A new data extortion group tracked as Mad Liberator is targeting AnyDesk users and runs a fake Microsoft Windows update screen to distract while exfiltrating data from the target device.
The operation emerged in July and although researchers observing the activity did not seen any incidents involving data encryption, the gang notes on their data leak site that they use AES/RSA algorithms to lock files.
Source: BleepingComputer
Targeting AnyDesk users
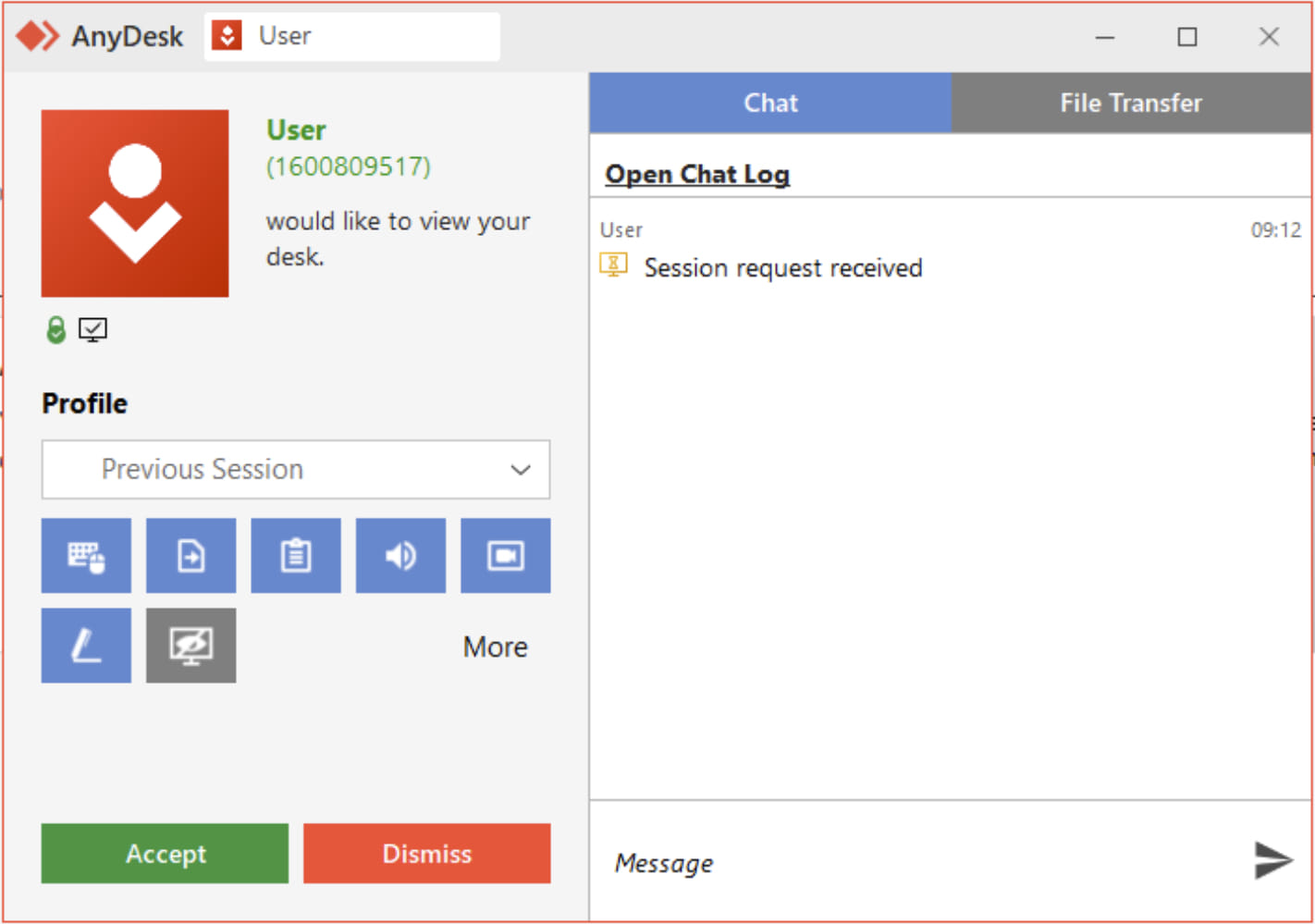
In a report from cybersecurity company Sophos, researchers say that a Mad Liberator attack starts with an unsolicited connection to a computer using AnyDesk remote access application, which is popular among IT teams managing corporate environments.
It is unclear how the threat actor selects its targets but one theory, although yet to be proven, is that Mad Liberator tries potential addresses (AnyDesk connection IDs) until someone accepts the connection request.
