North Korean hackers are using a new version of the DTrack backdoor to attack organizations in Europe and Latin America.
DTrack is a modular backdoor featuring a keylogger, a screenshot snapper, a browser history retriever, a running processes snooper, an IP address and network connection information snatcher, and more.
Apart from spying, it can also run commands to perform file operations, fetch additional payloads, steal files and data, and execute processes on the compromised device.
The new malware version doesn't feature many functional or code changes compared to samples analyzed in the past, but it is now deployed far more widely.
A wider distribution
As Kaspersky explains in a report published today, their telemetry shows DTrack activity in Germany, Brazil, India, Italy, Mexico, Switzerland, Saudi Arabia, Turkey, and the United States.
The targeted sectors include government research centers, policy institutes, chemical manufacturers, IT service providers, telecommunication providers, utility service providers, and education.
In the new campaign, Kaspersky has seen DTrack distributed using filenames commonly associated with legitimate executables.
For example, one sample they shared is distributed under the 'NvContainer.exe' file name, which is the same name as a legitimate NVIDIA file.
Kaspersky told BleepingComputer that DTrack continues to be installed by breaching networks using stolen credentials or exploiting Internet-exposed servers, as seen in previous campaigns.
When launched, the malware goes through multiple decryption steps before its final payload is loaded via process hollowing into an "explorer.exe" process, running directly from memory.
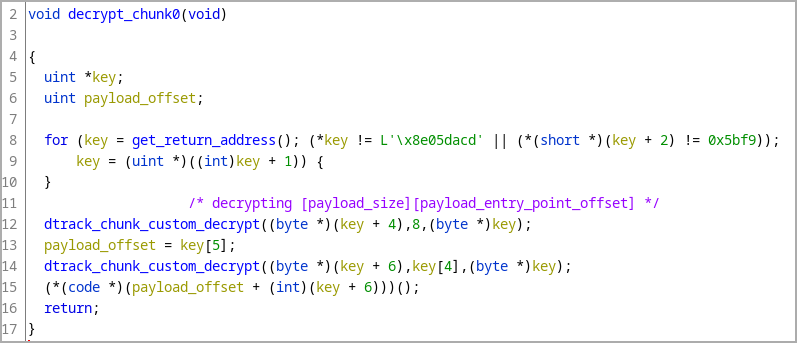
Chunk decryption routine (Kaspersky)
The only differences to past DTrack variants are it now uses API hashing to load libraries and functions instead of obfuscated strings, and that the number of C2 servers has been cut by half to just three.
Some of the C2 servers uncovered by Kaspersky are “pinkgoat[.]com”, “purewatertokyo[.]com”, “purplebear[.]com”, and “salmonrabbit[.]com.”
DTrack attribution
Kaspersky attributes this activity to the North Korean Lazarus hacking group and claims the threat actors use DTrack whenever they see the potential for financial gains.
In August 2022, the same researchers linked the backdoor to the North Korean hacking group tracked as 'Andariel,' which deployed Maui ransomware in corporate networks in the U.S. and South Korea.
In February 2020, Dragos linked DTrack to a North Korean threat group, 'Wassonite,' which attacked nuclear energy and oil and gas facilities.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.