Phishing attacks are now using automated chatbots to guide visitors through the process of handing over their login credentials to threat actors.
This approach automates the process for attackers and gives a sense of legitimacy to visitors of the malicious sites, as chatbots are commonly found on websites for legitimate brands.
This new development in phishing attacks was discovered by researchers at Trustwave, who shared the report with Bleeping Computer before publication.
It starts with an email
The phishing process begins with an email claiming to contain information about the delivery of a parcel, masquerading as the DHL shipping brand.
.png)
Clicking on the 'Please follow our instructions' button in the email loads a PDF file that contains links to the phishing site. The threat actors display the phishing links in the PDF document to bypass email security software.
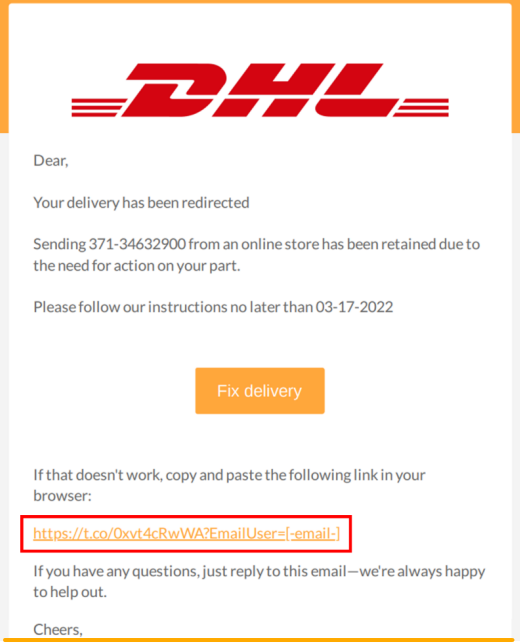
However, the URL button (or the link) in the PDF takes the victim to a phishing site (dhiparcel-management[.]support-livechat[.]24mhd[.]com) where they are supposed to resolve issues causing a package to be undeliverable.
This is where the chatbot takes over.
A chatbot steals your credentials
When the phishing page loads, visitors are greeted with a web chat explaining why the package could not be delivered instead of being shown a fake login form commonly used to steal credentials.
This webchat explains that the package's label was damaged, preventing its delivery. The webchat also displays a photo of the alleged package to add more legitimacy to the scam.
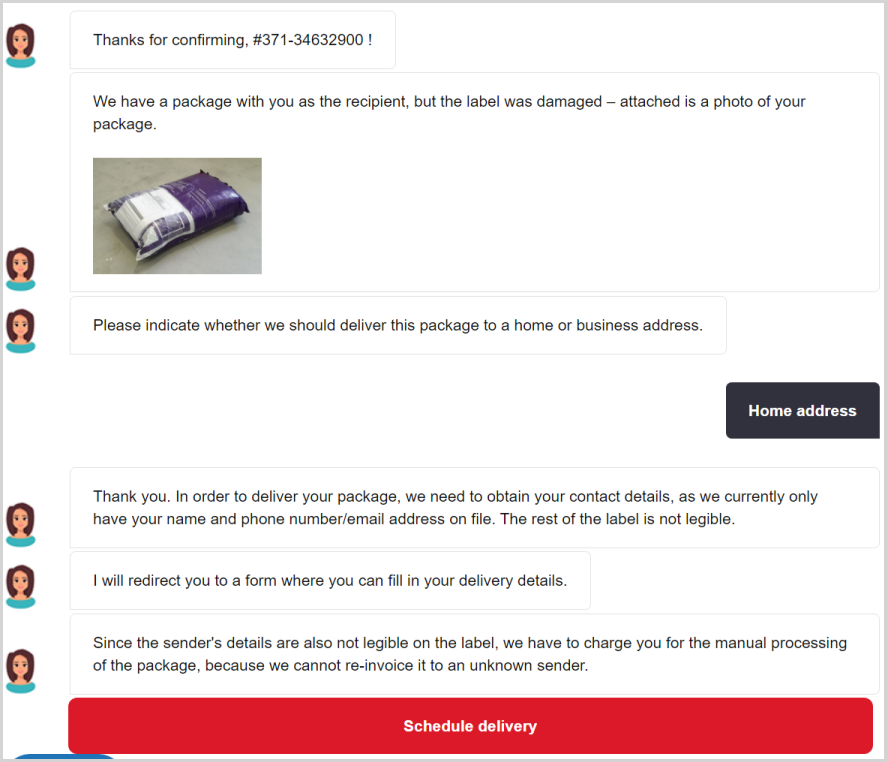
This virtual assistant offers pre-defined responses for the visitor, so the conversation is fixed, always leading to showing a photograph of the alleged package featuring a damaged label.
