WordPress sites are being hacked to install malicious plugins that display fake software updates and errors to push information-stealing malware.
Over the past couple of years, information-stealing malware has become a scourge to security defenders worldwide as stolen credentials are used to breach networks and steal data.
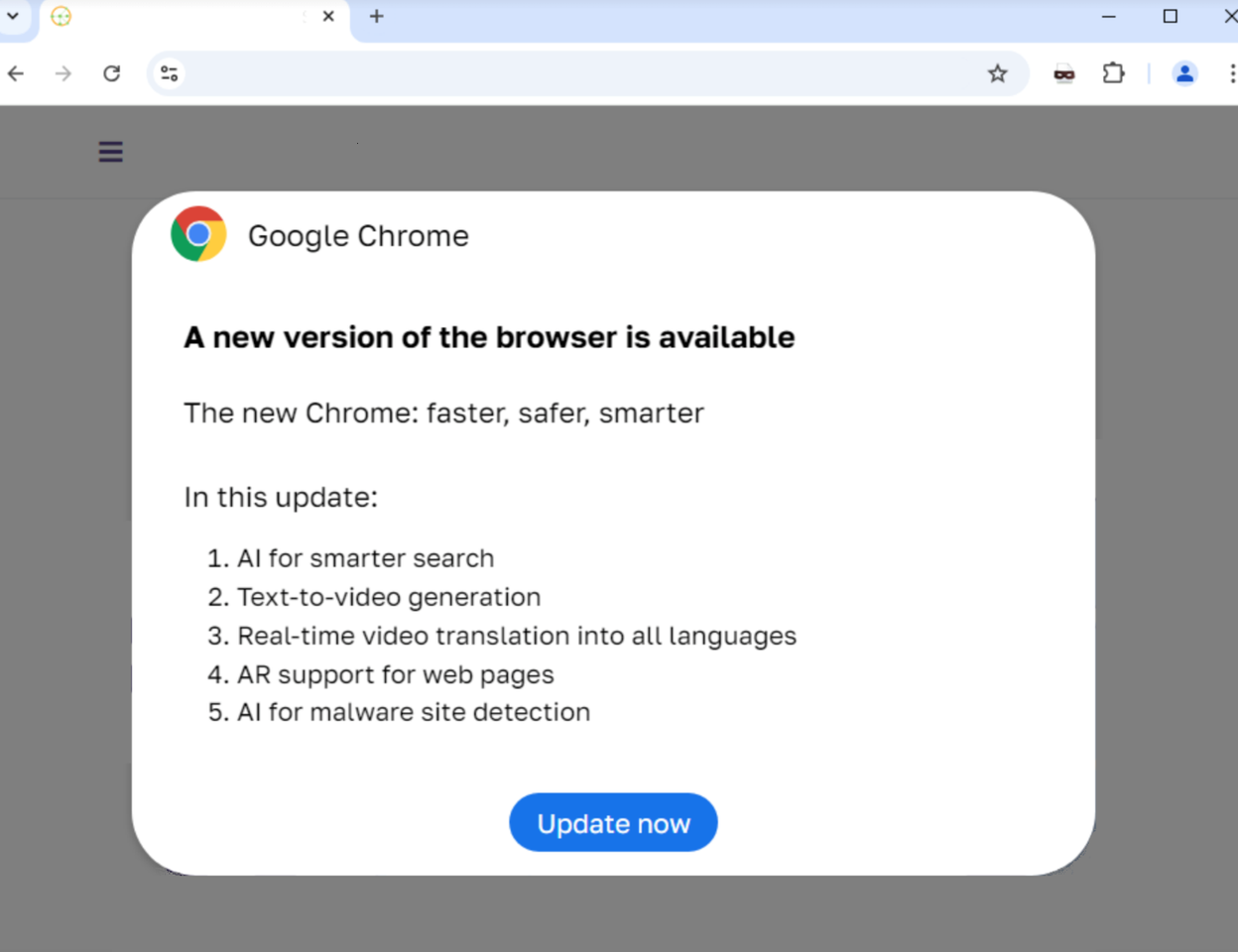
Since 2023, a malicious campaign called ClearFake has been used to display fake web browser update banners on compromised websites that distribute information-stealing malware.
