A new botnet called 'RapperBot' is being used in attacks since mid-June 2022, focusing on brute-forcing its way into Linux SSH servers to establish a foothold on the device.
The researchers show that RapperBot is based on the Mirai trojan but deviates from the the original malware's normal behavior, which is uncontrolled propagation to as many devices as possible.
Instead, RapperBot is more tightly controlled, has limited DDoS capabilities, and its operation appears geared towards initial server access, likely to be used as stepping stones for lateral movement within a network.
Over the past 1.5 months since its discovery, the new botnet used over 3,500 unique IPs worldwide to scan and attempt brute-forcing Linux SSH servers.
Mirai-based, but different
The new botnet was discovered in the wild by threat hunters at Fortinet, who noticed the IoT malware featured some unusual SSH-related strings and decided to investigate further.
RapperBot proved to be a Mirai fork, but with its own command and control (C2) protocol, unique features, and atypical (for a botnet) post-compromise activity.
"Unlike the majority of Mirai variants, which natively brute force Telnet servers using default or weak passwords, RapperBot exclusively scans and attempts to brute force SSH servers configured to accept password authentication," explains the Fortinet report.
"The bulk of the malware code contains an implementation of an SSH 2.0 client that can connect and brute force any SSH server that supports Diffie-Hellmann key exchange with 768-bit or 2048-bit keys and data encryption using AES128-CTR."
The SSH brute-forcing relies on a list of credentials downloaded from the C2 via host-unique TCP requests, while the malware reports back to the C2 when it succeeded.
Fortinet researchers followed the bot and continued to sample new variants, noticing that RapperBot used a self-propagation mechanism via a remote binary downloader, which was removed by the threat actors in mid-July.
The newer variants circulating at that time featured a shell command that replaced the victim's SSH keys with the actor's, essentially establishing persistence that's maintained even after SSH password changes.
Moreover, RapperBot added a system to append the actor's SSH key to the host's "~/.ssh/authorized_keys," which helps maintain access on the server between reboots or even if the malware is found and deleted.
In the most recent samples analyzed by the researchers, the bot adds the root user "suhelper" on the compromised endpoints and creates a Cron job that re-adds the user every hour in case an admin discovers the account and deletes it.
.png)
RapperBot's attack overview (Fortinet)
Also, it's worth noting that the malware authors added extra layers of obfuscation to the strings in later samples, like XOR encoding.
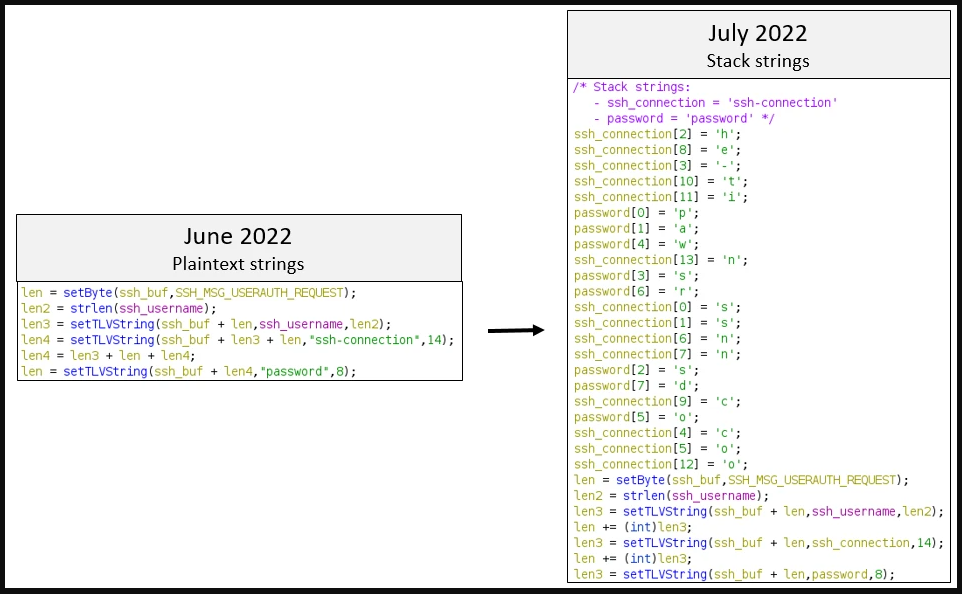
String obfuscation added on later variants (Fortinet)
RapperBot's goal
Most botnets either perform DDoS attacks or engage in coin-mining by hijacking the host's available computational resources, and some do both.
The goal of RapperBot, however, isn't evident, as the authors have kept its DDoS functions limited and even removed and re-introduced them at some point.
Also, the removal of self-propagation and the addition of persistence and detection-avoidance mechanisms indicate that the botnet's operators may be interested in initial access sales to ransomware actors.
Fortinet reports that its analysts saw no additional payloads delivered post-compromise during the monitoring period, so the malware just nests on the infected Linux hosts and sits dormant.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.