A "by-design flaw" uncovered in Microsoft Azure could be exploited by attackers to gain access to storage accounts, move laterally in the environment, and even execute remote code.
"It is possible to abuse and leverage Microsoft Storage Accounts by manipulating Azure Functions to steal access-tokens of higher privilege identities, move laterally, potentially access critical business assets, and execute remote code (RCE)," Orca said in a new report shared with The Hacker News.
The exploitation path that underpins this attack is a mechanism called Shared Key authorization, which is enabled by default on storage accounts.
According to Microsoft, Azure generates two 512-bit storage account access keys when creating a storage account. These keys can be used to authorize access to data via Shared Key authorization, or via SAS tokens that are signed with the shared key.
"Storage account access keys provide full access to the configuration of a storage account, as well as the data," Microsoft notes in its documentation. "Access to the shared key grants a user full access to a storage account's configuration and its data."
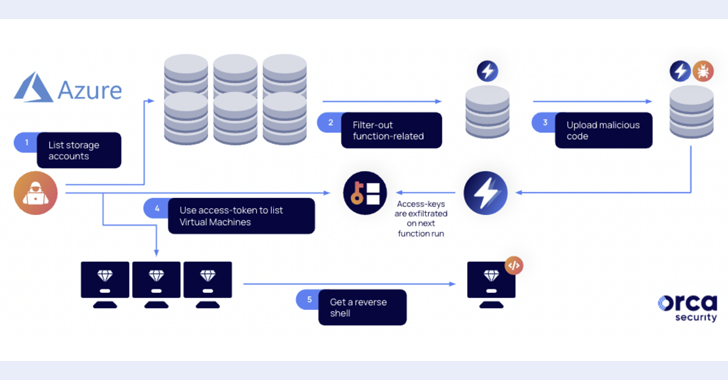
The cloud security firm said these access tokens can be stolen by manipulating Azure Functions, potentially enabling a threat actor with access to an account with Storage Account Contributor role to escalate privileges and take over systems.
Specifically, should a managed identity be used to invoke the Function app, it could be abused to execute any command. This, in turn, is made possible owing to the fact that a dedicated storage account is created when deploying an Azure Function app.
"Once an attacker locates the storage account of a Function app that is assigned with a strong managed identity, it can run code on its behalf and as a result acquire a subscription privilege escalation (PE)," Orca researcher Roi Nisimi said.
In other words, by exfiltrating the access-token of the Azure Function app's assigned managed identity to a remote server, a threat actor can elevate privileges, move laterally, access new resources, and execute a reverse shell on virtual machines.
"By overriding function files in storage accounts, an attacker can steal and exfiltrate a higher-privileged identity and use it to move laterally, exploit and compromise victims' most valuable crown jewels," Nisimi explained.
As mitigations, it's recommended that organizations consider disabling Azure Shared Key authorization and using Azure Active Directory authentication instead. In a coordinated disclosure, Microsoft said it "plans to update how Functions client tools work with storage accounts."
"This includes changes to better support scenarios using identity. After identity-based connections for AzureWebJobsStorage are generally available and the new experiences are validated, identity will become the default mode for AzureWebJobsStorage, which is intended to move away from shared key authorization," the tech giant further added.
The findings arrive weeks after Microsoft patched a misconfiguration issue impacting Azure Active Directory that made it possible to tamper with Bing search results and a reflected XSS vulnerability in Azure Service Fabric Explorer (SFX) that could lead to unauthenticated remote code execution.
- Karlston
-

 1
1


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.