Due to this problem, the chatbot requests the victim to give their personal details such as home or business address, full name, phone number, etc.
After that, the delivery is supposedly scheduled, and a bogus CAPTCHA step is displayed to act as one more false send of legitimacy to the phishing page.
Next, the victim is redirected to a phishing page that requires entering DHL account credentials and finally, leading to a payment step, supposedly to cover the shipping costs.
The final "Secure Pay" page contains the typical credit card payment fields, including cardholder name, card number, expiration date, and the CVV code.
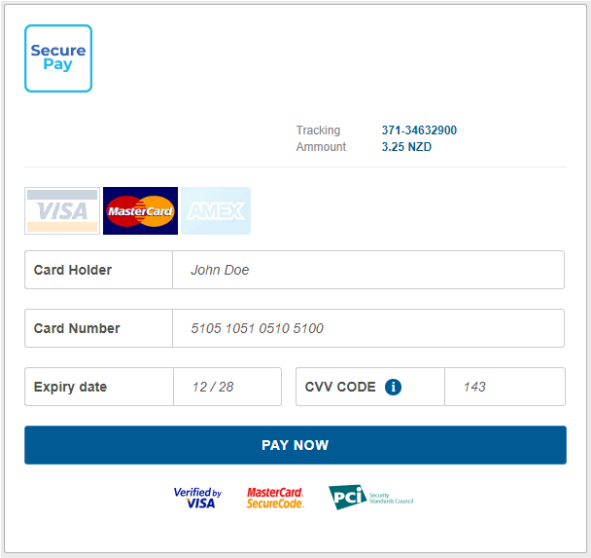
When the details are entered and the "Pay Now" button is clicked, the victim receives a one-time password (OTP) on the provided mobile phone number via SMS, which adds to the sense of legitimacy.
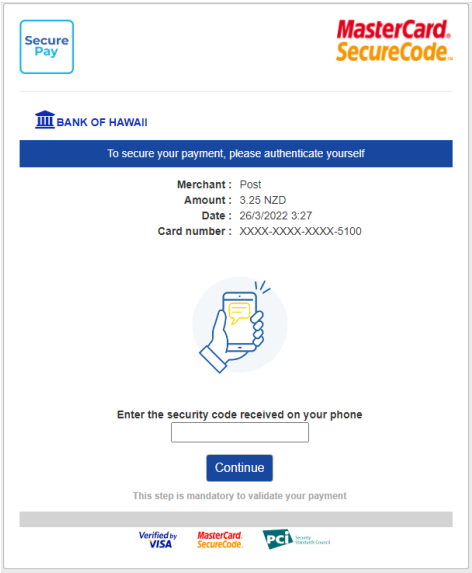
Trustwave's analysts tested entering random characters, and the system returned an error about an invalid security code, so the implementation of the OTP verification is real.
If the correct code is entered, the fake page serves a "Thank you!" message and confirms that the submission has been received.
Campaigns are getting more "genuine"
Threat actors are increasingly using mechanisms generally found in real websites, like CAPTCHAs, OTPs, and now even chatbots, making it hard for victims to spot attempts to steal their information.
This calls for greater vigilance when receiving unsolicited communications that request your immediate action, especially if these messages contain embedded buttons and URL links.
If DHL or any other shipping service requires your action, you should always open the actual website on a new browser tab instead of clicking on the provided links.
Then Log in to your account on the trusted platform, and check for any pending items or alerts. Alternatively, contact a customer support agent yourself.
As always, the best way to spot a phishing page is to examine the URL for the website. If it looks suspicious or does not match the legitimate domain, do not enter any personal information into the page.
In this case, the spoofed DHL URL ends with the domain "24mhd.com," which is clearly not the DHL website and is a clear sign of a phishing attempt.
Phishing websites now use chatbots to steal your credentials



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.