A sophisticated phishing kit has been targeting North Americans since mid-September, using lures focused on holidays like Labor Day and Halloween.
The kit uses multiple evasion detection techniques and incorporates several mechanisms to keep non-victims away from its phishing pages.
According to Akamai, whose security researchers discovered the campaign, one of the most interesting features of the kit is a token-based system that ensures each victim is redirected to a unique phishing page URL.
Campaign overview
The campaign spotted by Akamai started in September 2022 and continued throughout October, preying on online shoppers looking for "holiday specials."
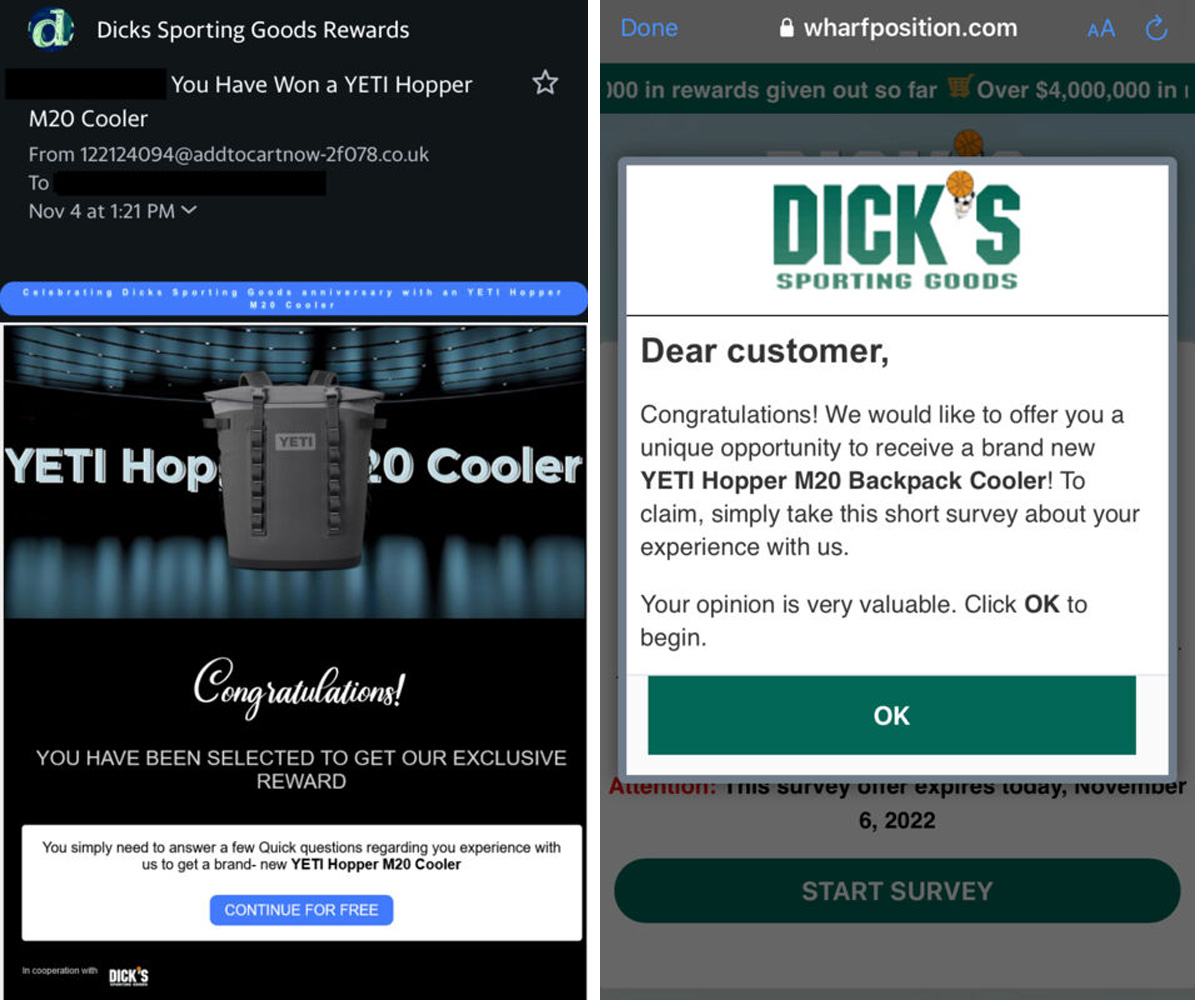
The central theme of the phishing emails sent to prospective victims is a chance to win a prize from a reputable brand.
The links in the email don't raise any alarms as they lead to the phishing site after a series of redirections, while URL shorteners conceal most URLs.
