Security researchers found a previously unknown backdoor they call Dophin that's been used by North Korean hackers in highly targeted operations for more than a year to steal files and send them to Google Drive storage.
According to research from cybersecurity company ESET, the APT 37 threat group (a.k.a. Reaper, Red Eyes, Erebus, ScarCruft) used the newly discovered malware against very specific entities. The group has been associated with espionage activity aligining with North Korean interests since 2012.
The researchers found Doplphin in April 2021 and observed it evolve into new versions with improved code and anti-detection mechanisms.
Beyond BLUELIGHT
Dolphin is used together with BLUELIGHT, a basic reconnaissance tool seen in previous APT37 campaigns, but it features more powerful capabilities like stealing information from web browsers (passwords), taking screenshots, and logging keystrokes.
BLUELIGHT is used to launch Dolphin's Python loader on a compromised system but has a limited role in espionage operations.
The Python loader includes a script and shellcode, launching a multi-step XOR-decryption, process creation, etc., eventually resulting in the execution of the Dolphin payload in a newly created memory process.

APT37 observed infection chain
(ESET)
Dolphin is a C++ executable using Google Drive as a command and control (C2) server and to store stolen files. The malware establishes persistence by modifying the Windows Registry.
Dolphin capabilities
During the initial stage, Dolphin collects the following information from the infected machine:
- Username
- Computer name
- Local and external IP address
- Installed security software
- RAM size and usage
- Presence of debugging or network packet inspection tools
- OS version
The backdoor also sends to the C2 its current configuration, version number, and time.
The configuration contains keylogging and file exfiltration instructions, credentials for Google Drive API access, and encryption keys.
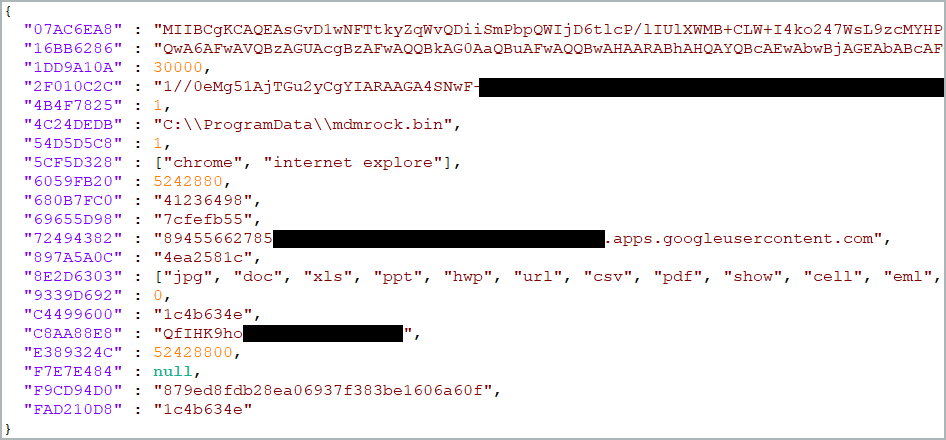
Dolphin's configuration (ESET)
The researchers say that the hackers delivered their commands to Dolphin by uploading them on Google Drive. In response, the backdoor uploads the result from executing the commands.
The malware has an extended set of capabilities that includes scanning local and removable drives for various types of data (media, documents, emails, certificates) that is archived and delivered to Google Drive. This feature was further improved to filter data by extension.
Stealing files from connected phone
Its search capabilities extend to any phone connected to the compromised host by using the Windows Portable Device API.
ESET notes that this functionality appeared to be under development in the first version of the malware they found. Evidence pointing to this was:
- use of a hardcoded path with a username that likely doesn’t exist on the victim’s computer
- missing variable initialization – some variables are assumed to be zero-initialized, or dereferenced as pointers without initialization
- missing extension filtering
Additionally, it can also lower the security a victim's Google account by changing related settings. This could allow attackers keep their access to the victim account for a longer period.
Dophin can record user keystrokes in Google Chrome by abusing the 'GetAsyncKeyState' API and it can take a snapshot of the active window every 30 seconds.
ESET researchers caught four distinct versions for the Dolphin backdoor, the latest being 3.0 from January 2022.
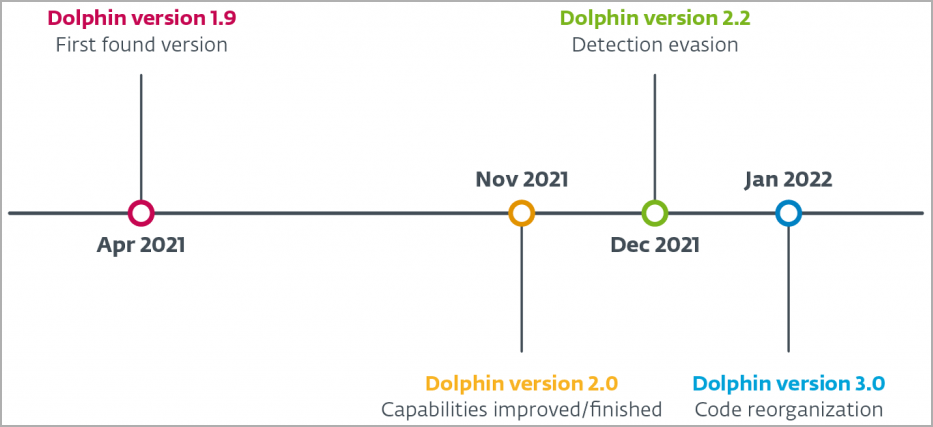
Dolphin versions timeline (ESET)
It's possible that newer versions of Dolphin exist and have been used in attacks, given that the backdoor has been deployed against select targets.
According to the researchers, the malware was used in a watering-hole attack on a South Korean paper reporting on activity and events related to North Korea. The hackers relied on an Internet Explorer exploit to ultimately deliver Dolphin backdoor to the target hosts.
ESET's report provides a list of hashes for Dolphin backdoor versions 1.9 through 3.0 (86/64-bit).




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.