More than 60,000 Microsoft Exchange servers exposed online are yet to be patched against the CVE-2022-41082 remote code execution (RCE) vulnerability, one of the two security flaws targeted by ProxyNotShell exploits.
According to a recent tweet from security researchers at the Shadowserver Foundation, a nonprofit organization dedicated to improving internet security, almost 70,000 Microsoft Exchange servers were found to be vulnerable to ProxyNotShell
attacks according to version information (the servers' x_owa_version header).
However, new data published on Monday shows that the number of vulnerable Exchange servers has decreased from 83,946 instances in mid-December to 60,865 detected on January 2nd.
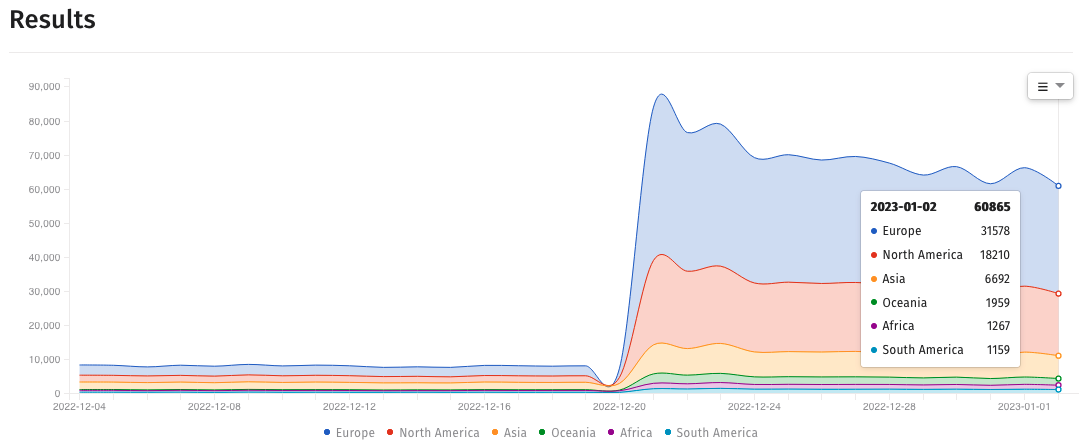
Exchange servers vulnerable to ProxyNotShell attacks (Shadowserver Foundation)
These two security bugs, tracked as CVE-2022-41082 and CVE-2022-41040 and collectively known as ProxyNotShell, affect Exchange Server 2013, 2016, and 2019.
If successfully exploited, attackers can escalate privileges and gain arbitrary or remote code execution on compromised servers.
Microsoft released security updates to address the flaws during the November 2022 Patch Tuesday, even though ProxyNotShell attacks have been detected in the wild since at least September 2022.
Threat intelligence company GreyNoise has been tracking ongoing ProxyNotShell exploitation since September 30th and provides information on ProxyNotShell scanning activity and a list of IP addresses linked to the attacks.
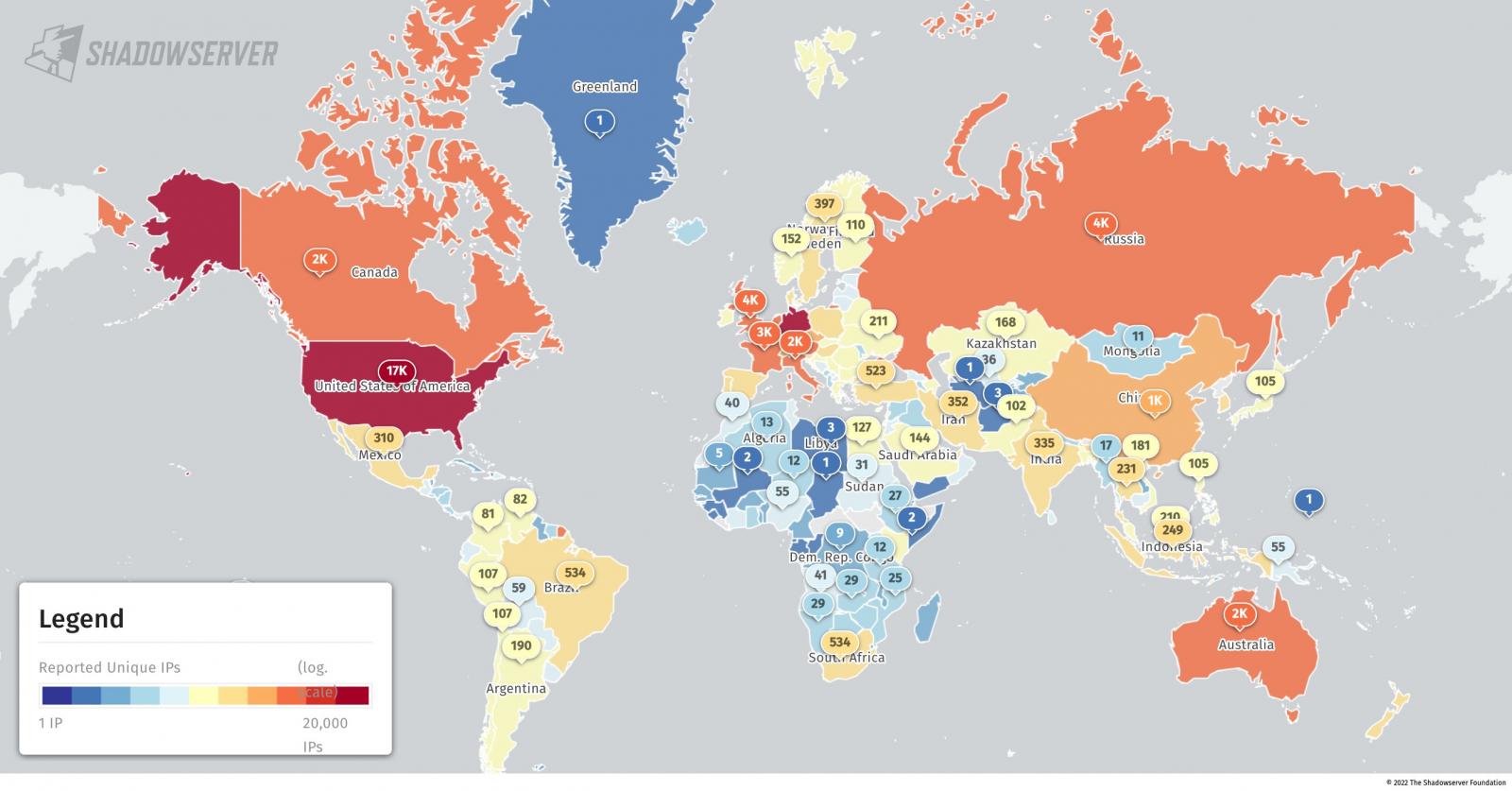
