An unknown threat actor has been targeting Russian entities with a newly discovered remote access trojan called Woody RAT for at least a year as part of a spear-phishing campaign.
The advanced custom backdoor is said to be delivered via either of two methods: archive files and Microsoft Office documents leveraging the now-patched "Follina" support diagnostic tool vulnerability (CVE-2022-30190) in Windows.
Like other implants engineered for espionage-oriented operations, Woody RAT sports a wide range of features that enables the threat actor to remotely commandeer and steal sensitive information from the infected systems.
"The earliest versions of this RAT were typically archived into a ZIP file pretending to be a document specific to a Russian group," Malwarebytes researchers Ankur Saini and Hossein Jazi said in a Wednesday report.
"When the Follina vulnerability became known to the world, the threat actor switched to it to distribute the payload."
In one instance, the hacking group attempted to strike a Russian aerospace and defense entity known as OAK based on evidence gleaned from a fake domain registered for this purpose.
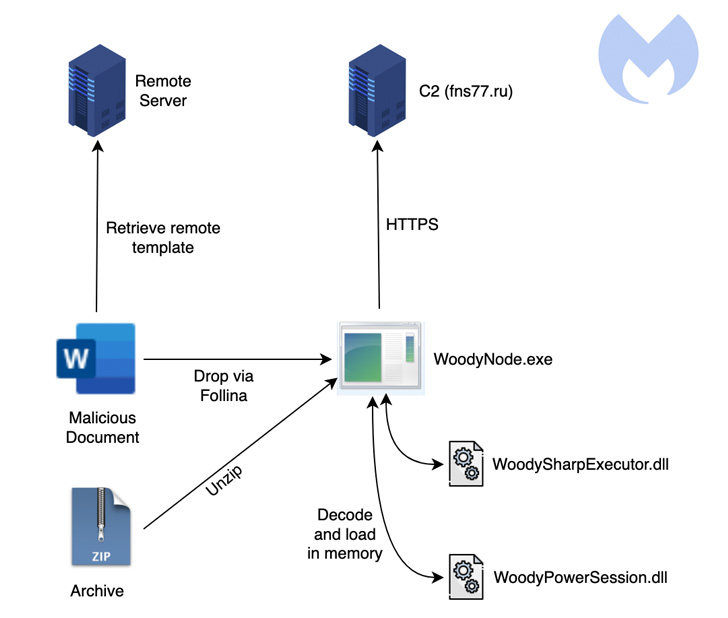
Attacks leveraging the Windows flaw as part of this campaign first came to light on June 7, 2022, when researchers from the MalwareHunterTeam disclosed the use of a document named "Памятка.docx" (which translates to "Memo.docx") to deliver a CSS payload containing the trojan.
The document purportedly offers best security practices for passwords and confidential information, among others, while acting as a decoy for dropping the backdoor.
Besides encrypting its communications with a remote server, Woody RAT is equipped with capabilities to write arbitrary files to the machine, execute additional malware, delete files, enumerate directories, capture screenshots, and gather a list of running processes.
Also embedded within the malware are two .NET-based libraries named WoodySharpExecutor and WoodyPowerSession that can be used to run .NET code and PowerShell commands received from the server, respectively.
Furthermore, the malware makes use of the process hollowing technique to inject itself into a suspended Notepad process and deletes itself from the disk to evade detection from security software installed on the compromised host.
Malwarebytes has yet to attribute the attacks to a specific threat actor, citing a lack of solid indicators linking the campaign to a previously known group, although Chinese and North Korean nation-state collectives have targeted Russia in the past.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.