A newly discovered multistage remote access trojan (RAT) dubbed ZuoRAT has been used to target remote workers via small office/home office (SOHO) routers across North America and Europe undetected since 2020.
In a report today, security researchers at Lumen’s Black Lotus Labs who spotted the malware said that this highly targeted campaign's complexity and the attackers' tactics, techniques, and procedures (TTPs) are the hallmarks of a state-backed threat actor.
The start of this campaign roughly lines up with a quick shift to remote work after the start of the COVID-19 pandemic which drastically increased the number of SOHO routers (including ASUS, Cisco, DrayTek, and NETGEAR) used by employees to access corporate assets from home.
"This gave threat actors a fresh opportunity to leverage at-home devices such as SOHO routers – which are widely used but rarely monitored or patched – to collect data in transit, hijack connections, and compromise devices in adjacent networks," Lumen says.
"The sudden shift to remote work spurred by the pandemic allowed a sophisticated adversary to seize this opportunity to subvert the traditional defense-in-depth posture of many well-established organizations."
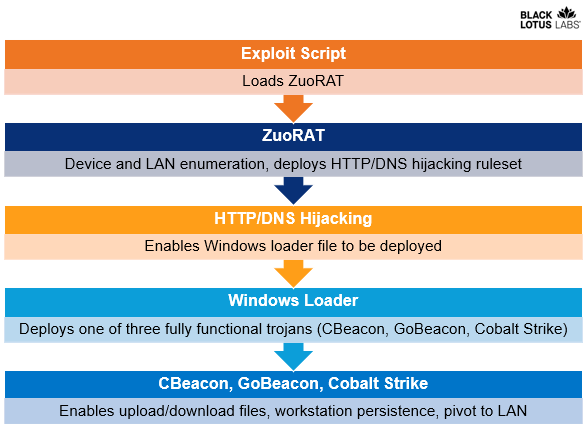
Once deployed on a router (unpatched against known security flaws) with the help of an authentication bypass exploit script, the multi-stage ZuoRAT malware provided the attackers with in-depth network reconnaissance capabilities and traffic collection via passive network sniffing.
ZuoRAT also allows moving laterally to compromise other devices on the network and to deploy additional malicious payloads (such as Cobalt Strike beacons) using DNS and HTTP hijacking.
Two more custom trojans were delivered onto hacked devices during these attacks: one C++ based one named CBeacon targeting Windows workstations and a Go-based one dubbed GoBeacon that could likely infect Linux and Mac systems besides Windows devices.
ZuoRAT campaign (Lumen Black Lotus Labs
"The capabilities demonstrated in this campaign – gaining access to SOHO devices of different makes and models, collecting host and LAN information to inform targeting, sampling and hijacking network communications to gain potentially persistent access to in-land devices and intentionally stealth C2 infrastructure leveraging multi-stage siloed router to router communications – points to a highly sophisticated actor that we hypothesize has been living undetected on the edge of targeted networks for years," the researchers added.
The additional malware deployed onto systems within victims' networks (i.e., CBeacon, GoBeacon, and Cobalt Strike) provided the threat actors with the ability to download and upload files, run arbitrary commands, hijack network traffic, inject new processes, and gain persistence on compromised devices.
Some compromised routers were also added to a botnet and used to proxy command and control (C2) traffic to hinder defenders' detection efforts.
Based on the age of VirusTotal submitted samples and nine months' worth of Black Lotus Labs telemetry, the researchers estimate that the campaign has so far impacted at least 80 targets.
"Organizations should keep a close watch on SOHO devices and look for any signs of activity outlined in this research," said Mark Dehus, Black Lotus Labs' director of threat intelligence.
"This level of sophistication leads us to believe this campaign might not be limited to the small number of victims observed. To help mitigate the threat, they should ensure patch planning includes routers, and confirm these devices are running the latest software available."
New ZuoRAT malware targets SOHO routers in North America, Europe
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.