A new phishing campaign uses Facebook posts as part of its attack chain to trick users into giving away their account credentials and personally identifiable information (PII).
The emails sent to targets pretend to be a copyright infringement issue on one of the recipient's Facebook posts, warning that their account will be deleted within 48 hours if no appeal is filed.
.png)
Phishing email sent to targets (Trustwave)
The link to appeal the account deletion is an actual Facebook post on facebook.com, helping threat actors bypass email security solutions and ensure their phishing messages land in the target's inbox.
The Facebook post pretends to be "Page Support," using a Facebook logo to appear as if the company manages it.
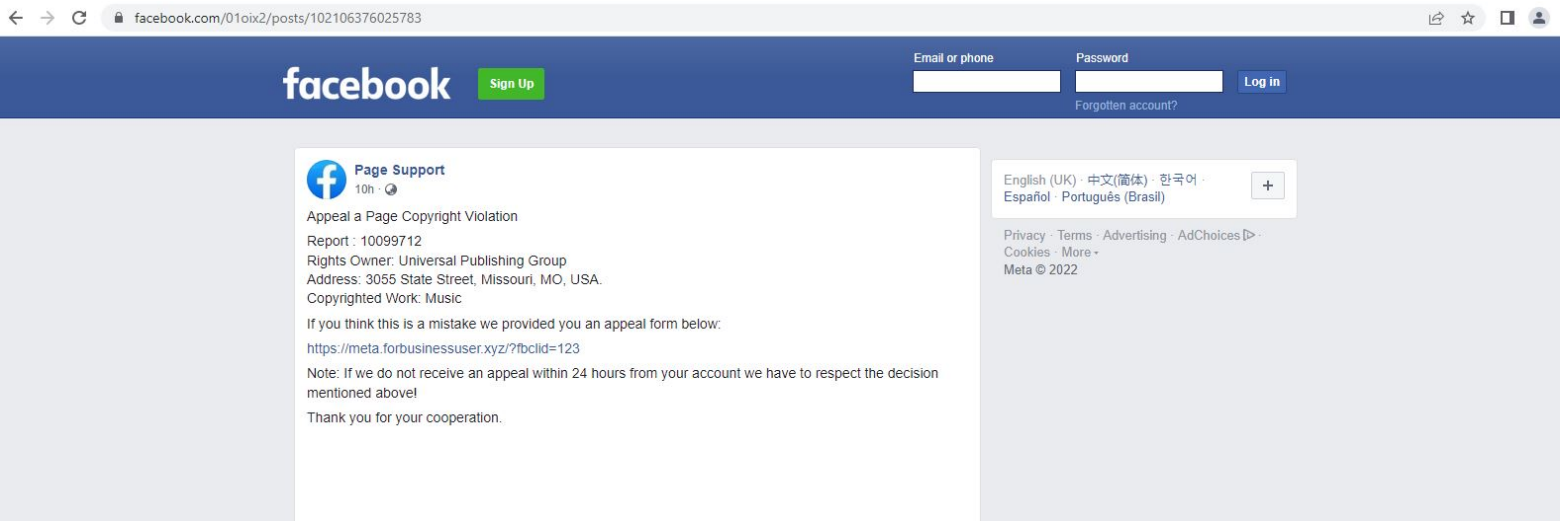
Facebook post masqueraded as a support page (Trustwave)
However, this post includes a link to an external phishing site named after Meta, Facebook’s owner company, to slightly reduce the chances of victims realizing the scam.
Trustwave's analysts who discovered the phishing campaign found the following three URLs, which remain online when writing this.
- meta[.]forbusinessuser[.]xyz/?fbclid=123
- meta[.]forbusinessuser[.]xyz/main[.]php
- meta[.]forbusinessuser[.]xyz/checkpoint[.]php
The phishing sites are crafted with care to make them appear like Facebook's actual copyright appeal page, containing a form where victims are requested to enter their full name, email address, phone number, and Facebook username.
