A new information-stealing malware named 'StrelaStealer' is actively stealing email account credentials from Outlook and Thunderbird, two widely used email clients.
This behavior deviates from most info-stealers, which attempt to steal data from various data sources, including browsers, cryptocurrency wallet apps, cloud gaming apps, the clipboard, etc.
The previously unknown malware was discovered by analysts at DCSO CyTec, who report that they first saw it in the wild in early November 2022, targeting Spanish-speaking users.
Polyglot file infection
StrelaStealer arrives on the victim's system via email attachments, currently ISO files with varying content.
In one example, the ISO contains an executable ('msinfo32.exe') that sideloads the bundled malware via DLL order hijacking.
In a more interesting case seen by the analysts, the ISO contains an LNK file ('Factura.lnk') and an HTML file ('x.html'). The x.html file is of particular interest because it is a polyglot file, which is a file that can be treated as different file formats depending on the application that opens it.
.png)
Diagram of the infection process - Source: DCSO CyTec
In this case, x.html is both an HTML file and a DLL program that can load the StrelaStealer malware or display a decoy document in the default web browser.
When the Fractura.lnk file is executed, it will execute x.html twice, first using rundll32.exe to run the embedded StrelaStealer DLL and another time as HTML to load the decoy document in the browser, as shown in the image below.
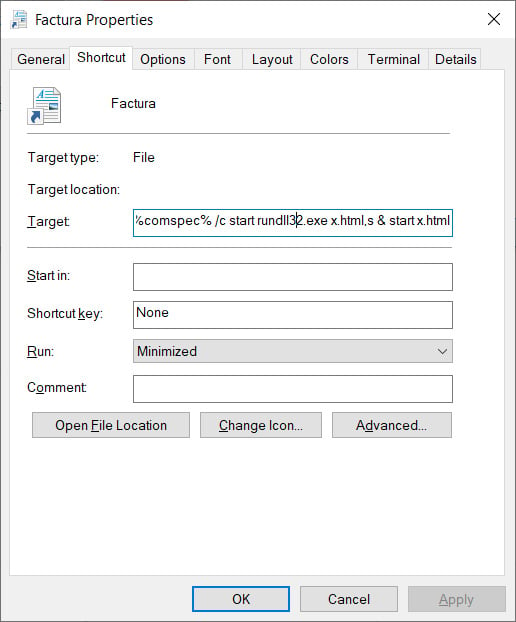
LNK file loading the DLL and decoy image from x.html - Source: BleepingComputer
Once the malware is loaded in memory, the default browser is opened to show the decoy to make the attack less suspicious.
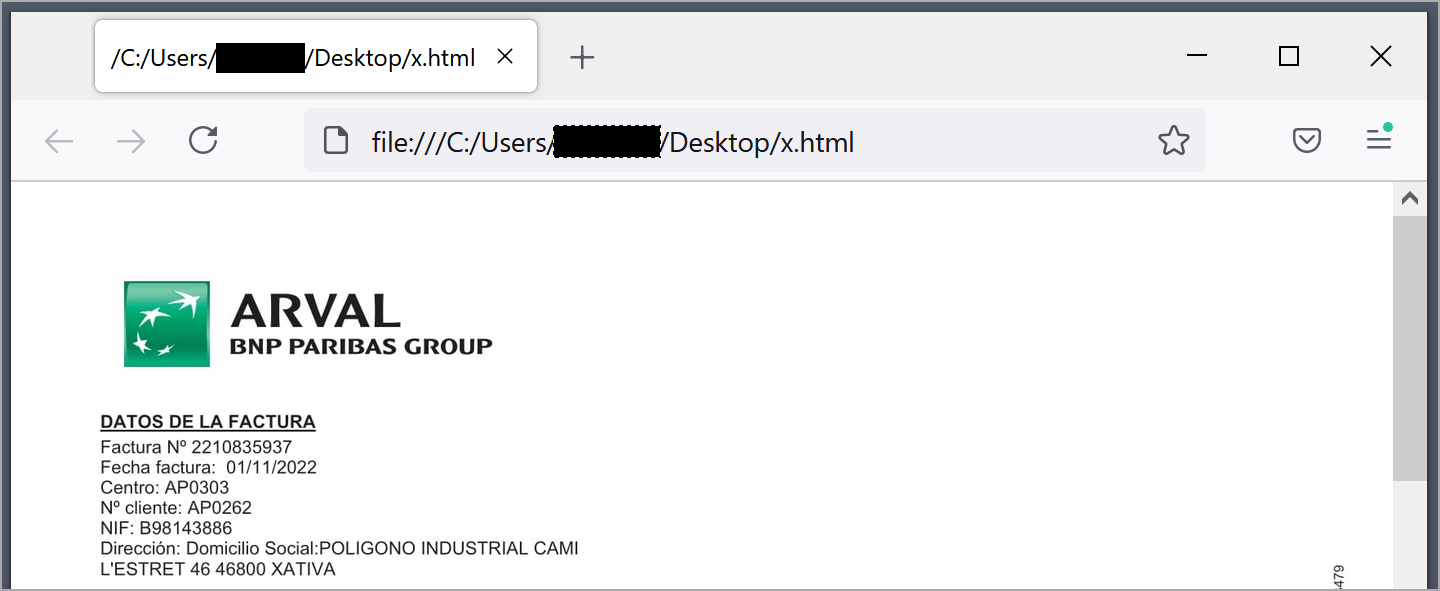
StrelaStealer details
Upon execution, StrelaStealer searches the '%APPDATA%\Thunderbird\Profiles\' directory for 'logins.json' (account and password) and 'key4.db' (password database) and exfiltrates their contents to the C2 server.
For Outlook, StrelaStealer reads the Windows Registry to retrieve the software's key and then locates the 'IMAP User', 'IMAP Server', and 'IMAP Password' values.
The IMAP Password contains the user password in encrypted form, so the malware uses the Windows CryptUnprotectData function to decrypt it before it's exfiltrated to the C2 along with the server and user details.
Finally, StrelaStealer validates that the C2 received the data by checking for a specific response and quits when it receives it. Otherwise, it enters a 1-second sleep and retries this data-theft routine.
Since the malware is spread using Spanish-language lures and focuses on very specific software, it may be used in highly targeted attacks. However, DCSO CyTec couldn't determine more about its distribution.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.