A new 'White Phoenix' ransomware decryptor allows victims to partially recover files encrypted by ransomware strains that use intermittent encryption.
Intermittent encryption is a strategy employed by several ransomware groups that alternates between encrypting and not encrypting chunks of data. This method allows a file to be encrypted much faster while still leaving the data unusable by the victim.
In September 2022, Sentinel Labs reported that intermittent encryption is gaining traction in the ransomware space, with all big RaaS offering it at least as an option to affiliates and BlackCat/ALPHV having seemingly the most sophisticated implementation.
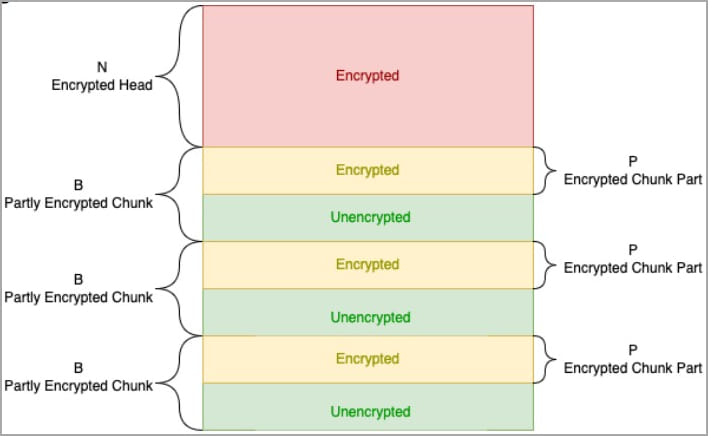
BlackCat's intermittent encryption (CyberArk)
However, according to CyberArk, which developed and published 'White Phoenix,' this tactic introduces weaknesses to the encryption, as leaving parts of the original files unencrypted creates the potential for free data recovery.
Ransomware operations that use intermittent encryption include BlackCat, Play, ESXiArgs, Qilin/Agenda, and BianLian.
Recovering partially encrypted files
CyberArk developed White Phoenix after experimenting with partially encrypted PDF files, attempting to recover text and images from stream objects.
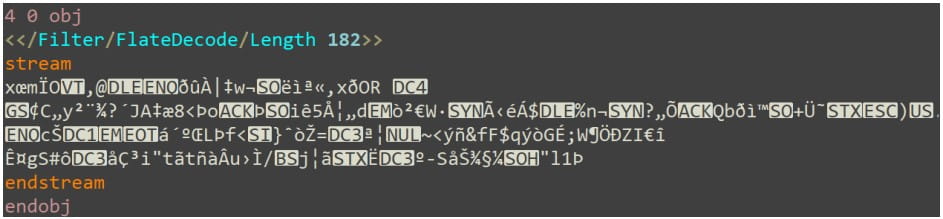
PDF's stream object sample (CyberArk)
The researchers found that in certain BlackCat encryption modes, many objects in PDF files remain unaffected, allowing the data to be extracted.
In the case of image streams, recovering them is as simple as removing the applied filters.
In the case of text recovery, the restoration methods include identifying text chunks in the streams and concatenating them or reversing hex encoding and CMAP (character mapping) scrambling.
After successfully recovering PDF files using the White Phoenix tool, CyberArk found similar restoration possibilities for other file formats, including files based on ZIP archives.
These files using the ZIP format include Word (docx, docm, dotx, dotm, odt), Excel (xlsx, xlsm, xltx, xltm, xlsb, xlam, ods), and PowerPoint (pptx, pptm, ptox, potm, ppsx, ppsm, odp) document formats.
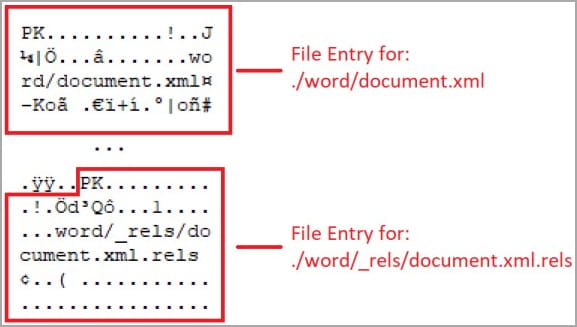
File entries in ZIP archive (CyberArk)
Restoration for these file types is achieved by using 7zip and a hex editor to extract the unencrypted XML files of impacted documents and perform data replacement.
White Phoenix automates all the above steps for supported file types, although manual intervention might be required in some cases.
The tool is available to download for free from CyberArk's public GitHub repository.
Practical limitations
The analysts report that their automated data recovery tool should work well for the mentioned file types encrypted by the following ransomware strains:
- BlackCat/ALPHV
- Play ransomware
- Qilin/Agenda
- BianLian
- DarkBit
However, it is essential to note that White Phoenix will not produce good results in every case, even if it's theoretically supported.
For example, if a large portion of a file has been encrypted, including its critical components, the recovered data may be incomplete or useless. Hence, the tool's effectiveness is directly linked to the extent of the damage to the file.
For cases where text is stored as CMAP objects in PDF files, the recovery is only possible if neither the text nor the CMAP objects are encrypted, except for rare cases where the hex encoding matches the original character values.
BleepingComputer tested White Phoenix with a small sample of ALPHV-encrypted PDF files and Play-encrypted PPTX and DOCX files and was unable to recover any data using the tool.
However, CyberArk explained that this could be caused by intermittent encryption not being used in the attacks we received samples from or the files being too heavily encrypted to be properly parsed.
"Depending on the specific ransomware sample being used, different file sizes might be too encrypted to recover data from. If the following characters aren't seen in the file, it is likely fully encrypted and White Phoenix won't be able to help," CyberArk told BleepingComputer.
For White Phoenix to work correctly, Zip/Office formats must contain the "PK\x03\x04" string in the file to be supported. In addition, PDFs need to contain "0 obj" and "endobj" strings to be partially recovered.
If White Phoenix cannot find these strings, it will state that the file type is not supported, as shown below in our limited tests.
Testing White Phoenix against a Play-encrypted file
Source: BleepingComputer
While this decryptor may not work for all files, it could be very helpful for victims to attempt to recover "some" data from critical files.
CyberArk invites all security researchers to download and try the tool and join the effort to improve it and help extend its support to more file types and ransomware strains.
- aum
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.