Researchers discovered 120,000 infected systems that contained credentials for cybercrime forums. Many of the computers belong to hackers, the researchers say.
Analyzing the data, threat researchers found that the passwords used for logging into hacking forums were generally stronger than those for government websites.
Hacker logins compromised
After pouring through 100 cybercrime forums, researchers at threat intelligence company Hudson Rock found that some hackers had inadvertently infected their computers and had their logins stolen.
Hudson Rock says that 100,000 of the compromised computers belonged to hackers and the number of credentials for cybercrime forums was in excess of 140,000.
The researchers collected the information from publicly available leaks as well as info-stealer logs sourced directly from threat actors.
Info-stealers are a type of malware that search specific locations on the computer for login information. A common target is web browsers, because of their autofill and password storage features.
Alon Gal, chief technology officer at Hudson Rock, told BleepingComputer that “hackers around the world infect computers opportunistically by promoting results for fake software or through YouTube tutorials directing victims to download infected software.”
Among those that fell for the lure were other hackers, likely less skilled ones, so they got infected just like any other gullible user trying to take a shortcut.
Identifying the owners of those compromised computers as hackers, or at least hacker enthusiasts, was possible by looking at the data from the info-stealer logs, which also exposed the individual’s real identity:
- Additional credentials found on the computers (additional emails, usernames)
- Auto-fill data containing personal information (names, addresses, phone numbers)
- System information (computer names, IP addresses)
In a previous blog post, Hudson Rock describes how a prominent threat actor called La_Citrix, known for selling Citrix/VPN/RDP access to companies, accidentally infected their computer.
Looking at the collected data, Hudson Rock determined that more than 57,000 compromised users had accounts to the Nulled[.]to community of budding cybercriminals.
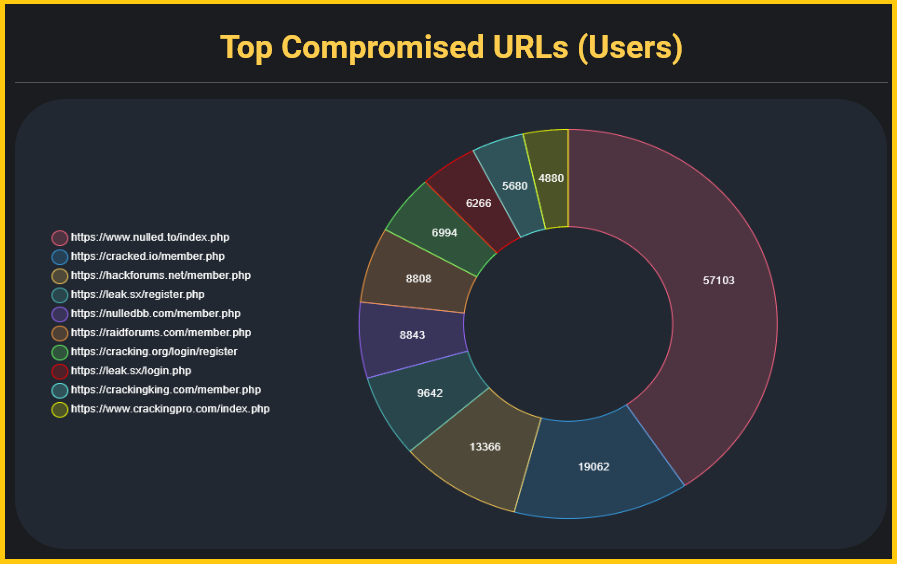
Users of BreachForums had the strongest passwords to log into the site, the researchers found, with more than 40% of the credentials being at least 10 characters long and containing four types of characters.
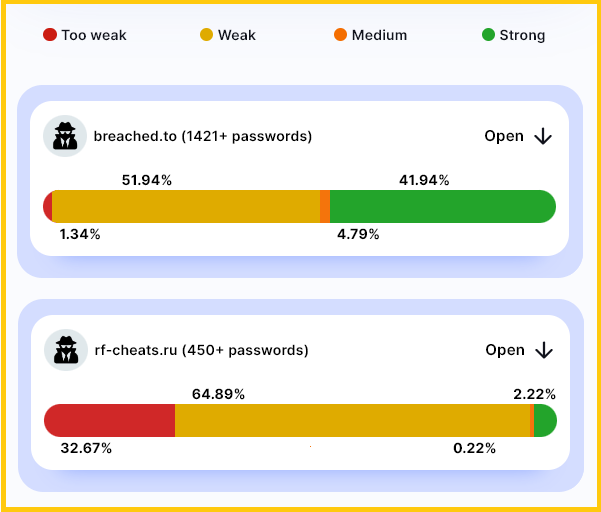
However, hackers also used very weak passwords like a string of consecutive numbers. This could be explained by their lack of interest in getting involved in the community.
