A new campaign conducted by the TA558 hacking group is concealing malicious code inside images using steganography to deliver various malware tools onto targeted systems.
Steganography is the technique of hiding data inside seemingly innocuous files to make them undetectable by users and security products.
TA558 is a threat actor that has been active since 2018, known for targeting hospitality and tourism organizations worldwide, focusing on Latin America.
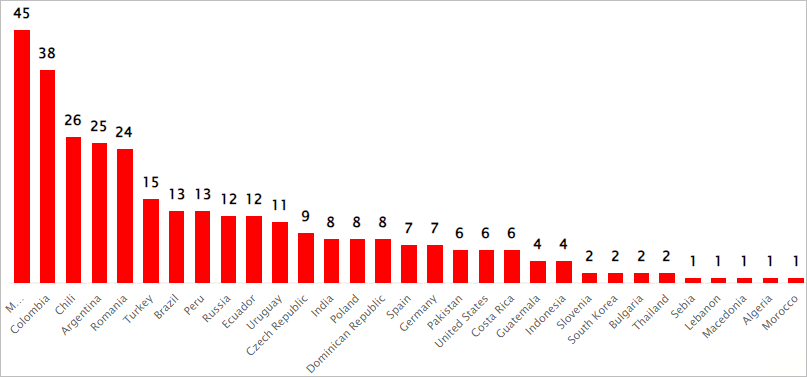
The group's latest campaign, dubbed "SteganoAmor" due to the extensive use of steganography, was uncovered by Positive Technologies. The researchers identified over 320 attacks in this campaign that affected various sectors and countries.
SteganoAmor attacks
The attacks begin with malicious emails containing seemingly innocuous document attachments (Excel and Word files) that exploit the CVE-2017-11882 flaw, a commonly targeted Microsoft Office Equation Editor vulnerability fixed in 2017.
The emails are sent from compromised SMTP servers to minimize the chances of the messages getting blocked as they come from legitimate domains.
If an old version of Microsoft Office is installed, the exploit will download a Visual Basic Script (VBS) from the legitimate 'paste upon opening the file. ee' service. This script is then executed to fetch an image file (JPG) containing a base-64 encoded payload.
PowerShell code inside the script contained in the image downloads the final payload hidden inside a text file in the form of a reversed base64-encoded executable.
Positive Technologies has observed several variants of the attack chain, delivering a diverse array of malware families, including:
- AgentTesla – Spyware that functions as a keylogger and a credential stealer, capturing keystrokes, system clipboard data, taking screenshots, and exfiltrating other sensitive information.
- FormBook – Infostealer malware that harvests credentials from various web browsers, collects screenshots, monitors and logs keystrokes, and can download and execute files according to the commands it receives.
- Remcos – Malware that allows the attacker to remotely manage a compromised machine, executing commands, capturing keystrokes, and turning on the webcam and microphone for surveillance.
- LokiBot – Info-stealer that targets data such as usernames, passwords, and other information related to many commonly used applications.
- Guloader – Downloader that is used to distribute secondary payloads, typically packed to evade antivirus detection.
- Snake Keylogger – Data-stealing malware that logs keystrokes, collects system clipboard data, captures screenshots, and harvests credentials from web browsers.
- XWorm – Remote Access Trojan (RAT) that gives the attacker remote control over the infected computer.
The final payloads and malicious scripts are often stored in legitimate cloud services like Google Drive, taking advantage of their good reputation to evade getting flagged by AV tools.
Stolen information is sent to compromised legitimate FTP servers used as command and control (C2) infrastructure to make the traffic appear normal.
Positive Technologies discovered over 320 attacks, most focused in Latin American countries, but the targeting scope extends worldwide.
Using a seven-year bug in TA558's attack chain makes it fairly easy to defend against SteganoAmor, as updating Microsoft Office to a more recent version would render these attacks ineffective.
A complete list of the indicators of compromise (IoCs) is available at the bottom of the report.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.