Additionally, the attackers abuse legitimate cloud services like Google, AWS, and Azure, abusing their good reputation to bypass protection mechanisms.
Everyone visiting the phishing site wins the promised prize after completing a short survey. In addition, a five-minute timer ensures those taking the survey are infused with a feeling of urgency.
Some impersonated brands include sporting goods firm Dick's, high-end luggage maker Tumi, Delta Airlines, and the wholesale clubs, Sam's Club and Costco.
To increase the campaign's effectiveness, the phishing actors include fake user testimonials showcasing the received prizes.
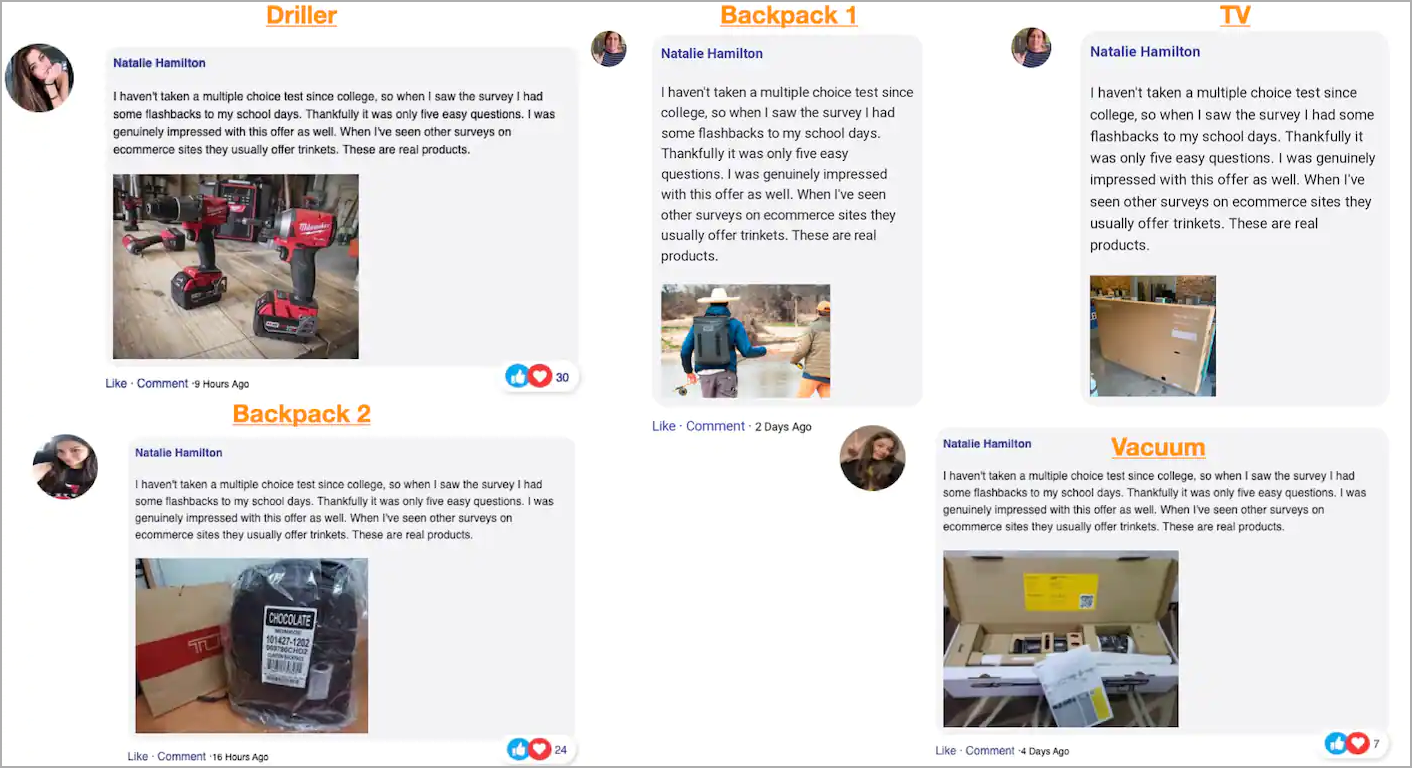
Fake user testimonials on the survey pages - Source: Akamai
After "winning" the prize, the victim is requested to cover the shipping costs for receiving the prize, for which they need to enter their payment card details.
Of course, there is no prize to be shipped, and the credit card details are stolen by the threat actors to be used for online purchases.
Akamai says roughly 89% of users landing on phishing domains are from the United States and Canada.