They could be using the account just to keep up with the discussions, check what data was for sale, or just to have access to the forum whenever something more important occurred.
The researchers also discovered that the credentials for cybercrime forums were generally stronger than the logins for government websites, although the difference is not large.
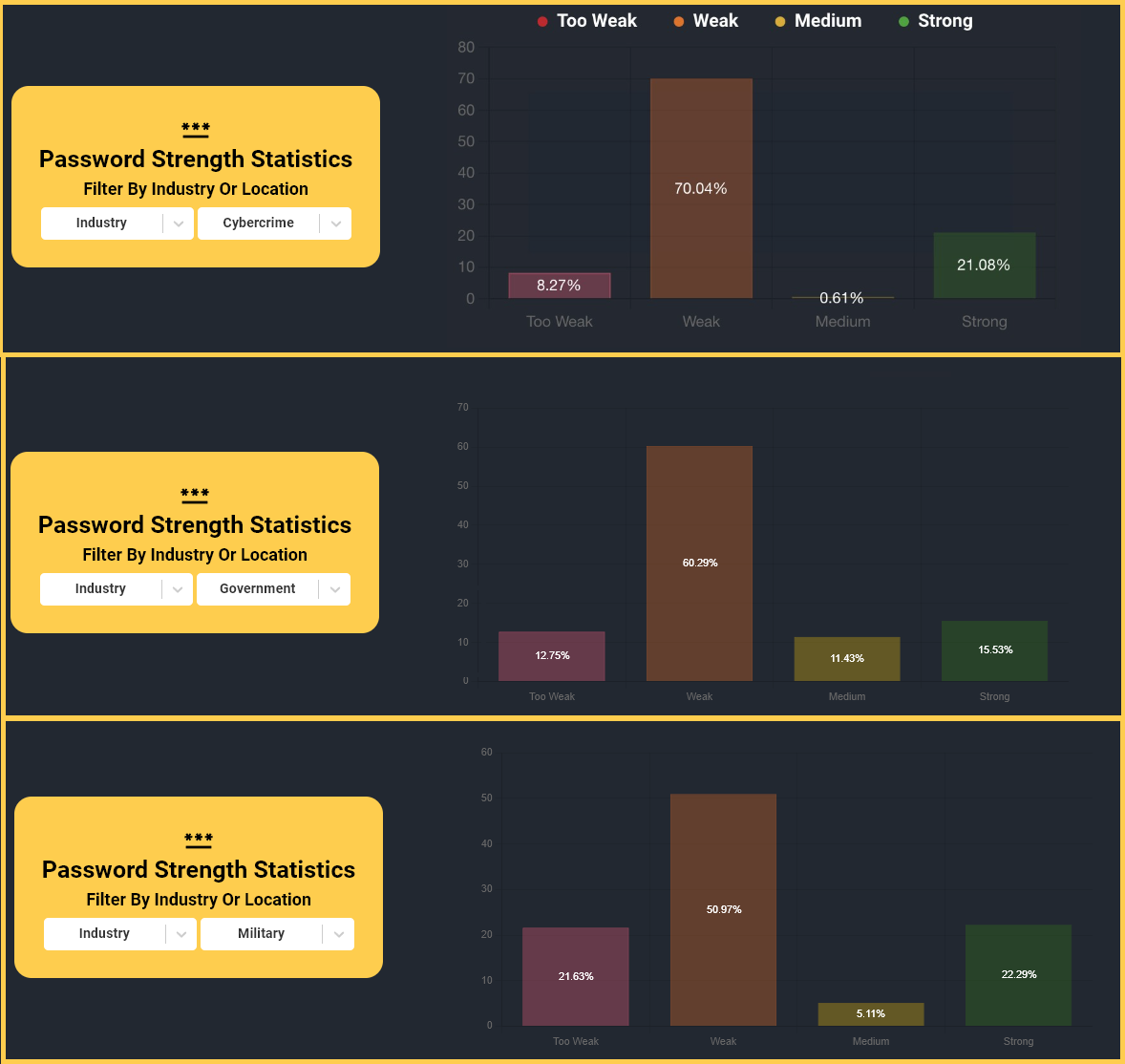
According to Hudson Rock, most of the infections were from just three info-stealers, which also happen to be popular choices with many hackers: RedLine, Raccoon, and Azorult.
At the moment, a large number of initial access compromises start with an info-stealer, which collects all the data a threat actor needs to impersonate a legitimate user, typically called a system fingerprint.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.