Hackers have found a new method to establish persistence on VMware ESXi hypervisors to control vCenter servers and virtual machines for Windows and Linux while avoiding detection.
With the help of malicious vSphere Installation Bundles, the attacker was able to install on the bare-metal hypervisor two backdoors that researchers have named VirtualPita and VirtualPie.
Researchers also uncovered a unique malware sample that they called VirtualGate, which includes a dropper and a payload.
Deceiving trust
In an incident response engagement earlier this year, security researchers at cyber threat intelligence company Mandiant (acquired by Google) found that an actor suspected to have ties with China used malicious vSphere Installation Bundles (VIBs) to deliver the VirtualPita and VirtualPie malware.
A VIB is a package of files for creating or maintaining an ESXi image. It lets the administrator manage how the ESXi installation behaves by creating startup tasks, firewall rules, or running binaries when the machine restarts.
The VIB package includes the following:
- an archive, typically referred to as "payload" files that need to be installed on the host
- an XML descriptor with information about the VIB requirements, dependencies, compatibility issues, payload to install, name, install date
- signature file that verifies the maker of the VIB and the level of trust associated with it
VIBs can be created by VMware (created and tested by the company), approved partners, or the community (not a source accepted through the VMware program, such as individuals or third-party partners).
During the investigation of the incident, Mandiant discovered that the threat actor, tracked as UNC3886, modified the acceptance level in the XML descriptor for the VBI used in the attack from 'community' to 'partner' to deceive anyone looking into it.
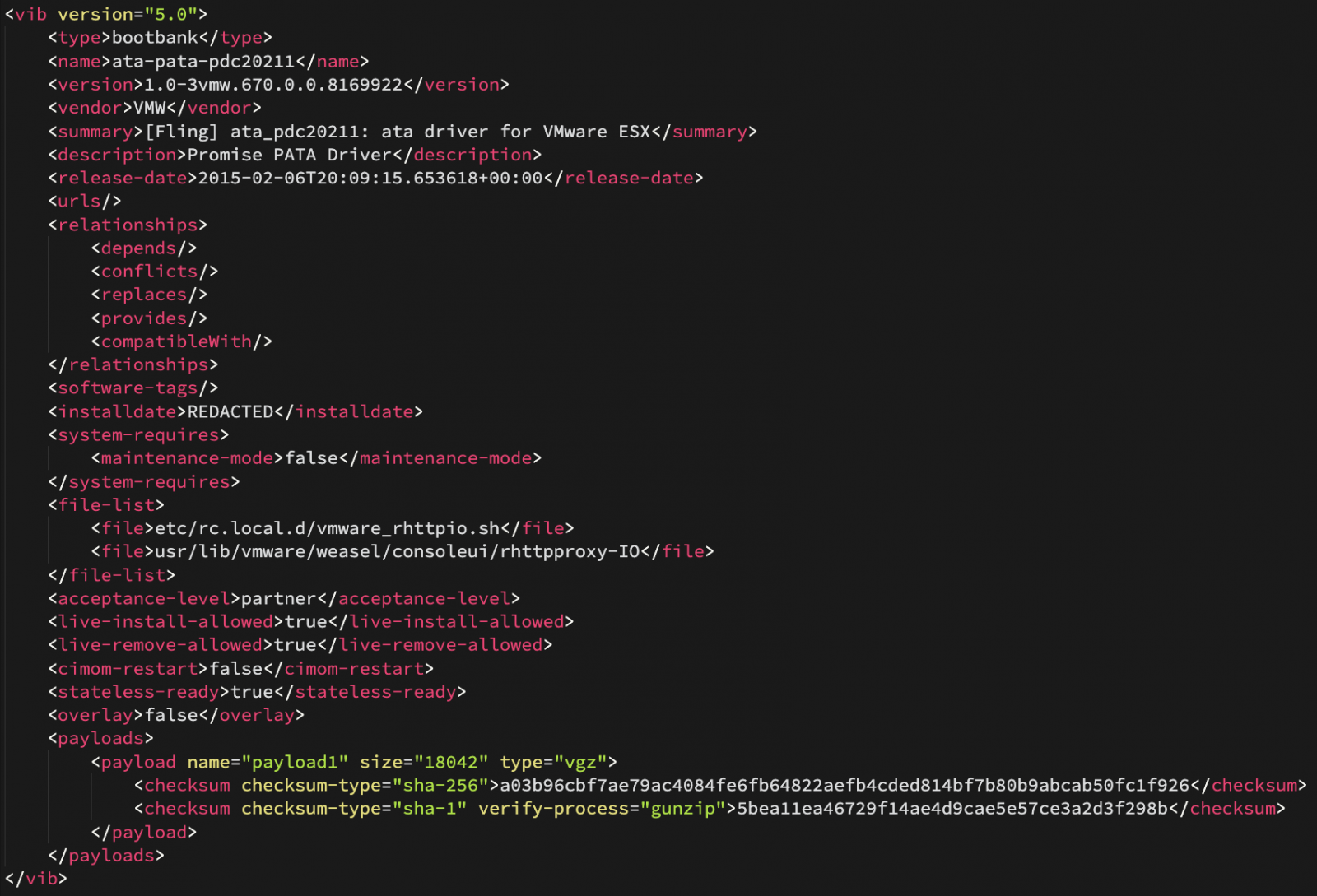
A modified level of trust is not enough for the ESXi system to accept it by default but the attacker also used the '--force' flag to install the malicious VIBs.