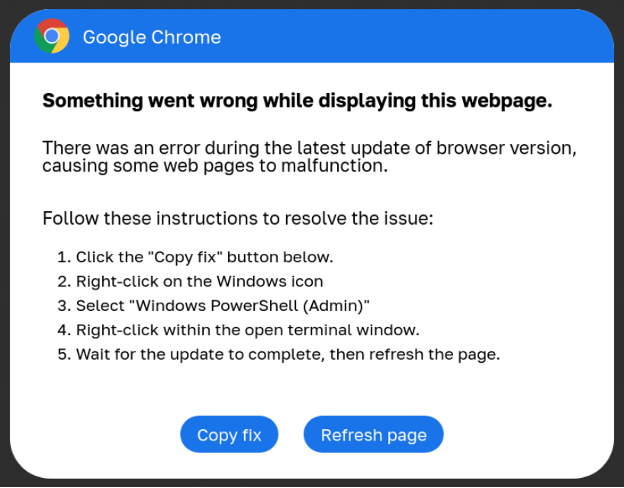
In 2024, a new campaign called ClickFix was introduced that shares many similarities with ClearFake but instead pretends to be software error messages with included fixes. However, these "fixes" are PowerShell scripts that, when executed, will download and install information-stealing malware.
ClickFix campaigns have become increasingly common this year, with threat actors compromising sites to display banners showing fake errors for Google Chrome, Google Meet conferences, Facebook, and even captcha pages.
Malicious WordPress plugins
Last week, GoDaddy reported that the ClearFake/ClickFix threat actors have breached over 6,000 WordPress sites to install malicious plugins that display the fake alerts associated with these campaigns.
"The GoDaddy Security team is tracking a new variant of ClickFix (also known as ClearFake) fake browser update malware that is distributed via bogus WordPress plugins," explains GoDaddy security researcher Denis Sinegubko.
"These seemingly legitimate plugins are designed to appear harmless to website administrators but contain embedded malicious scripts that deliver fake browser update prompts to end-users."
The malicious plugins utilize names similar to legitimate plugins, such as Wordfense Security and LiteSpeed Cache, while others use generic, made-up names.
The list of malicious plugins seen in this campaign between June and September 2024 are:
| LiteSpeed Cache Classic | Custom CSS Injector |
| MonsterInsights Classic | Custom Footer Generator |
| Wordfence Security Classic | Custom Login Styler |
| Search Rank Enhancer | Dynamic Sidebar Manager |
| SEO Booster Pro | Easy Themes Manager |
| Google SEO Enhancer | Form Builder Pro |
| Rank Booster Pro | Quick Cache Cleaner |
| Admin Bar Customizer | Responsive Menu Builder |
| Advanced User Manager | SEO Optimizer Pro |
| Advanced Widget Manage | Simple Post Enhancer |
| Content Blocker | Social Media Integrator |
Website security firm Sucuri also noted that a fake plugin named "Universal Popup Plugin" is also part of this campaign.
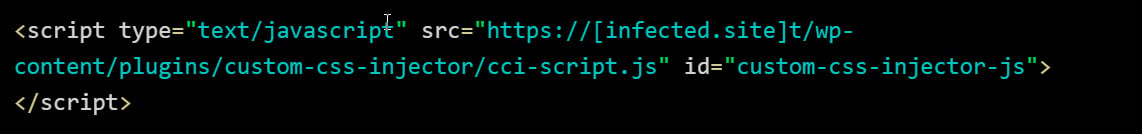
When installed, the malicious plugin will hook various WordPress actions depending on the variant to inject a malicious JavaScript script into the HTML of the site.
When loaded, this script will attempt to load a further malicious JavaScript file stored in a Binance Smart Chain (BSC) smart contract, which then loads the ClearFake or ClickFix script to display the fake banners.