Thousands also exposed to ProxyShell and ProxyLogon attacks
In order to protect your Exchange servers from incoming attacks, you have to apply the ProxyNotShell patches released by Microsoft in November.
While the company also provided mitigation measures, these can be bypassed by attackers, meaning that only fully patched servers are secure from compromise.
As reported by BleepingComputer last month, Play ransomware threat actors are now using a new exploit chain to bypass ProxyNotShell URL rewrite mitigations and gain remote code execution on vulnerable servers through Outlook Web Access (OWA).
To make things even worse, a Shodan search reveals a significant number of Exchange servers exposed online, with thousands left unpatched against ProxyShell and ProxyLogon vulnerabilities that made it into the top most exploited vulnerabilities in 2021.
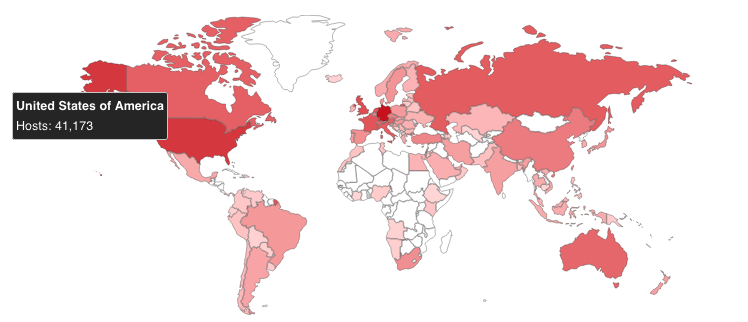
Exchange servers exposed online (Shodan)
Exchange servers are valuable targets, as demonstrated by the financially motivated FIN7 cybercrime group which has developed a custom auto-attack platform known as Checkmarks and designed to breach Exchange servers.
According to threat intelligence firm Prodaft, which discovered the platform, it scans for and exploits various Microsoft Exchange remote code execution and privilege elevation vulnerabilities, such as CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207.
FIN7's new platform has already been used to infiltrate 8,147 companies, primarily located in the United States (16.7%), after scanning over 1.8 million targets.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.