On closer inspection, though, the falsified VIB became evident, showing that the signature file could not be associated with a party trusted by VMware.
Using these tricks, the threat actor was able to install the VirtualPita and VirtualPie malware on the compromised ESXi machine.
"VIRTUALPITA is a 64-bit passive backdoor that creates a listener on a hardcoded port number on a VMware ESXi server," Mandiant says in a report today.
The researchers added that the backdoor often impersonates a legitimate service by using VMware service names and ports. It allows execution of arbitrary commands, uploads and downloads files, as well as starting and stopping the logging mechanism ('vmsyslogd ').
During the research, a Linux variant for VirtualPita was found persistent as an init.d startup service on Linux vCenter systems, hiding under the name of the legitimate binary ksmd.
VirtualPie is Python-based and spawns a daemonized IPv6 listener on a hardcoded port on a VMware ESXi server. It supports arbitrary command line execution, can transfer files, and set up a reverse shell.
On Windows guest virtual machines under the infected hypervisor, the researchers found another malware, VirtualGate, which includes a memory-only dropper that deobfusccates a second-stage DLL payload on the VM.
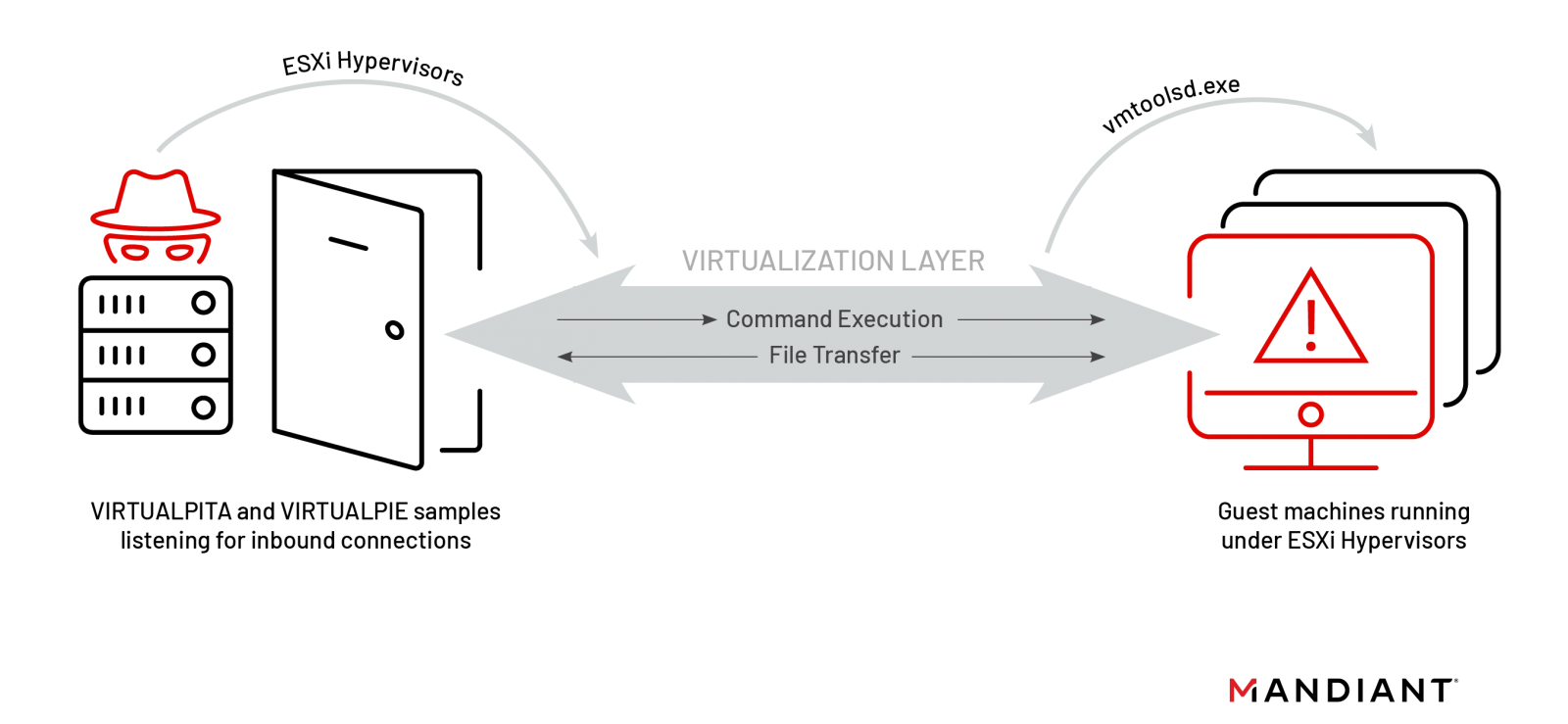
This attack requires the threat actor to have admin-level privileges to the hypervisor. While this may appear to lower the risk, adversaries often lurk on the victim network waiting for an opportunity to reach valuable assets or extend their presence.
In a separate blog post today, Mandiant provides technical details on how defenders can minimize the attack surface on ESXi hosts by detecting malicious VIBs.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.