Source: Randy McEoin
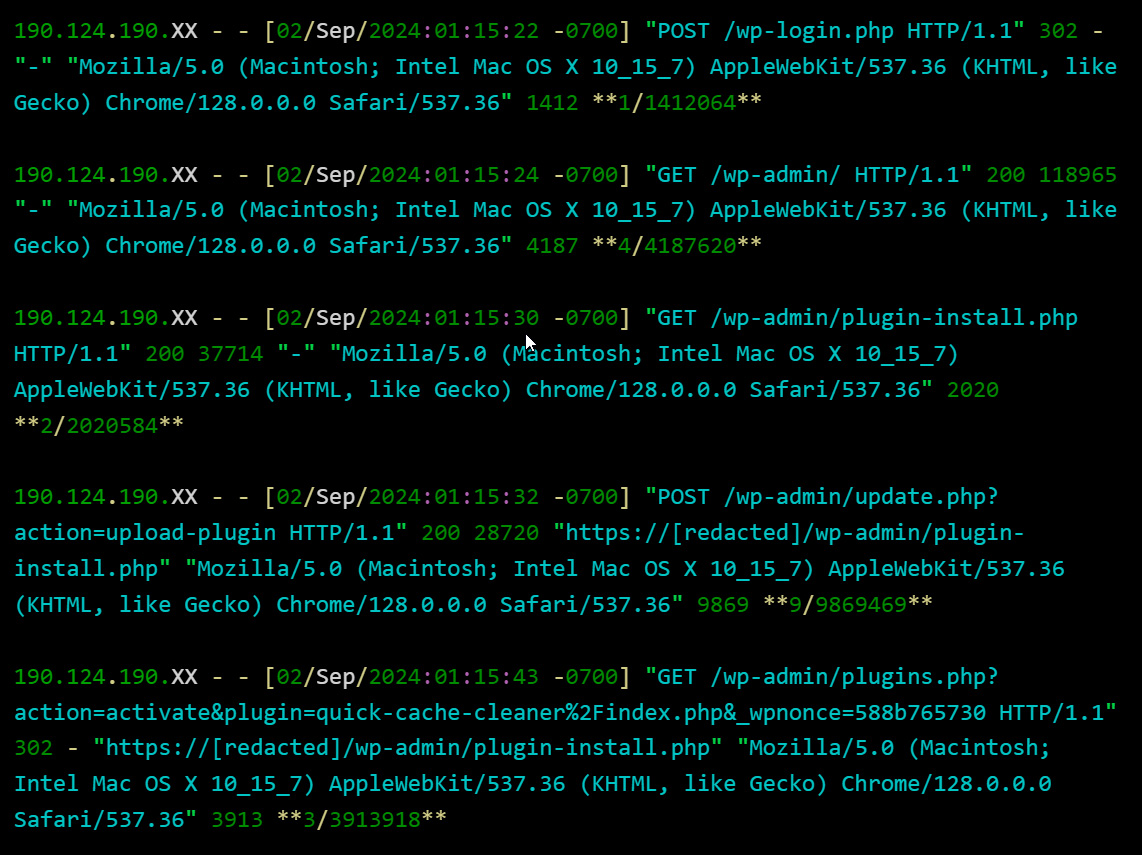
From web server access logs analyzed by Sinegubko, the threat actors appear to be utilizing stolen admin credentials to log into the WordPress site and install the plugin in an automated manner.
As you can see from the image below, the threat actors log in via a single POST HTTP request rather than first visiting the site's login page. This indicates that it is being done in an automated manner after the credentials have been already obtained.
Once the threat actor logs in, they upload and install the malicious plugin.
While it is unclear how the threat actors are obtaining the credentials, the researcher notes it could be through previous brute force attacks, phishing, and information-stealing malware.
If you are a WordPress operation and are receiving reports of fake alerts being displayed to visitors, you should immediately examine the list of installed plugins, and remove any that you did not install yourself.
If you find unknown plugins, you should also immediately reset the passwords for any admin users to a unique password only used at your site.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
2023: Over 5,800 news posts | 2024 (till end of September): 4,292 news posts
RIP Matrix | Farewell my friend ![]()



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.