OldGremlin, one of the few ransomware groups attacking Russian corporate networks, has expanded its toolkit with file-encrypting malware for Linux machines.
The gang has Russian-speaking members that have been operating since at least March 2020 using self-made malware, focusing on Russian companies in the logistics, industry, insurance, retail, real estate, software development, and banking sectors.
Also known as TinyScouts, due to the names of the functions in the malicious code they use, OldGremlin is characterized by a small number of campaigns per year with million-dollar ransom demands.
In 2022, OldGremlin launched just five campaigns but they also demanded the highest ransom in the two and a half years of activity, $16.9 million, say researchers at Group-IB, a Singapore-based cybersecurity company.
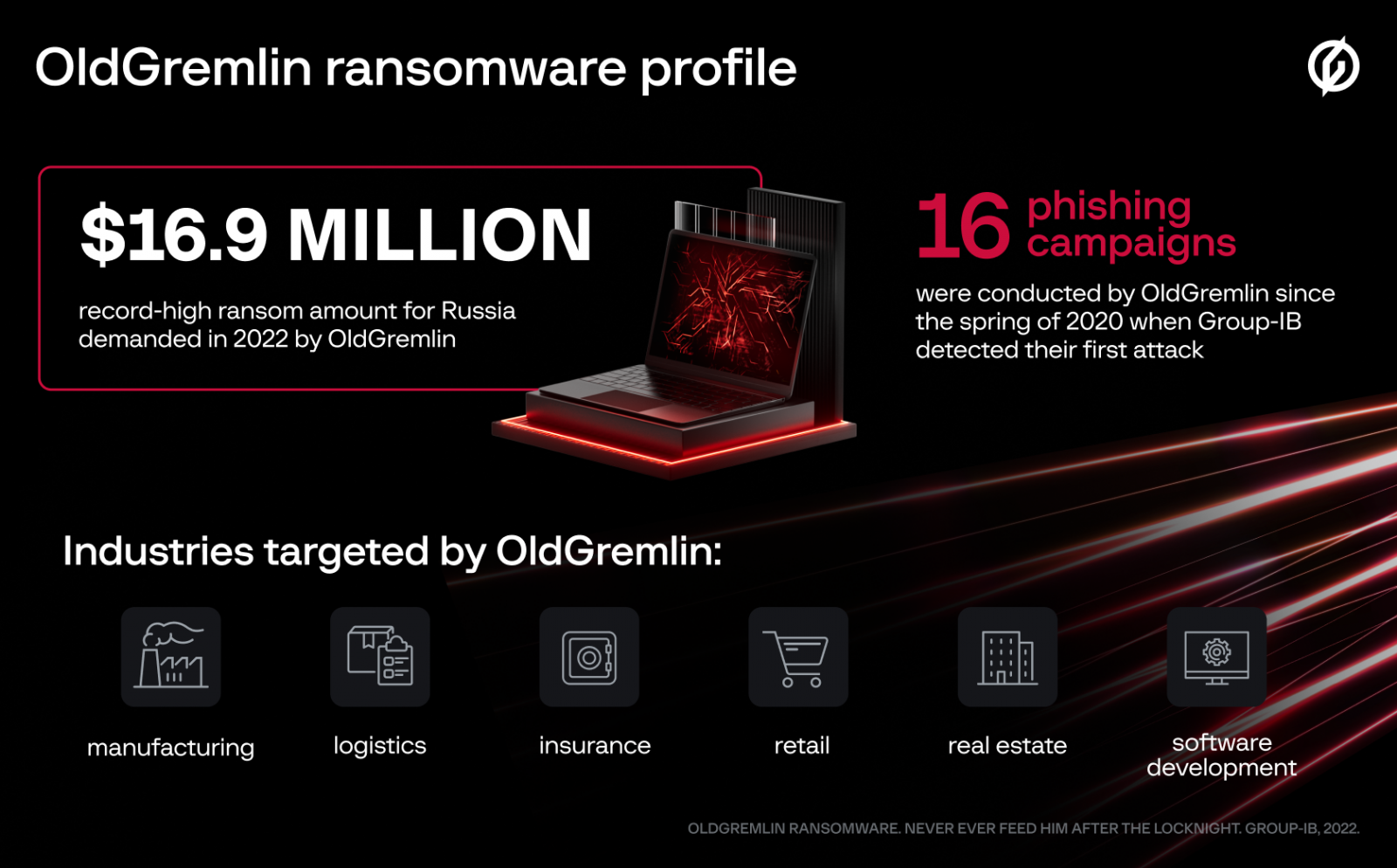
OldGremlin demanded $16.9 million after encrypting Russian company - source: Group-IB
OldGremlin’s ransomware for Linux
Group-IB researchers have been tracking OldGremlin and their tactics, techniques, and procedures (TTPS) since the first attacks attributed to the group in March 2020.
During an incident response engagement this year, Group-IB found that OldGremlin targeted a Linux machine with a Go variant of the TinyCrypt ransomware the gang uses to encrypt Windows machines.
The researchers say that the Linux variant works in the same way as the Windows counterpart, using the AES algorithm with the CBC block cipher mode to encrypt files with a 256-bit key, which is encrypted using the RSA-2048 asymmetric cryptosystem.
The malware executable is wrapped using Ultimate Packer (UPX) and appends the .crypt extension to the encrypted files, among them being .RAW, .ZST, .CSV, .IMG, .ISO, SQL, TAR, TGZ, .DAT, .GZ, .DUMP.
Campaigns this year
Breaching the target is done through carefully prepared phishing emails that impersonate well-known organizations - RBC media group, consultant groups, developers of management systems, lobby groups, Minsk Tractor Works, a dental clinic, financial entities, law firms, a company in the metals and mining industry.
In campaigns this year, OldGremlin also started with a malicious email but changed the malware delivery method. Instead of distributing the initial stage payload directly through a malicious document, the attacker switched to tricking the victim into downloading the document from a file-sharing service.
The first payload is TinyFluff, a NodeJS backdoor that provides remote access to the system and the possibility to download additional payloads.
OldGremlin stays on the victim network for more than a month (49 days on average), collecting information that allows the discovery of high-value systems for encryption.
The group relies on a self-developed toolkit that includes the following:
- a reconnaissance tool
- malicious LNK files
- multiple backdoors (TinyPosh, TinyNode, TinyFluff, TinyShell)
- tool to extract data from Credential Manager
- tool to bypass antivirus software
- tool to isolate a device from the network
- TinyCrypt ransomware
The toolkit strongly suggests that OldGremlin is a highly skilled actor carefully preparing attacks to leave its victims with no other choice but to pay the ransom.
Apart from the custom tools, the attacker also uses open-source and commercial frameworks like PowerSploit and Cobalt Strike.
OldGremlin attacks this year come after a period of relative stagnation in 2021 when the group carried out just one phishing campaign and demanded $4.2 million from the victim.
The total number of attacks that researchers attribute to OldGremlin has now reached 16, most of them dating from 2020.
Although most ransomware gangs avoid targets in Russia and the countries in the Commonwealth of Independent States (CIS) region, Russian companies are still targeted for file-encrypting attacks.
"OldGremlin has debunked the myth that ransomware groups are indifferent to Russian companies. According to our data, the gang’s track record includes almost twenty attacks with multi-million ransom demands, with large companies becoming their preferred targets more often" - Ivan Pisarev, Head of Dynamic Malware Analysis Team at Group-IB
Several groups do not align with this rule, which is followed by the letter by Russian cybercriminals, Dharma, Crylock, and Thanos being some of the most active in 2021.
- Karlston and Matt
-

 2
2




Recommended Comments
There are no comments to display.