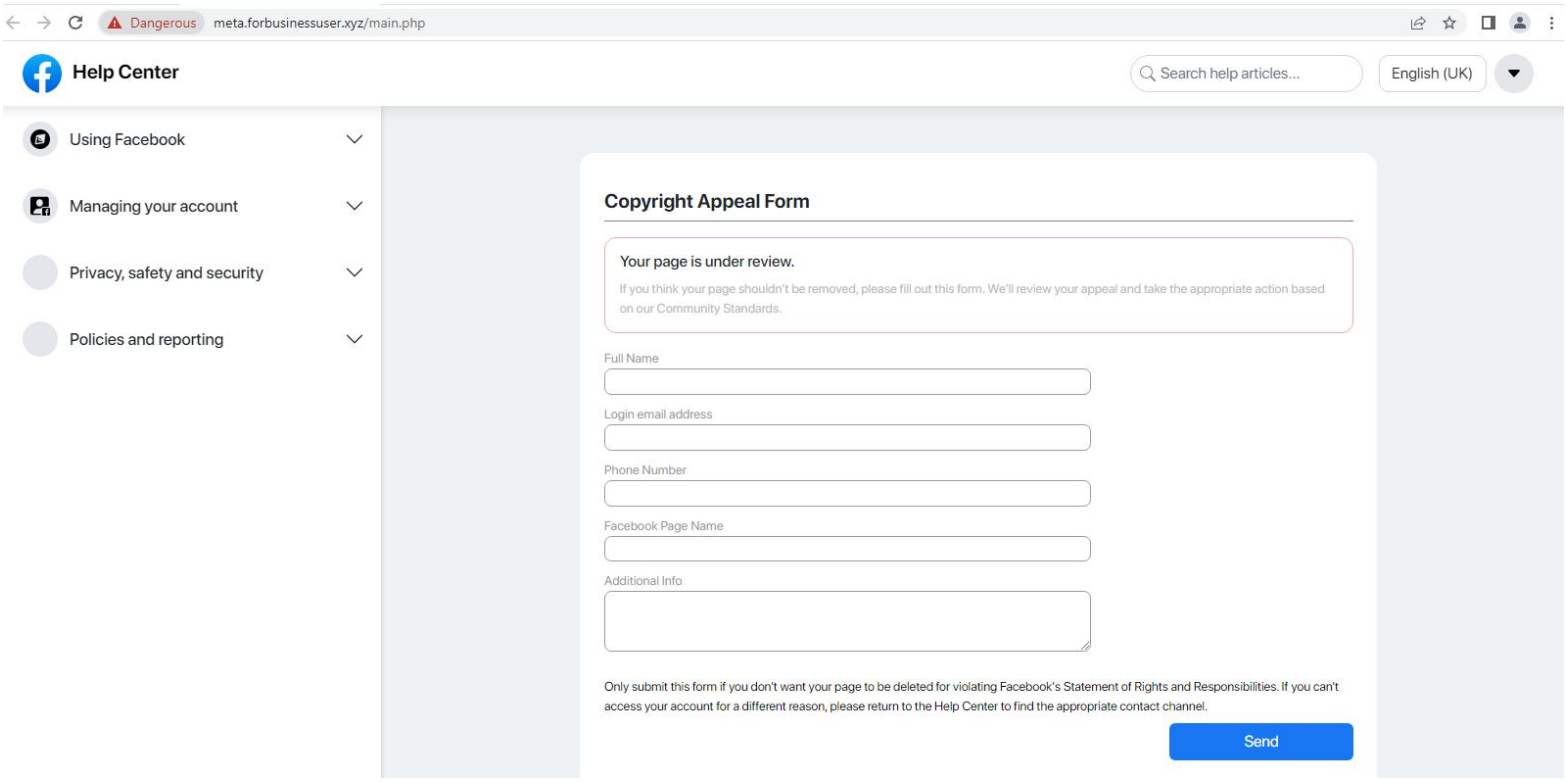
The landing phishing page mimics Facebook's Help Center (Trustwave)
Upon submission of this data, the page also collects the victim’s IP address and geolocation information and exfiltrates everything to a Telegram account under the threat actor’s control.
