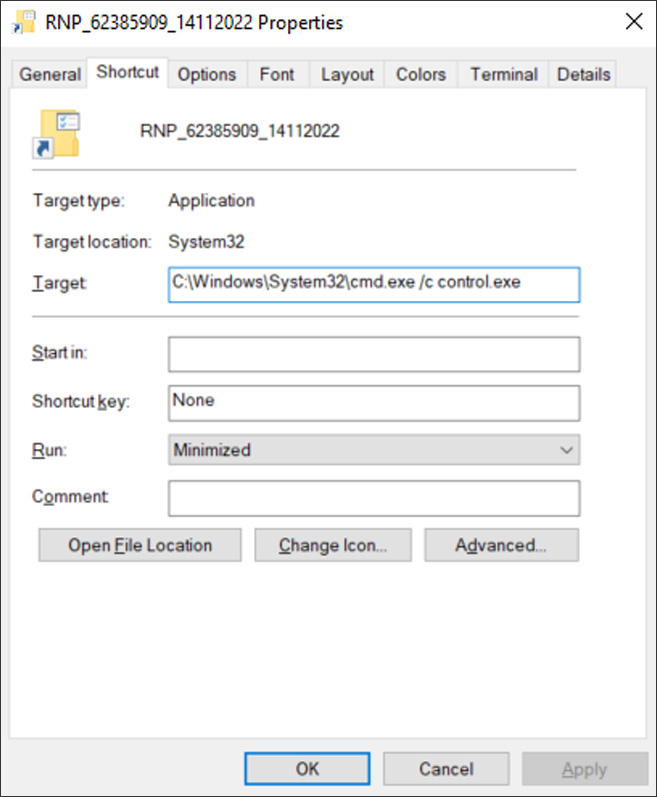
Windows shortcut that triggers the QBot infection - Source: BleepingComputer
When control.exe is launched, it will automatically attempt to load the legitimate edputil.dll DLL, which is located in the C:\Windows\System32 folder. However, it does not check for the DLL in specific folders and will load any DLL with the same name if placed in the same folder as the control.exe executable.
As the threat actors are bundling a malicious edputil.dll DLL in the same folder as control.exe, that malicious DLL will be loaded instead.
Once loaded, the malicious edputil.dll DLL infects the device with the QBot malware (msoffice32.dll) using the regsvr32.exe msoffice32.dll command.
By installing QBot through a trusted program like the Windows 10 Control Panel, security software may not flag the malware as malicious, allowing it to evade detection.
QBot will now quietly run in the background, stealing emails for use in phishing attacks and downloading additional payloads such as Brute Ratel or Cobalt Strike.
Brute Ratel and Cobalt Strike are post-exploitation toolkits that threat actors use to gain remote access to corporate networks.
This remote access commonly leads to corporate data theft and ransomware attacks.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.