The North Korean APT group 'Lazarus' (APT38) is exploiting VMWare Horizon servers to access the corporate networks of energy providers in the United States, Canada, and Japan.
Lazarus is a state-backed threat actor known for conducting espionage, data theft, and cryptocurrency stealing campaigns over the past decade. The threat actors are responsible for hundreds of sophisticated attacks internationally.
According to researchers at Cisco Talos, who uncovered the latest operation, Lazarus targeted the energy organizations between February and July 2022, leveraging public VMWare Horizon exploits for initial access.
From there, they used custom malware families like 'VSingle' and 'YamaBot' and a previously unknown remote access trojan (RAT) named 'MagicRAT' that is used to search for and steal data from infected devices.
Symantec's threat hunters analyzed the same campaign in April and ASEC researchers in May. However, Cisco's report goes deeper to unveil many more details about the threat actor's activity.
Multiple attack strategies
Cisco Talos presents several attack strategies that illustrate Lazarus' latest techniques, tactics, and procedures (TTPs) and highlight the versatility of the sophisticated hacking group.
In the first case, the threat actors exploit VMWare servers vulnerable to Log4Shell flaws to run shellcode that establishes a reverse shell for running arbitrary commands on the compromised endpoint.
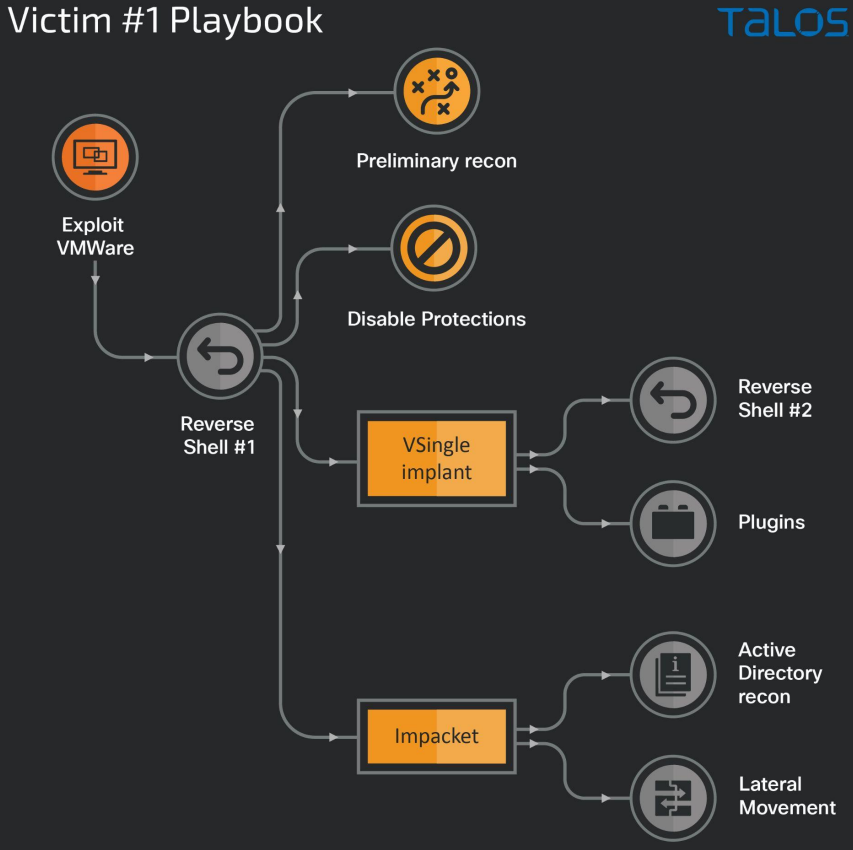
Since VMWare Horizon runs with high privileges, Lazarus can deactivate Windows Defender via registry key modifications, WMIC, and PowerShell commands before deploying VSingle.
The VSingle backdoor supports advanced network reconnaissance commands, prepares the ground for stealing credentials, creates new admin users on the host, and finally establishes a reverse shell connection with the C2 to fetch plugins that enrich its functionality.
