Modern phishing kits sold on cybercrime forums as off-the-shelve packages feature multiple, sophisticated detection avoidance and traffic filtering systems to ensure that internet security solutions won’t mark them as a threat.
Fake websites that mimic well-known brands are abundant on the internet to lure victims and steal their payment details or account credentials.
Most of these websites are built using phishing kits that feature brand logos, realistic login pages, and in cases of advanced offerings, dynamic webpages assembled from a set of basic elements.
Advanced phishing kit dictionary (Kaspersky)
Threat actors use phishing kits extensively due to the automation they offer, as they typically have to set up hundreds of fake sites each day to replace those detected and blocked the previous day.
However, that doesn’t mean that authors of these kits don’t make an effort to incorporate anti-detection systems that would help them stay up and running for longer.
On the contrary, they are employing multiple mechanisms to help keep their malicious nature hidden from sophisticated threat detectors, and Kaspersky has published a report today detailing the main methods.
How phishing kits stay hidden
First, phishing kits include visitor filtering settings that prevent bots, analysis software, and guests from non-targeted locations from entering.
Search engine crawlers also have to be blocked from accessing the site as putting it too high on search results increases the risk of exposure and leads to a prompt take-down.
Then there are the obfuscation options that aim to prevent detection from internet security tools.
- Caesar cipher – Replacing every character in the text by one that is a fixed number of positions further down the alphabet so that the content doesn’t make sense. When the page is loaded, the shift reverts, and the correct characters are displayed.
- Page source encoding – AES or base64 encoding on the text or the page’s HTML code, which is much more powerful than the Caesar method. The content is decoded on the browser when the page is loaded.
- Invisible HTML tags – Add many junk HTML tags that are invisible when the page is rendered on the browser and only serve as innocuous “noise” that hides the malicious parts.
- String slicing – Cutting strings into re-arrangeable groups of characters and referring to them by their number in a code table. When the page is loaded, the strings are reassembled back into completion.
- Randomized HTML attributes – Adding a large number of randomized tag attribute values to effectively disable anti-phishing tools by rendering their guesses unreliable, which leads them to dismissal.
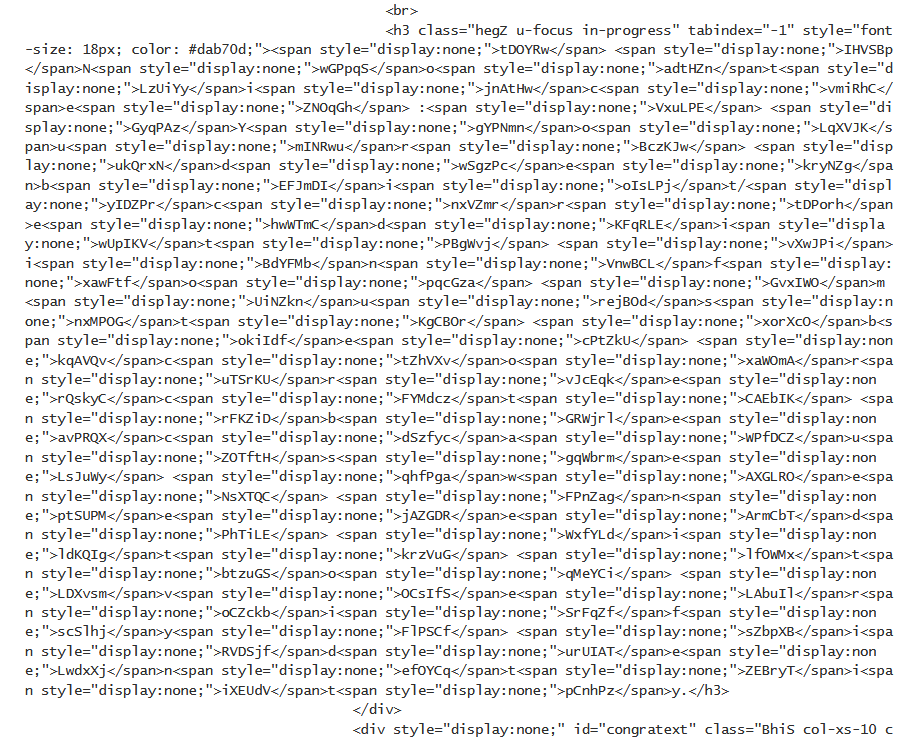
Junk HTML tags in phishing site (Kaspersky)
Some of the above tricks are also employed for obfuscating the stolen data from victims or the code of the phishing kit to prevent unpaid copies and forks.
A shifting market
Kaspersky reports that in 2021, it detected 469 individual phishing kits supporting at least 1.2 million phishing websites.
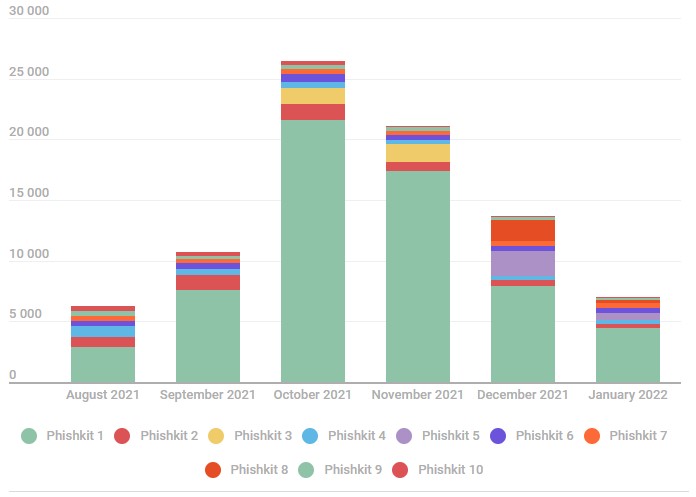
Number of unique domains using the top 10 phishing kits (Kaspersky)
As the security firm underlines, the number of sophisticated phishing kits that include anti-bot, anti-detection, and geoblocking features constantly increases.
The URLs to these sites are circulated via emails, instant messages, forum posts, and even YouTube videos, so beware.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.