A previously unknown ‘ARCrypter’ ransomware that compromised key organizations in Latin America is now expanding its attacks worldwide.
Threat actors behind the new ransomware family attacked a government agency in Chile last August, targeting both Linux and Windows systems and appending the “.crypt” extension on encrypted files.
Back then, Chilean threat analyst Germán Fernández told BleepingComputer that the strain appeared entirely new, not connected to any known ransomware families.
Researchers at BlackBerry have confirmed this via a report that identifies the family as ARCrypter and links it to a second attack against the Colombia National Food and Drug Surveillance Institute (Invima) in October.
BlackBerry also warns that ARCrypter is now expanding its operations outside Latin America and targeting various organizations worldwide, including China and Canada.
BleepingComputer confirmed this expansion, also seeing ARCrypter victims in Germany, USA, and France.
The ransom demands vary and get as low as $5,000 in some cases seen by BleepingComputer, so ARCrypter operates as a mid-tier ransomware actor.
ARCrypter details
BlackBerry says the first samples of ARCrypter appeared in early August 2022, a few weeks before the Chile attack.
The attack vector remains unknown, but the analysts were able to locate two AnonFiles URLs that are used as remote resources for fetching a “win.zip” archive containing “win.exe.”
The executable is a dropper file that contains the resources BIN and HTML. HTML holds the ransom note data, while BIN contains encrypted data that requires a password.
.png)
The ransom note, generated prior to encryption (BleepingComputer)
If a password is provided, BIN will create a random directory on the compromised machine to store the second-stage payload, which is named using random alphanumeric characters.
“While we were unable to identify the correct decryption key used for decryption of the BIN resource, we believe with a high degree of certainty that the second payload is the ARCrypter ransomware,” says BlackBerry in the report.
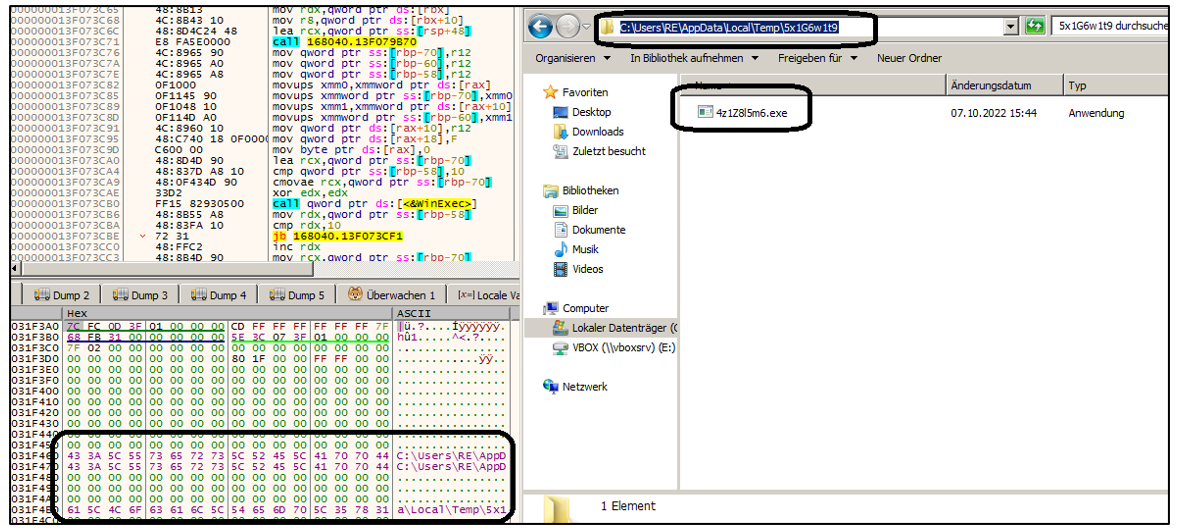
The randomly-named payload dropped on a newly created folder (BlackBerry)
The ARCrypter payload then creates persistence by adding the following registry key:
“HKLM\Software\Microsoft\Windows\CurrentVersion\Run\SecurityUpdate”
Next, the malware deletes all Shadow Volume Copies to prevent easy data restoration, modifies network settings to secure stable connectivity, and then encrypts all files except for the types shown below.
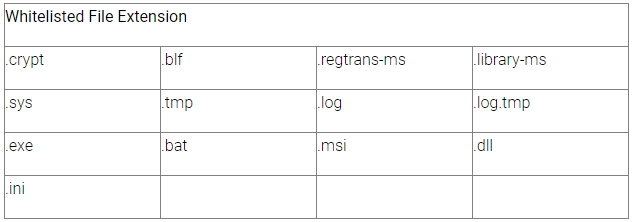
File types excluded from encryption (BlackBerry)
Files in critical locations like “Boot” and “Windows” folders are also skipped to avoid rendering the system completely unusable.
Apart from the ‘.crypt’ extension, encrypted files will show an ‘ALL YOUR FILES HAS BEEN ENCRYPTED’ message on the file manager, thanks to modifications to the following Registry keys:
HKCU\Control Panel\International\sShortDate
HKLM\SYSTEM\ControlSet001\Control\CommonGlobUserSettings\Control Panel\International\sShortDate
.png)
Files encrypted by ARCrypter (BlackBerry)
While the threat actors claim to steal data during their attacks, the ransomware operation does not currently have a data leak site that they use to publish data for unpaid victims.
At this time, little is known about the operators of ARCrypter, their origin, language, and potential links to other ransomware gangs.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.