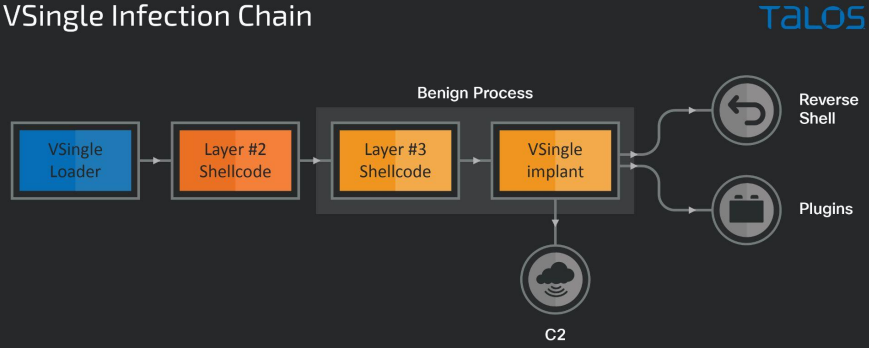
In the second case presented in the report, which concerns a different victim, the initial access and reconnaissance follow similar patterns, but this time, the hackers dropped MagicRAT along with VSingle.
Talos published a separate post on MagicRAT yesterday, detailing all the functions of this previously unseen trojan.
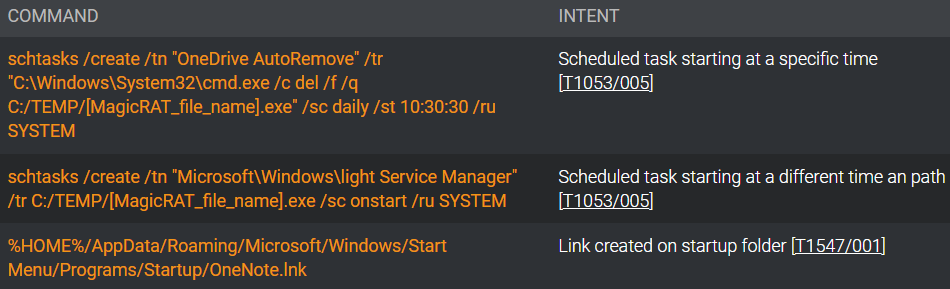
MagicRAT can establish persistence on its own by executing hardcoded commands that create the required scheduled tasks, help in system reconnaissance, and fetch additional malware from C2, like the TigerRAT.
In the third intrusion case, Lazarus deploys YamaBot, a custom malware written in Go, featuring standard RAT capabilities such as:
- List files and directories.
- Send process information to C2.
- Download files from remote locations.
- Execute arbitrary commands on the endpoints.
- Uninstall itself
The Japanese CERT linked YamaBot with Lazarus in July 2022, highlighting its encrypted C2 communication capabilities.
Lazarus attack chain diversification isn’t limited to the final malware payloads but extends to the proxy or reverse tunneling tools and credential harvesting techniques.
In some cases, the hackers employed the Mimikatz and Procdump tools, while in others, they exfiltrated copies of registry hives containing AD credentials.
“In one instance, the attackers tried to obtain Active Directory information on one endpoint via PowerShell cmdlets. However, a day later, the attackers used adfind.exe to extract similar information on the same endpoint,” explains Cisco Talos in the report.
The idea behind these variations is to mix up TTPs and make attribution, detection, and defense more challenging for incident responders.
As highlighted in this report, Lazarus is closely monitored by cybersecurity firms, so they can't afford to become lazy in diversifying their attack chains.
This diversification in attacks is illustrated in the Lazarus hacker's wide range of attacks, including their targeting of IT job seekers, the creation of fake cryptocurrency trading apps, the creation of trojanized development tools, the use of ransomware as decoys, and the massive $620 million theft of cryptocurrency theft from the Ronin bridge.
Source: Bleeping Computer
- aum
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.