The threat actors might collect the extra information to bypass fingerprinting protections or security questions while taking over the victim's Facebook account.
Meanwhile, a redirection takes the victim to the next phishing page, which displays a fake 6-digit one-time password (OTP) request with a timer.
.png)
Bogus 2FA step on the phishing site (Trustwave)
Whatever code the victim enters will result in an error, and if the 'Need another way to authenticate?' is clicked, the site redirects to the actual Facebook site.
Trustwave’s analysts also discovered that the threat actors use Google Analytics on their phishing pages to help them track the efficiency of their campaigns.
Widespread technique
Trustwave reports it has found numerous Facebook accounts using phony posts made to appear as support pages that lead victims to phishing websites.
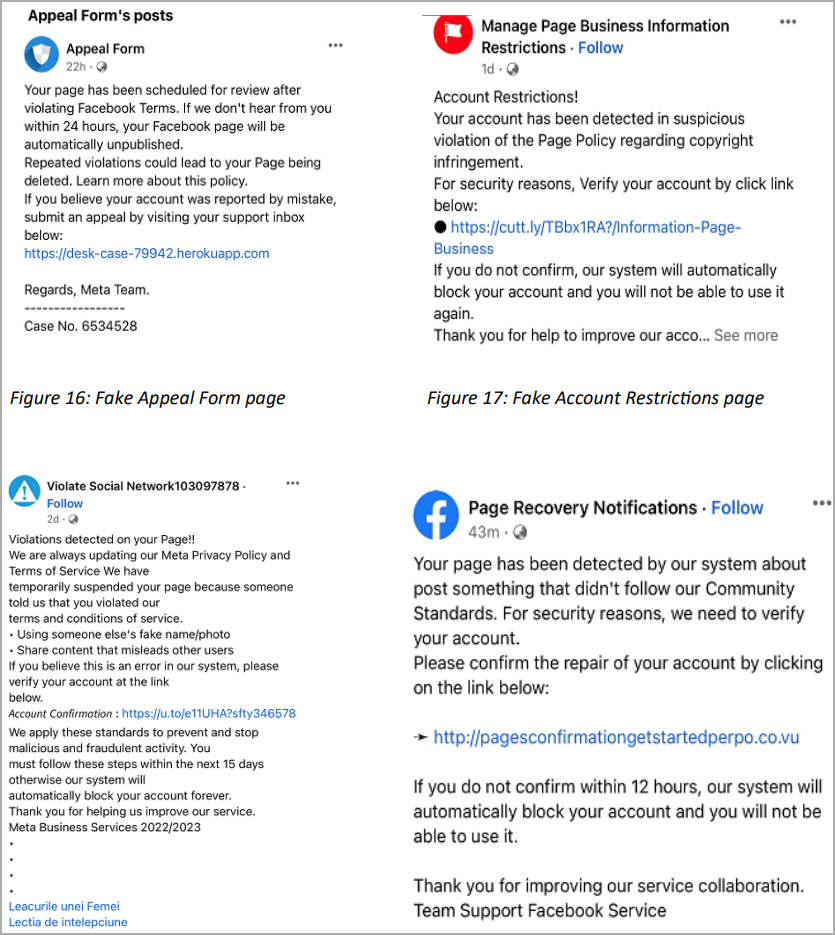
Various Facebook accounts promoting the same fake alerts (Trustwave)
These posts use URL shorteners for linking to phishing sites to evade getting flagged and removed by the social media platform.
Victims may land on these posts via phishing emails, like in the campaign presented in this report, or via instant messages received on Facebook.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.