Researchers this week unveiled a new strain of Linux malware that's notable for its stealth and sophistication in infecting both traditional servers and smaller Internet-of-things devices.
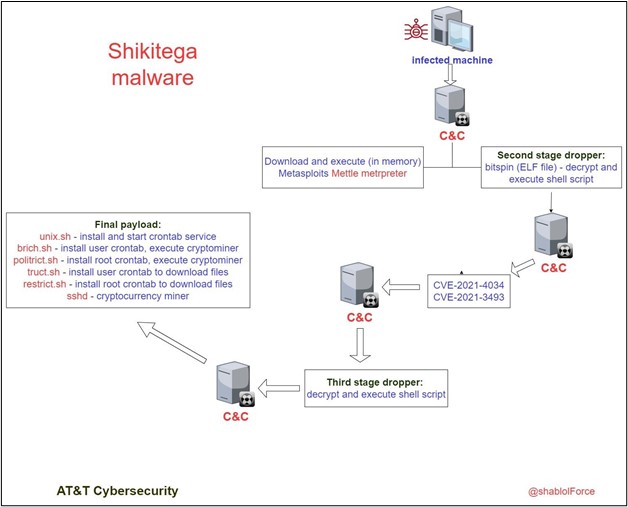
Dubbed Shikitega by the AT&T Alien Labs researchers who discovered it, the malware is delivered through a multistage infection chain using polymorphic encoding. It also abuses legitimate cloud services to host command-and-control servers. These things make detection extremely difficult.
"Threat actors continue to search for ways to deliver malware in new ways to stay under the radar and avoid detection," AT&T Alien Labs researcher Ofer Caspi wrote. "Shikitega malware is delivered in a sophisticated way, it uses a polymorphic encoder, and it gradually delivers its payload where each step reveals only part of the total payload. In addition, the malware abuses known hosting services to host its command and control servers."
The ultimate objective of the malware isn't clear. It drops the XMRig software for mining the Monero cryptocurrency, so stealthy cryptojacking is one possibility. But Shikitega also downloads and executes a powerful Metasploit package known as Mettle, which bundles capabilities including webcam control, credential stealing, and multiple reverse shells into a package that runs on everything from "the smallest embedded Linux targets to big iron." Mettle's inclusion leaves open the potential that surreptitious Monero mining isn't the sole function.
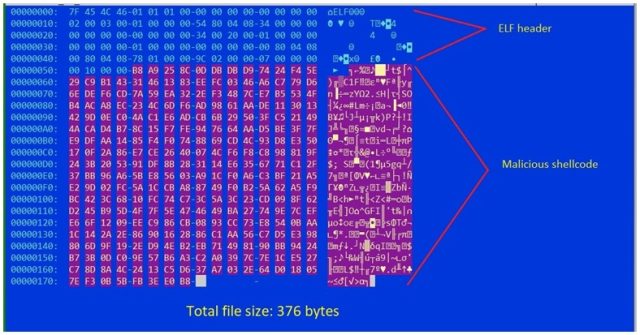
The main dropper is tiny—an executable file of just 376 bytes.
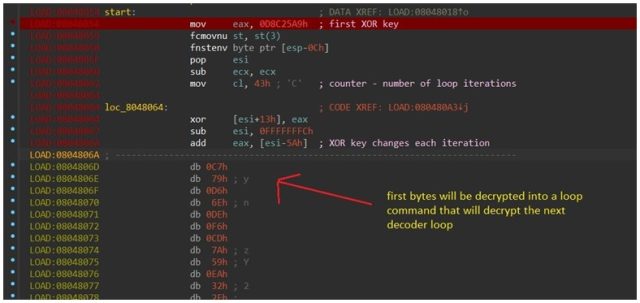
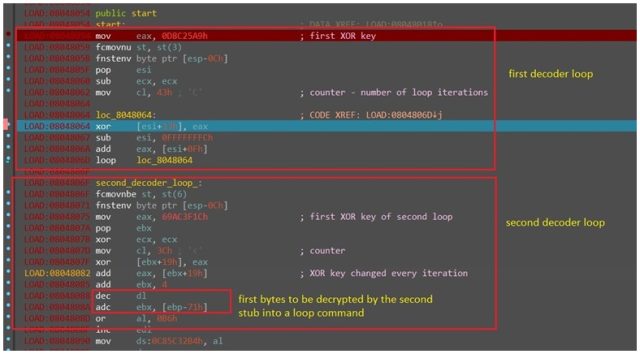
The polymorphic encoding happens courtesy of the Shikata Ga Nai encoder, a Metasploit module that makes it easy to encode the shellcode delivered in Shikitega payloads. The encoding is combined with a multistage infection chain, in which each link responds to a part of the previous one to download and execute the next one.
"Using the encoder, the malware runs through several decode loops, where one loop decodes the next layer, until the final shellcode payload is decoded and executed," Caspi explained. "The encoder stud is generated based on dynamic instruction substitution and dynamic block ordering. In addition, registers are selected dynamically."
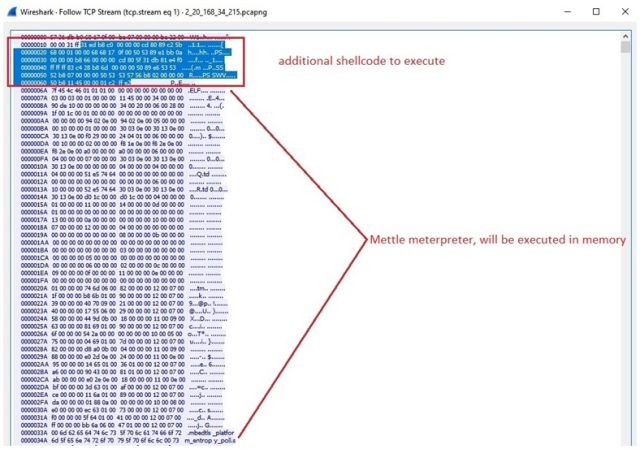
A command server will respond with additional shell commands for the targeted machine to execute, as Caspi documented in the packet capture shown below. The bytes marked in blue are the shell commands that the Shikitega will execute.
The commands and additional files, such as the Mettle package, are automatically executed in memory without being saved to disk. This adds further stealth by making detection through antivirus protection difficult.
To maximize its control over the compromised device, Shikitega exploits two critical escalation of privileges vulnerabilities that give full root access. One bug, tracked as CVE-2021-4034 and colloquially known as PwnKit, lurked in the Linux kernel for 12 years until it was discovered early this year. The other vulnerability is tracked as CVE-2021-3493 and came to light in April 2021. While both vulnerabilities have received patches, the fixes may not be widely installed, particularly on IoT devices.
The post provides file hashes and domains associated with Shikitega that interested parties can use as indicators of a compromise. Given the work the unknown threat actors responsible devoted to the malware's stealth, it wouldn't be surprising if the malware is lurking undetected on some systems.
Source: Ars Technica
- aum, Karlston and Matt
-

 3
3




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.