Technical information has emerged for a serious vulnerability affecting multiple Linux kernel versions that could be triggered with "minimal capabilities." The security issue is being referred to as StackRot (CVE-2023-3269) and can be used to compromise the kernel and elevate privileges.
A patch is available for the affected stable kernels since July 1st and full details about the issue along with a complete exploit code are expected by the end of the month.
Security researcher Ruihan Li discovered and reported the vulnerability. He explains in a post today that it affects the kernel's memory management subsystem, a component in charge with implementing the virtual memory and demand paging, memory allocation for the kernel's needs and the user space programs, as well as mapping files into the processes' address space.
StackRot impacts all kernel configurations on Linux versions 6.1 through 6.4.
Although Li sent the vulnerability report on June 15th, creating a fix took almost two weeks due to its complexity, and Linus Torvalds led the effort.
"On June 28th, during the merge window for Linux kernel 5.5, the fix was merged into Linus' tree. Linus provided a comprehensive merge message to elucidate the patch series from a technical perspective. These patches were subsequently backported to stable kernels (6.1.37, 6.3.11, and 6.4.1), effectively resolving the "Stack Rot" bug on July 1st," the researcher clarified.
StackRot details
StackRot arises from the Linux kernel's handling of stack expansion within its memory management subsystem, tied to managing virtual memory areas (VMAs).
Specifically, the weak spot is in "maple tree," a new data structure system for VMAs introduced in Linux kernel 6.1 that replaced the "red-black trees" and relied on the read-copy-update (RCU) mechanism.
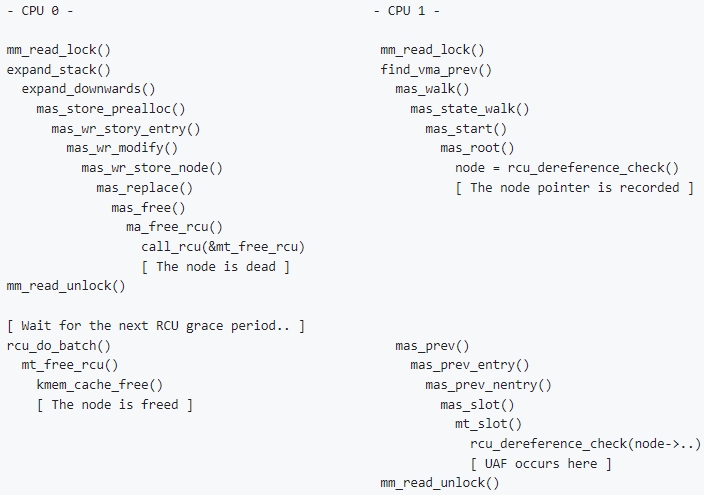
The vulnerability is a use-after-free (UAF) problem stemming from the way stack expansion was handled, because the maple tree could replace a node without obtaining the memory management (MM) write lock.
As the Linux kernel expands the stack and removes the gap between VMAs, a new node is created in the "maple tree," and the old one is marked for deletion after current reads finish due to the maple tree's RCU safety.
However, during the RCU grace period, a use-after-free issue may occur when a process accesses the old node, thus creating an exploitable context for elevating privileges.
Exploit coming
Ruihan Li notes that exploiting StackRot is a challenging task and that CVE-2023-3269 may be the first example of a theoretically exploitable use-after-free-by-RCU (UAFBR) vulnerability.
However, the researcher announced plans to disclose the complete technical details about StackRot and a proof-of-concept (PoC) exploit by the end of July.
Linux kernel 6.1 has been approved as the long-term support (LTS) version since February. However, not all major Linux distributions have adopted it.
For instance, Ubuntu 22.04.2 LTS (Jammy Jellyfish), whose standard support ends in April 2027, ships with Linux kernel version 5.19. On the other hand, Debian 12 (Bookworm) comes with Linux kernel 6.1.
A complete list of Linux distributions using kernel version 6.1 or higher is available from DistroWatch.
Users should check the kernel version their Linux distro runs on and choose one that is not affected by StackRot or an updated release that contains the fix.
- aum
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.