Source: Sophos
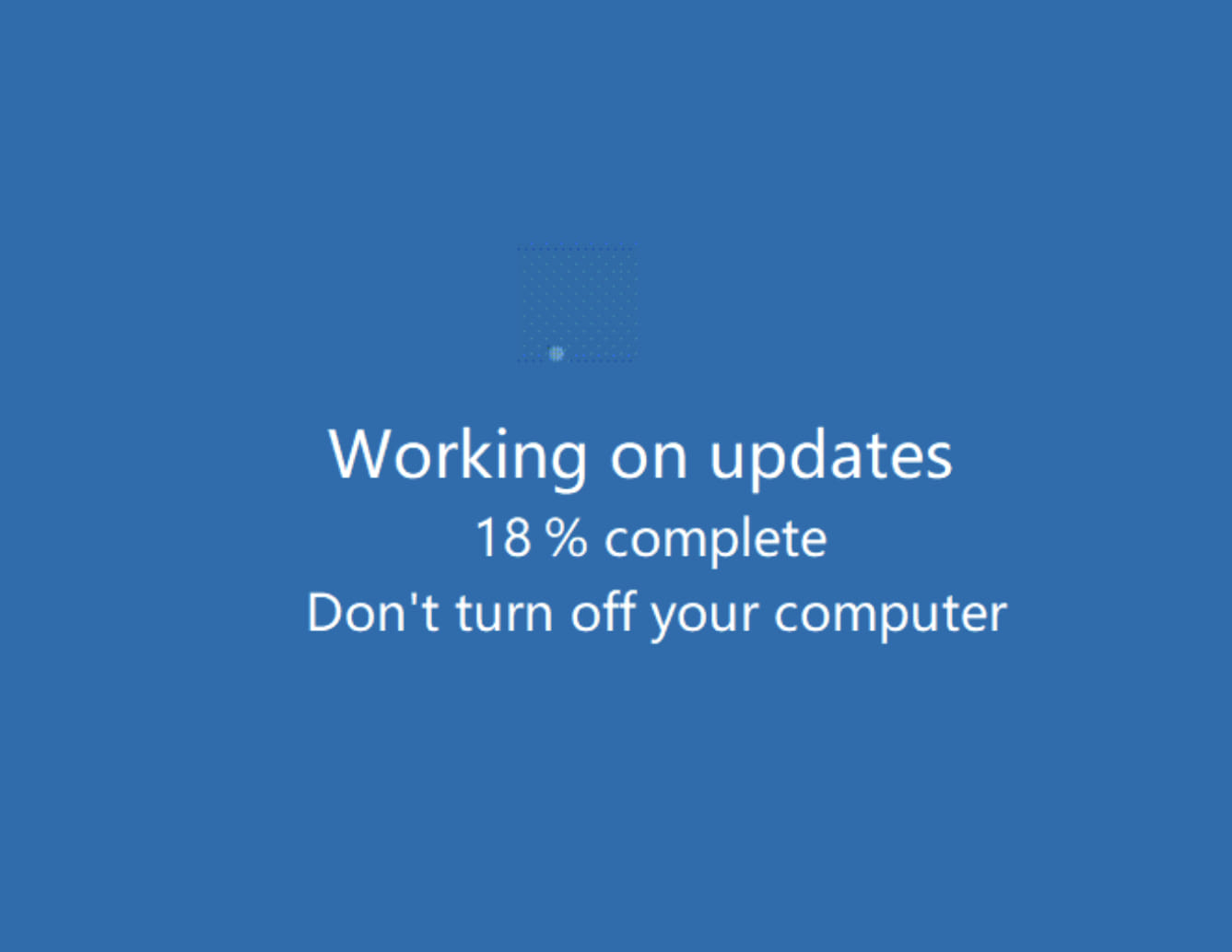
Once a connection request is approved, the attackers drop on the compromised system a binary named Microsoft Windows Update, which shows a fake Windows Update splash screen.
Source: Sophos
The only purpose of the ruse is to distract the victim while the threat actor uses AnyDesk's File Transfer tool to steal data from OneDrive accounts, network shares, and the local storage.
During the fake update screen, the victim's keyboard is disabled, to prevent disrupting exfiltration process.
In the attacks seen by Sophos, which lasted approximately four hours, Mad Liberator did not perform any data encryption in the post-exfiltration stage.
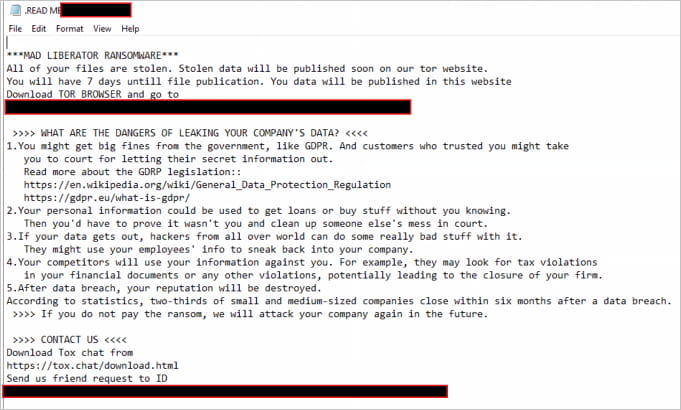
However, it still dropped ransom notes on the shared network directories to ensure maximum visibility in corporate environments.
Source: Sophos
Sophos notes that it has not seen Mad Liberator interact with the target prior to the AnyDesk connection request and has logged no phishing attempts supporting the attack.
Regarding Mad Liberator’s extortion process, the threat actors declare on their darknet site that they first contact breached firms offering to “help” them fix their security issues and recover encrypted files if their monetary demands are met.
If the victimized company does not respond in 24 hours, their name is published on the extortion portal and are given seven days to contact the threat actors.
After another five days since the ultimatum has been issued passed without a ransom payment, all stolen files are published on the Mad Liberator website, which currently lists nine victims.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every single day for many years.
2023: Over 5,800 news posts | 2024 (till end of July): 3,313 news posts



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.