Depending on their exact location, the redirection takes them to a different phishing site impersonating locally available brands.
Each victim gets a unique URL
Each phishing email contains a link to a landing page with an anchor (#) usually used to direct a visitor to a specific part of the linked-to page.
In this phishing campaign, the anchor tag represents a token used by JavaScript on the phishing landing to reconstruct a URL to which the target will be redirected.
"The values being after the HTML anchor will not be considered as HTTP parameters and will not be sent to the server, yet this value will be accessible by JavaScript code running on the victim's browser," explains Akamai.
"In the context of a phishing scam, the value placed after the HTML anchor might be ignored or overlooked when scanned by security products that are verifying whether it is malicious or not."
"This value will also be missed if viewed by a traffic inspection tool."
Akamai shared the following image showing how the phishing link anchor is used to create a redirection link.
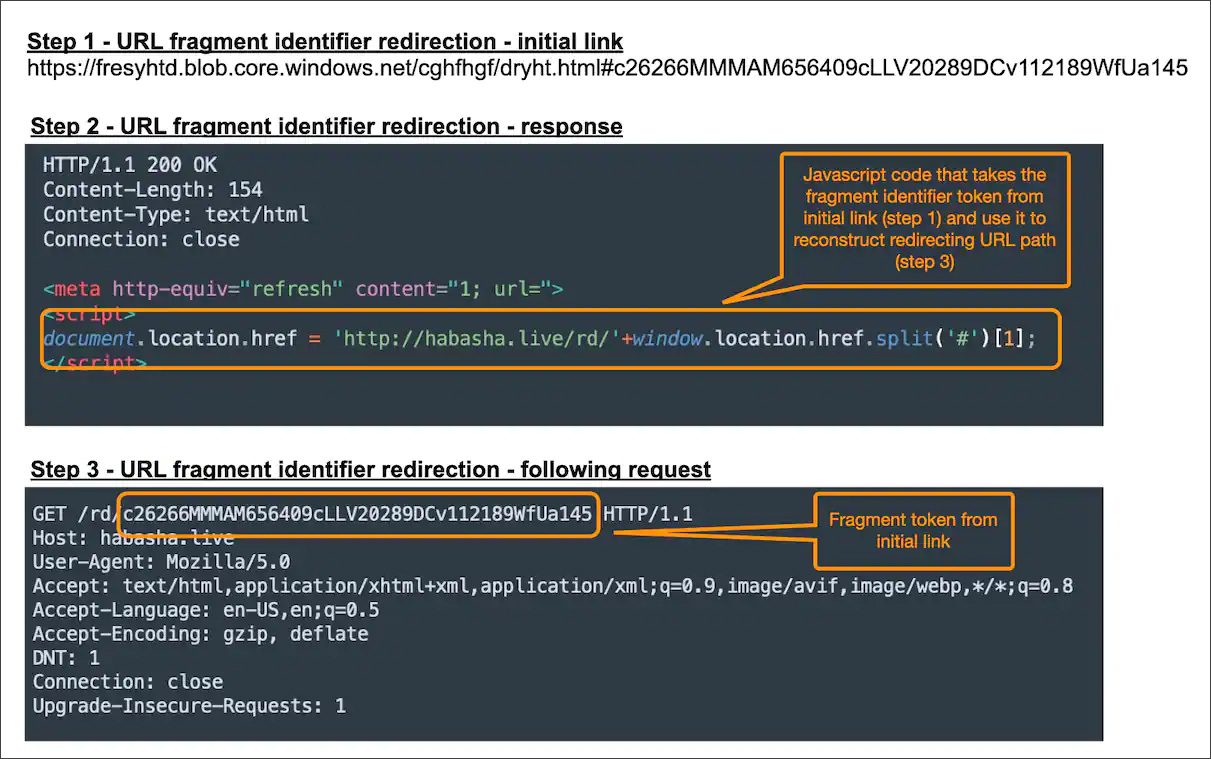
Redirecting based on anchor token - Source: Akamai
Security products and network traffic inspection tools overlook this token, so it doesn't introduce risks for the phishing actors.
Instead, it helps keep unwanted traffic, researchers, analysts, and random visitors away from the phishing landing pages.
Those without a valid token, and browser redirections that don't use JavaScript for their rendering, will fail to access the phishing site.
Apart from filtering non-victims, the tokens can also be used for victim-specific tracking, campaign performance measurement, and more.
In summary, the kit combines almost all known techniques for effectiveness and detection avoidance, making it a potent threat to North Americans.
With the Black Friday and Christmas shopping season approaching, consumers should be extra vigilant when they receive messages about promotions and special offers.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.