A number of malicious samples have been created for the Windows Subsystem for Linux (WSL) with the goal of compromising Windows machines, highlighting a sneaky method that allows the operators to stay under the radar and thwart detection by popular anti-malware engines.
The "distinct tradecraft" marks the first instance where a threat actor has been found abusing WSL to install subsequent payloads.
"These files acted as loaders running a payload that was either embedded within the sample or retrieved from a remote server and was then injected into a running process using Windows API calls," researchers from Lumen Black Lotus Labs said in a report published on Thursday.
Windows Subsystem for Linux, launched in August 2016, is a compatibility layer that's designed to run Linux binary executables (in ELF format) natively on the Windows platform without the overhead of a traditional virtual machine or dual-boot setup.
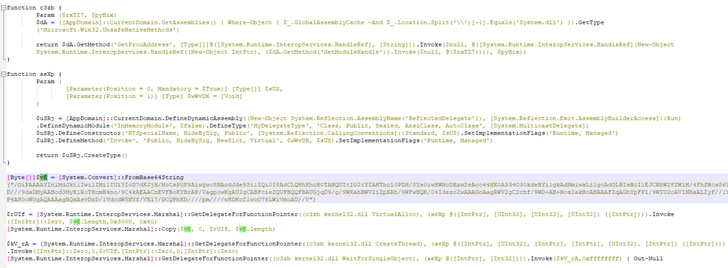
The earliest artifacts date back to May 3, 2021, with a series of Linux binaries uploaded every two to three weeks till August 22, 2021. Not only are the samples written in Python 3 and converted into an ELF executable with PyInstaller, but the files are also orchestrated to download shellcode from a remote command-and-control server and employ PowerShell to carry out follow-on activities on the infected host.
This secondary "shellcode" payload is then injected into a running Windows process using Windows API calls for what Lumen described as "ELF to Windows binary file execution," but not before the sample attempts to terminate suspected antivirus products and analysis tools running on the machine. What's more, the use of standard Python libraries makes some of the variants interoperable on both Windows and Linux.
"Thus far, we have identified a limited number of samples with only one publicly routable IP address, indicating that this activity is quite limited in scope or potentially still in development," the researchers said. "As the once distinct boundaries between operating systems continue to become more nebulous, threat actors will take advantage of new attack surfaces."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.