Unknown threat actors have uploaded a massive 144,294 phishing-related packages on open-source package repositories, inluding NPM, PyPi, and NuGet.
The large-scale attack resulted from automation, as the packages were uploaded from accounts using a particular naming scheme, featured similar descriptions, and led to the same cluster of 90 domains that hosted over 65,000 phishing pages.
The campaign supported by this operation promotes fake apps, prize-winning surveys, gift cards, giveaways, and more. In some cases, they take victims to AliExpress via referral links.
A massive operation
This phishing campaign was discovered by analysts at Checkmarx and Illustria, who worked together to uncover and map the infection impacting the open-source software ecosystem.
NuGet had the largest share of malicious package uploads, counting 136,258, PyPI had 7,894 infections, and NPM only had 212.
The phishing packages were uploaded in troves within a couple of days, which is commonly a sign of malicious activity.
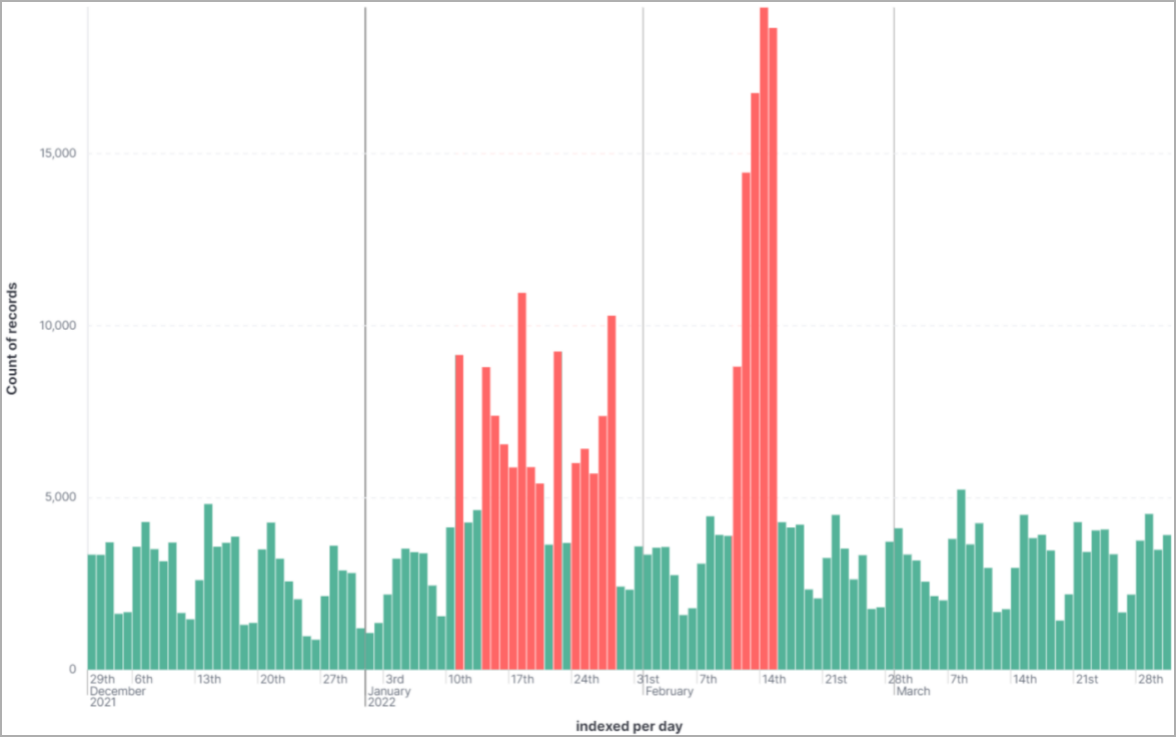
Diagram of malicious package uploads (Checkmarx)
The URL to the phishing sites was implanted in the package description, hoping that the links from repositories would increase the SEO of their phishing sites.
These package descriptions also urged users to click links to get more info about alleged gift card codes, apps, hack tools, etc.
.png)
Malicious package description (Checkmarx)
In some cases, the threat actors promote fake Steam gift card generators, Play Station Network e-gift card codes, Play Store credits, Instagram followers generators, YouTube subscribers generators, and more.
Almost all of these sites request visitors to enter their email, username, and account passwords, which is where the phishing step takes place.
.png)
Sample of the malicious websites (Checkmarx)
The fake sites feature an element that resembles the promised free generator but fails when visitors try to use it, asking for “human verification.”
This initiates a series of redirections to survey sites, finally landing on legitimate e-commerce websites using affiliate links, which is how the threat actors generate revenue from the campaign.
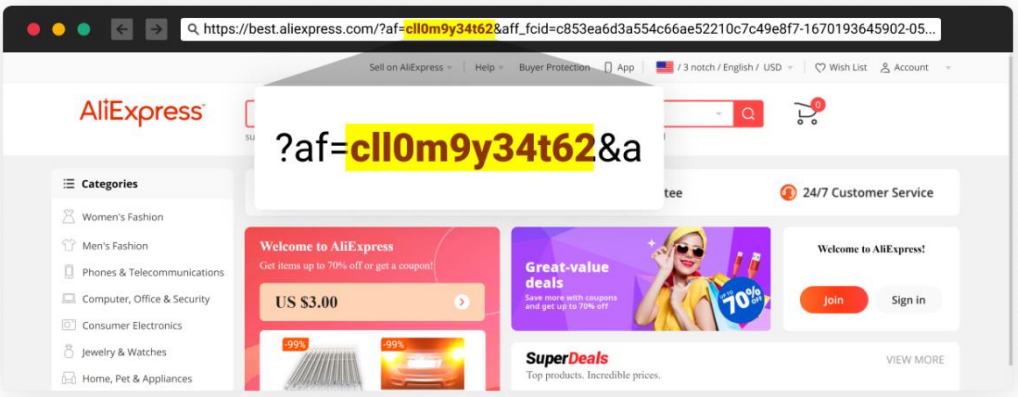
Refferal ID on final destination of the victim in the campaign (Checkmarx)
Of course, the stolen game account credentials, emails, and social media usernames can also be monetized, as these are typically bundled in collections and sold on hacking forums and darknet markets.
The security researchers who discovered this campaign informed NuGet of the infection, and all packages have since been delisted.
However, considering the automated method employed by the threat actors to upload such a large number of packages in such a short time, they could re-introduce the threat using new accounts and different package names at any time.
For the complete list of the URLs used in this campaign, check out this IoC text file on GitHub.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.